You can witness a PUA:Win32/DNDownloader detection while installing a certain software. This detection refers to a potentially unwanted software that attempts to run unwanted apps along with the “main” installation. In this article, I explain how to remove it and show the dangers related to that threat.
Detection Overview
PUA:Win32/DNDownloader is a heuristic detection of potentially unwanted software associated with the LDPlayer app. This program is a free Windows-based Android emulator developed by the Chinese company XuanZhi. In general, the emulator itself is not harmful, while programs that are installed along with it are.
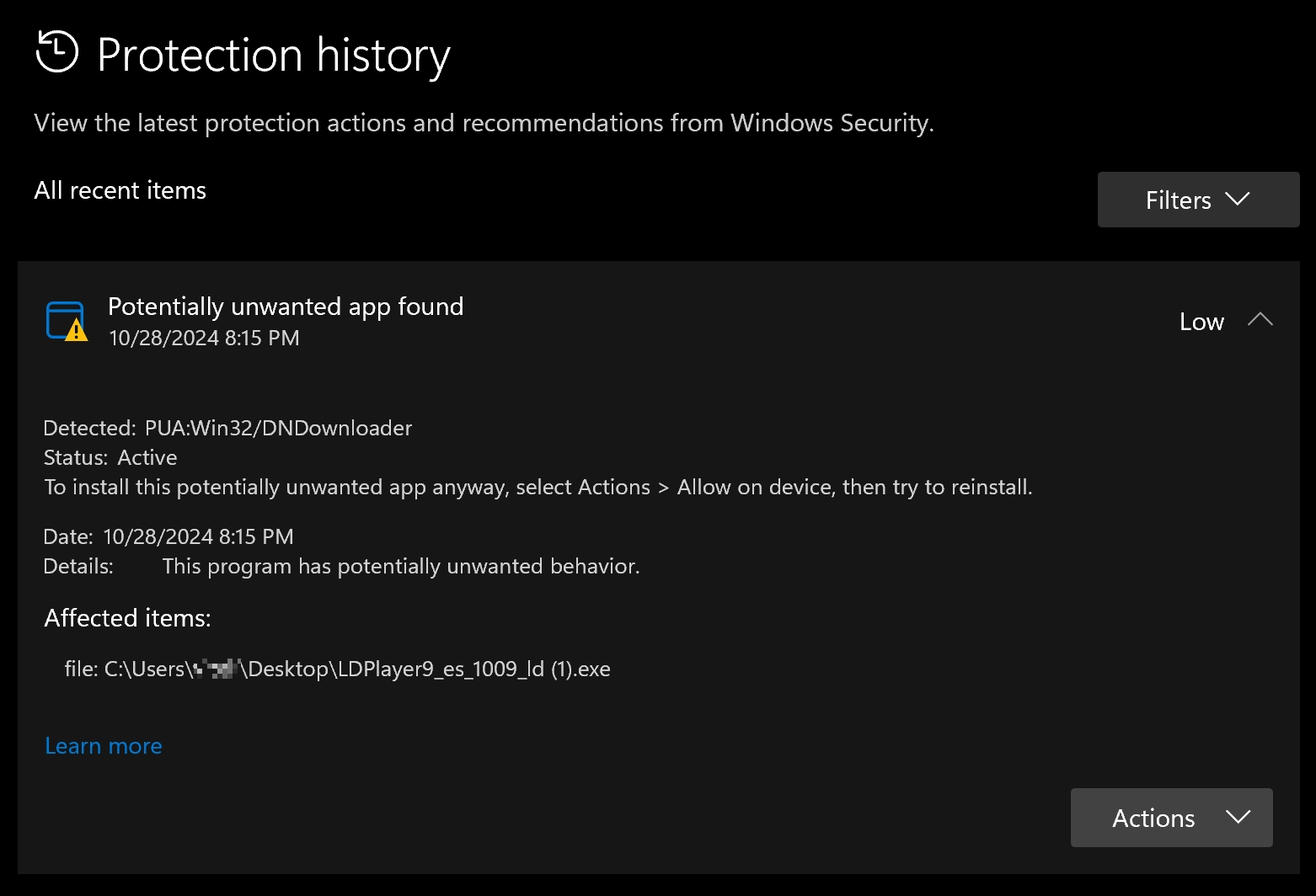
Although LDPlayer has an official website, VirusTotal search results indicate that PUA:Win32/DNDownloader is distributed through malicious websites, often disguised as popular programs, mobile game clients, or cracked mobile apps. Common disguises include popular games and software for some specific tasks.
- Terraria
- Roblox.client
- Brawlstars
- Pokemongo
- Mobile.legends
- Standoff2
- Pixlink.camera
- Instagram.followers.unfollowers
- Minivideos.videodownloader
This is only a small sample of the software under which users have encountered Win32/DNDownloader under the guise of. Additionally, the installation process typically includes prompts to install extra software.
