Nnice ransomware is a malware strain that aims at encrypting user files and demanding ransom payment for their decryption. Detected on January 14, 2025, it presumably targets individuals and small businesses. Upon the encryption, it changes file extensions by adding the .nnice extension to the end, i.e. file.txt becomes file.txt.nnice, picture.jpeg – picture.jpeg.nnice, and so on.
On top of changes to the files, the malware changes desktop wallpaper and spawns a ransom note that contains the details about how to pay the money and contact the hacker afterwards. It also opens the ransom note to the full screen so the user won’t miss or ignore it.
Ransom Note Overview
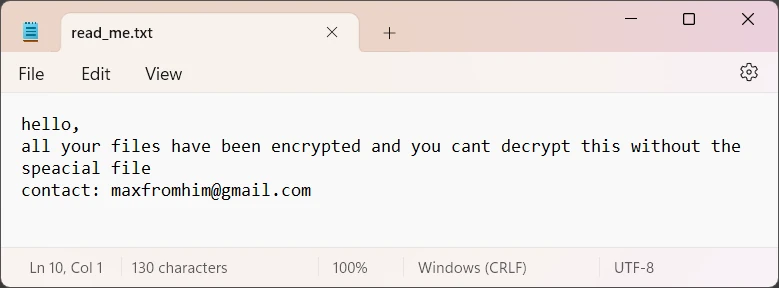
Ransom note of Nnice ransomware is exceptionally short, consisting of only one sentence and a contact email address – [email protected]. All it says is that all the files were encrypted and it is impossible to get them back “without the special file”. It is unclear what special file it is about, as typically the decryption requires a special tool.
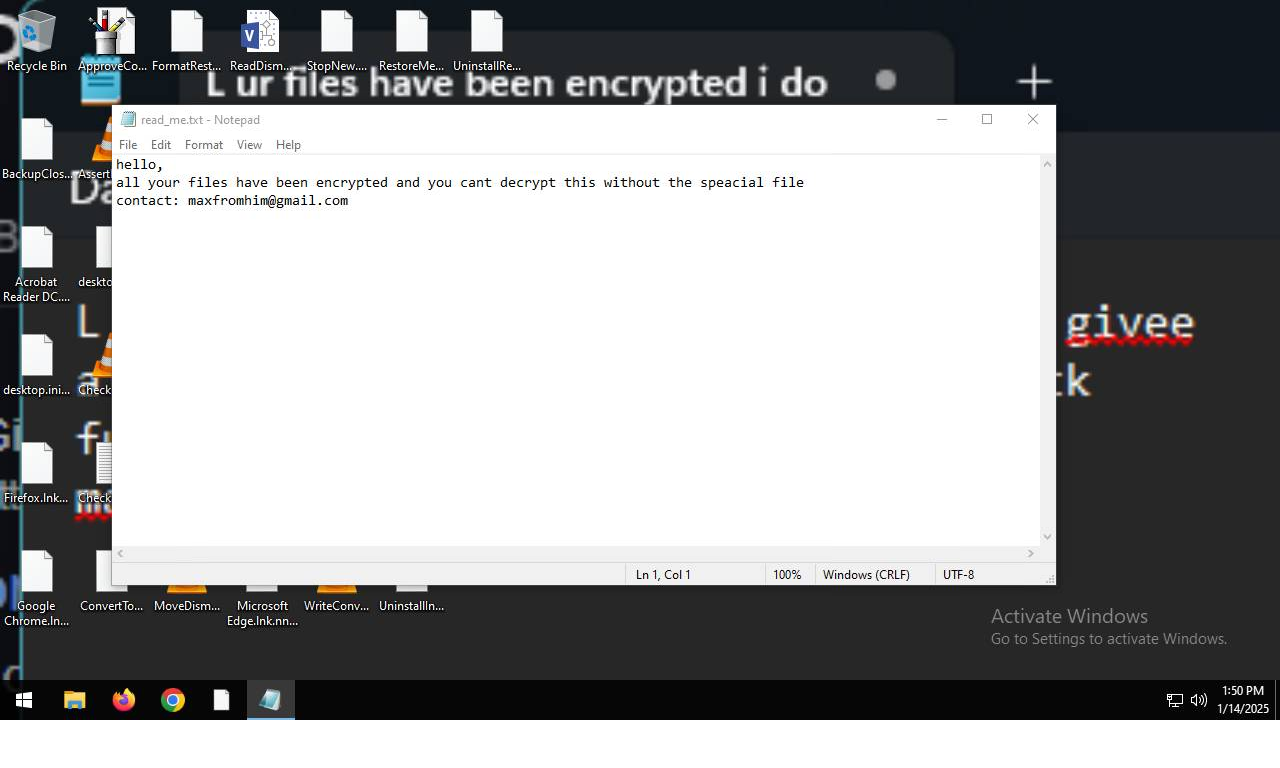
The same information is present on the wallpaper that the malware sets up after finishing the encryption. It only differs in wording and the promise to give the files back. There are no mentions of the specific sum that the hacker demands, meaning that it is up to discussion.
I strongly encourage you against paying anything to the fraud. There is no guarantee that they will give you the decryptor tool, and not simply ignore you or ask even a bigger sum for some unrelated reason. Also, by paying the ransom, you in fact fund the further malicious activity, so the attacks will happen more and more often.
Nnice Ransomware Analysis
The technical side of Nnice ransomware is worth your attention, as it gives important hints on what you need to do after the attack. It is based off of Chaos ransomware, a malware strain that has a special builder app, which simplifies modifying the behavior and features of the virus.
Upon execution, Nnice ransomware checks system location and some of the configurations to ensure it is not running on a virtual machine. Then, it disables Volume Shadow Copies, a built-in backup system that could have helped the user with reverting the system state to pre-encryption.
For the encryption, it uses AES/RSA encryption algorithms, and applies encryption only to files smaller than 2 megabytes. This helps a lot when it comes to file decryption, I will explain why later in this article. After finishing the encryption, it modifies the registry key to change the wallpaper, and opens its ransom note in the Notepad app.
One important and worrying detail of the ransomware is the data stealing module that is built into itvo. Following the encryption process, it accesses user credentials stored in browser files. This is a tactic typical for spyware and infostealers; they dump logins and passwords into a separate text file and send it to the command server.
How to Remove Nnice Virus?
A step that I heavily recommend you to do before proceeding with data recovery is to remove the malware. After all the action, the ransomware remains active and will encrypt any recovered files that appear in the system.
To remove Nnice ransomware, I recommend using GridinSoft Anti-Malware. Its multi-component detection system will find even the most modern malware samples, no matter how well they hide in the system. Download it by clicking the banner below and run a Full scan, to check the most remote areas of your computer.
After the removal, I will recommend you to reset all the passwords that you have used in the attacked system. This will ensure that the hacker won’t have access to your online accounts.
How to Recover the files?
The encryption algorithm used by this ransomware is quite strong, so brute forcing the decryption key is a futile idea. Yet the way the malware handles the encryption allows for a trick to circumvent the decryption entirely and get the files back for free.
Files over 2 megabytes are not encrypted. Any media files (photos, videos, music) are likely left untouched; malware does this to save system power and avoid attracting too much attention to its activity. Thus, all you have to do to access them is delete the .nnice extension at the end. After that, you should be able to access the files as usual.
For smaller files, unfortunately, the simple way around is not available. You can try seeking for unencrypted versions of files in cloud backups, conversations in messengers, emails and so on. It is possible for law enforcement to arrest the hackers and retrieve all the decryption keys. Malware analysts, at the same time, can elaborate a functioning decryptor that will restore the files for free.





