Specialists from the Swiss cybersecurity company PRODAFT have published the results of an 18-month study on the PYSA cyber-extortion group.
PYSA (an acronym for “Protect Your System, Amigo”) is the successor to Mespinoza ransomware.
Note: Let me remind you that we also said that Lapsus$ hack group stole the source codes of Microsoft products.
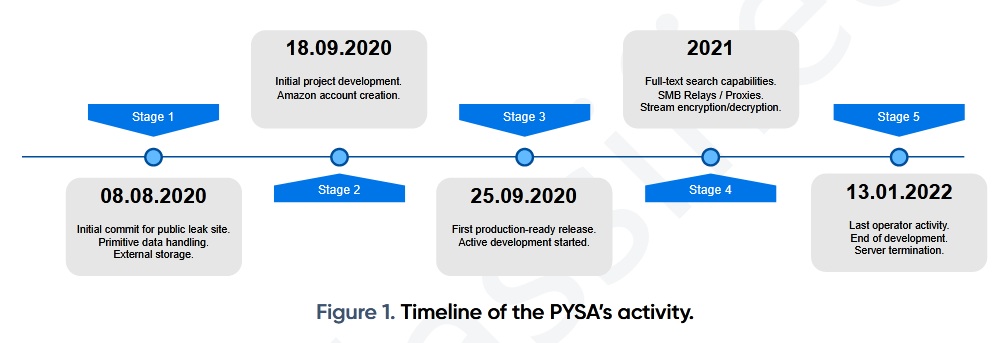
The malware was first discovered in December 2019 and was the fourth most used ransomware in the last quarter of 2021.
Since September 2020, the group has stolen confidential information from 747 victims. In January 2022, her servers were taken down.
According to Intel 471, the majority of victims are in the US (59.2% of all PYSA attacks) and the UK (13.1%). Most often, PYSA attacked government, educational and health organizations.
Like other cyber-ransomware groups, PYSA used a double extortion tactic, releasing the victim’s stolen files if they refused to pay the ransom.
The malware encrypted files by adding the .pysa extension. To decrypt them, a private RSA key was required, which could only be obtained by paying a ransom to the extortionists. Almost 58% of the victims who paid the required amount were able to restore access to their files.
Note: You might also be interested to know what Experts linked BlackCat (ALPHV) ransomware to BlackMatter and DarkSide groups.
PRODAFT specialists managed to find a publicly accessible .git folder managed by PYSA operators and found out the login of one of the project authors – [email protected].
The PYSA operation involved at least 11 accounts, most of which were created on January 8, 2021. 90% of all activity in the malware control panel was accounted for by four accounts – t1, t3, t4 and t5.
The PYSA infrastructure also included docker containers, including public leak servers, databases, and command and control servers, as well as an Amazon S3 cloud for storing encrypted files.