ekoia experts report that a new infostealer, Stealc, has appeared on the darknet, and is gaining popularity among criminals due to aggressive advertising and similarities to malware such as Vidar, Raccoon, Mars, and Redline.
Let me remind you that we also wrote that Djvu Ransomware Spreads via Discord, Carrying RedLine Stealer, and also that NetSupport and Raccoon Stealer malware spreads masked as Cloudflare warnings.
Also information security specialists reported that Raccoon malware steals data from 60 different applications.
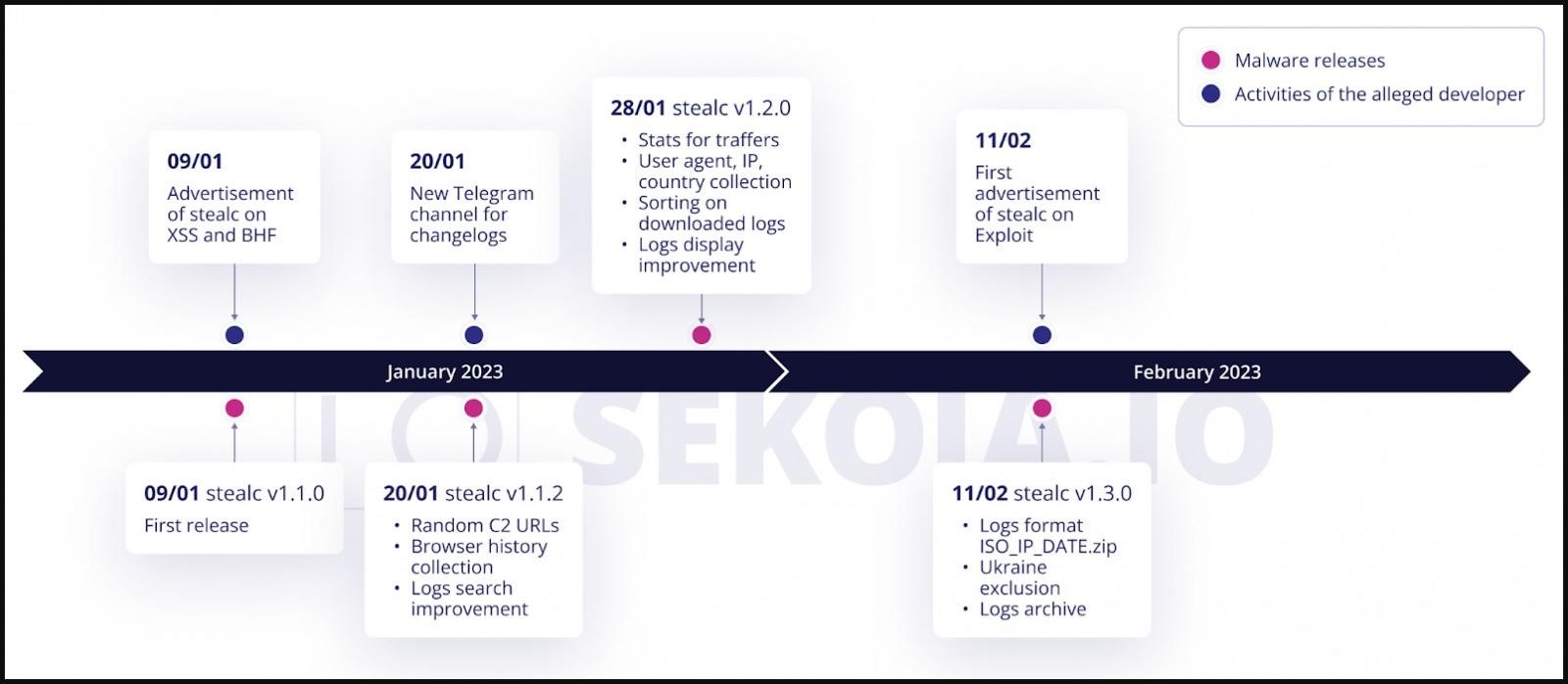
For the first time, analysts noticed the advertisement of the new malware back in January, and in February it began to actively gain popularity.
On hack forums and Telegram channels, Stealc is advertised by someone under the nickname Plymouth. He says that the malware is a “non-resident stealer with flexible settings and a convenient admin panel.”