PUA:Win32/DNDownloader Analysis
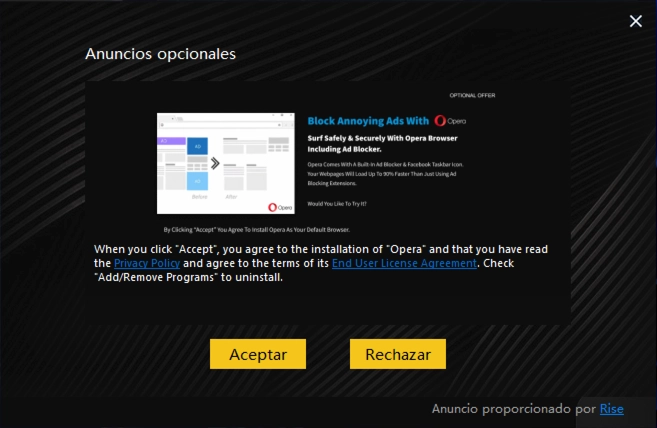
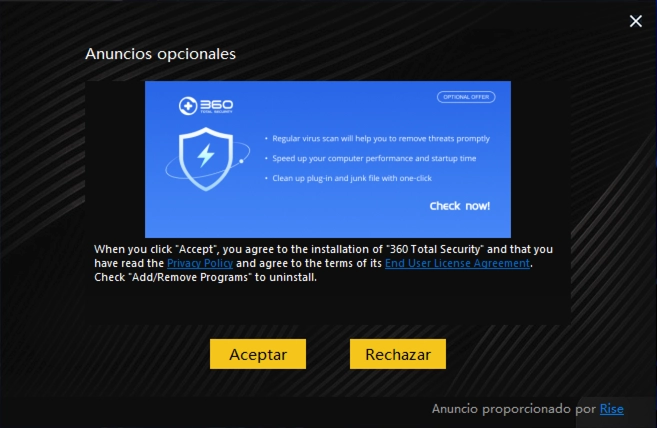
Let’s take a closer look at this unwanted software. The first red flag is that Defender detects it as soon as the installation file is downloaded. This detection is warranted, and here’s why. During installation, PUA:Win32/DNDownloader persistently attempts to install additional bundled software.
The programs included in this bundle are typical for unwanted software of this kind—namely, Opera and 360 Total Security. I’ve encountered other unwanted software that also tries to install these two programs.
Technical Details
Although PUA:Win32/DNDownloader may seem harmless at first glance, its behavior on the system indicates otherwise. The first red flag is that it reads mutexes on the system. The program looks for the Local\__DDDrawCheckExclMode__ mutex and if it does not find it, it creates it and several others:
{EE8B94A3-D811-458B-A446-AF28FA10E845}
MUTEX_LDPLAYER
\Sessions\1\BaseNamedObjects\MUTEX_LDPLAYER
\Sessions\1\BaseNamedObjects\{EE8B94A3-D811-458B-A446-AF28FA10E845}
This behavior is typical of a malicious program, or at least something phony, but not legitimate software. During installation, PUA:Win32/DNDownloader employs techniques like obfuscation to avoid static and dynamic analysis, and it checks for a virtual environment by verifying the following values:
\HARDWARE\DESCRIPTION\System\BIOS
\HARDWARE\DESCRIPTION\System\BIOS\SystemProductName
\HARDWARE\DESCRIPTION\System\BIOS\SystemManufacturer
While a hardware check may be justifiable for optimizing emulator performance, checking for anti-malware software is unusual for standard programs. It checks the following registry keys:
\SOFTWARE\AVAST Software\Avast
\SOFTWARE\Wow6432Node\AVAST Software\Avast
\SOFTWARE\AVG\AV
\SOFTWARE\Wow6432Node\AVG\AV
\SOFTWARE\Avira\Browser
\SOFTWARE\Wow6432Node\Avira\Browser
\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection
\SOFTWARE\WOW6432Node\McAfee
It also modifies certain registry values related to system protection and OneDrive. Otherwise, despite these red flags, LDPlayer performs its intended function.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{E8433B72-5842-4d43-8645-BC2C35960837}.check.101\CheckSetting
HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts\LastUpdate
Is PUA:Win32/DNDownloader False Positive?
Yes, PUA:Win32/DNDownloader can be a false positive detection. Since this is a heuristic detection, it relies on behavior analysis rather than exact signatures. This means that machine learning may occasionally misinterpret certain behaviors. This is also true for the program files it extracts during installation.
For example, on 06/14/2024, some VirusTotal analyses and comments indicated that the files Roboto-Regular.otf and NotoSans-Regular.otf contained DcRat (DarkCrystal RAT). However, upon re-analysis on 10/29/2024, no malware was detected in these files.
Conversely, this detection is associated with the LDPlayer program specifically, which Microsoft Defender flags in most cases upon download. Although the latest version from the official website does not currently trigger a detection, this could potentially change in the future.
How To Ensure Your PC is Clean From PUA:Win32/DNDownloader?
The LDPlayer itself is not malicious; however, the additional software it attempts to install can pose security risks.
To ensure your PC is clean, start by running a full scan with Gridinsoft Anti-Malware. This security tool is designed to detect and remove potentially unwanted applications (PUAs) like DNDownloader, which may infiltrate your system through bundled downloads or malicious ads. After the scan, review and remove any detected items to eliminate potential risks. Finally, activate real-time protection to prevent similar threats from sneaking into your system in the future.