Researchers have discovered a vulnerability called ParseThru — the bug affects Go-based products and can be abused to gain unauthorized access to cloud applications.
Experts from the Israeli company Oxeye, which specializes in the security of cloud applications, noticed the problem. ParseThru is related to how URL parsing is implemented in some Go applications. The implementation creates vulnerabilities that allow attackers to perform malicious actions.
Let me remind you that we also reported that Malware developers increase use of the unusual programming languages, and also that the Trojan Source attack is dangerous for compilers of most programming languages.
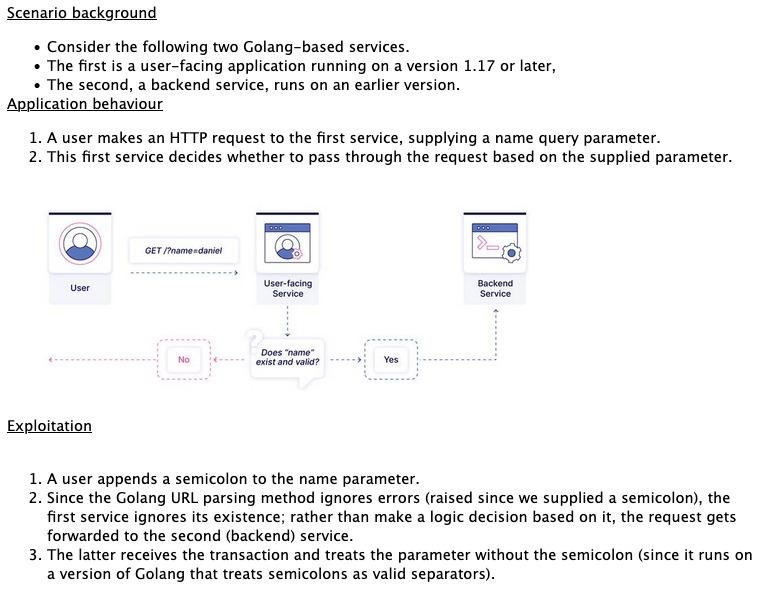
The experts explain that up until version 1.17, Go treated the semicolon in the query part of a URL as a valid delimiter (for example: example.com?a=1;b=2&c=3), and after that version, the behavior was changed to display an error when finding a query string containing a semicolon.
However, researchers have found that if a user application runs on Go 1.17 or later, and its associated backend runs on an earlier version of Go, an attacker can smuggling requests with query parameters that would normally be rejected. That is, the idea is to send specially prepared requests containing a semicolon, which will be ignored by the Golang user API, but will be processed by the internal service.
Oxeye analysts managed to find several open-source projects that are vulnerable to ParseThru. These include Skipper HTTP Router and Reverse Proxy, Traefik HTTP Reverse Proxy and Load Balancer, and the CNCF Harbor Project, designed to ensure that container images are secure and trusted. The researchers cite Harbor as an example: in its case, the vulnerability will allow attackers to read private Docker images with limited access, which under normal circumstances would be inaccessible to them.
Oxeye has already communicated its findings to the developers of the affected applications, and they have released fixes.