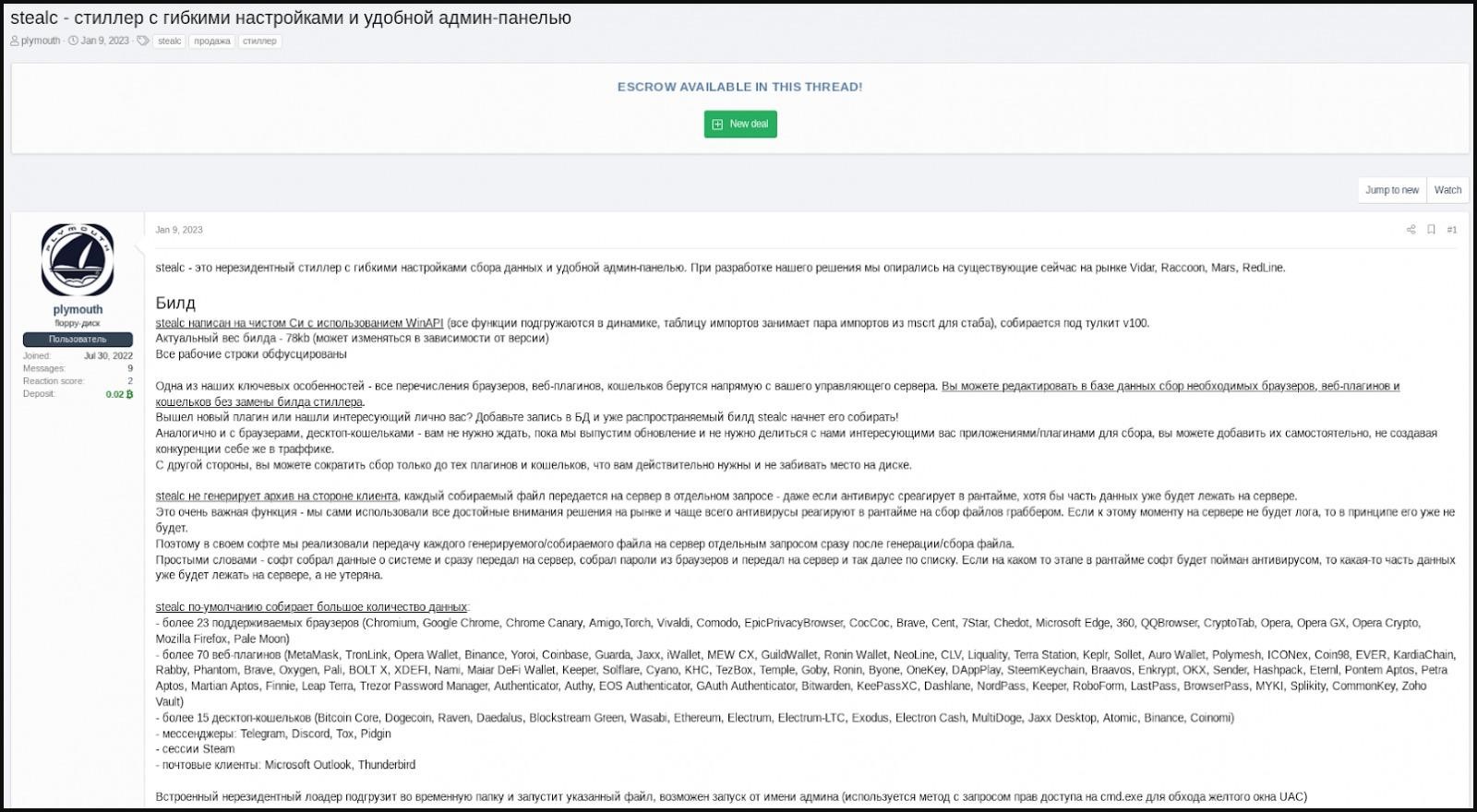
Advertisement Stealc
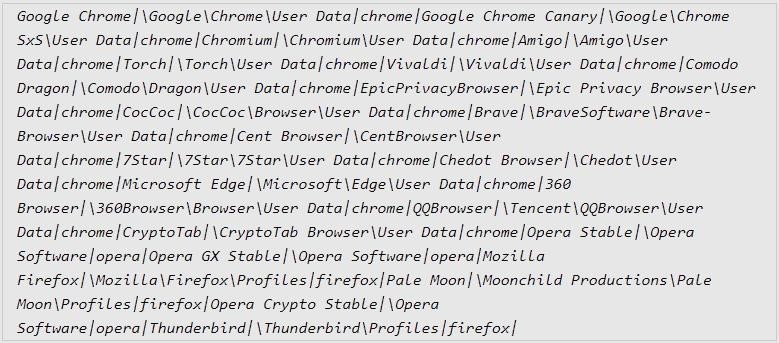
In addition to the usual targeting of data from browsers, extensions and cryptocurrency wallets for such malware (the malware targets 22 browsers, 75 plugins and 25 desktop wallets), Stealc can also be configured to capture certain types of files that the malware operator wants to steal.
Configuration Instructions for Browser Attacks
The advertisement notes that when developing Stealc, its authors relied on solutions already existing “on the market”, including Vidar, Raccoon, Mars and Redline.
Sekoia analysts noticed that Stealc, Vidar, Raccoon, and Mars have in common that they all load legitimate third-party DLLs (eg sqlite3.dll, nss3.dll) to steal sensitive data. The researchers also say that the organization of communication with the control server of one of the samples of the new stealer they analyzed is similar to Vidar and Raccoon.
In total, the researchers identified more than 40 Stealc C&C servers and several dozen malware samples. According to them, this indicates that the new malware has aroused considerable interest among the cybercriminal community.
Malware development
One of Stealc’s distribution methods that researchers have already discovered is YouTube videos that describe how to install the cracked software and contain links to download sites. In such programs, a stealer is built in, which starts working and communicates with the control server after the installer is launched.

Site distributing stealer
According to experts, hacker clients with access to the Stealc administration panel can generate new stealer samples, and this increases the chances of the malware leaking and making it available to a wider audience in the future.




