A new strain of ransomware, named Embargo, written in Rust, recently surfaced along with its Darknet infrastructure. It uses double extortion tactics and is very reminiscent of a recently seized ALPHV group. The novice gang already boasts of 4 victims from different countries.
Embargo Ransomware Discovered, Coded in Rust
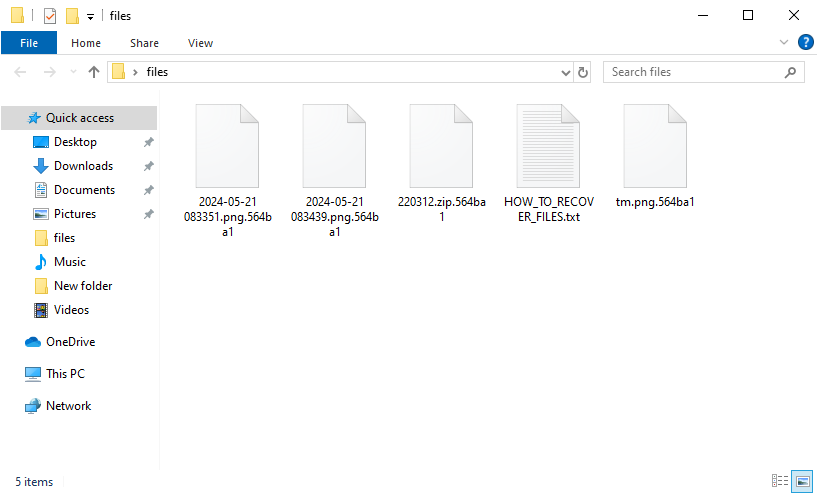
In May 2024, cybersecurity researchers discovered a new ransomware group called Embargo. It uses the Rust language, known for its security and parallelism capabilities. The Embargo has fast encryption that uses ChaCha20 and Curve25519 to lock victims’ files, making a recovery without paying a ransom nearly impossible. After encryption, the ransomware adds a random 6-symbol extension to the encrypted files. Discovered variants used the .564ba1 string, though it would likely change in future. The use of the Rust language indicates the growing trend of adopting modern languages to bypass traditional security solutions.
The creators of Embargo use a now-classic double extortion method. This means that they first demand a ransom to unlock encrypted files. After paying the ransom, they threaten to publish sensitive data online unless the victim pays the “for silence” again. The average ransom amount from Embargo is around $1 million (15 BTC).
Attack vector and infection process
Typically, the attack vector starts with phishing emails containing malicious attachments or links. After the user clicks on them, the payload is downloaded and executed on the victim’s system. In brief, Embargo seeks out specific instructions to control its actions when it runs. It targets directories R:\backups\, \\files01\finance, \\10.0.3.2\D$\Accounting, creates a unique mutex identifier and clears the recycle bin to prevent file recovery.
Additionally, it disables Windows recovery options by command C:\\Windows\\System32\\cmd.exe /q /c bcdedit /set {default} recoveryenabled no, stops specific running processes and system services, and identifies all connected drives and network resources to encrypt files. Embargo uses strong encryption methods, such as ChaCha20 and Curve, to securely lock files and leaves a ransom note named HOW_TO_RECOVER_FILES.txt in each folder it encrypts. Thus, the ransomware encrypts files to make them inaccessible without a decryption key, which TAs offer in exchange for a ransom payment.
ALPHV/BlackCat similarities
One of the most essential aspects of Embargo is its operational similarities to ALPHV/BlackCat. This notorious ransomware group recently ceased operations in what looked like an exit scam. Analysts note several things in common, that can point at this malware being a reborn variant of ALPHV ransomware.
- Codebase and infrastructure. A detailed analysis of Embargo’s code revealed similarities with ALPHV/BlackCat’s code solutions. In particular, it resembles a test sample of ALPHV ransomware written in Rust, that hackers released back in 2022. New sample, although visually different, repeats the structure and syntax of the older one.
- Darknet site design. As most of ransomware group, Embargo operates a Darknet site for negotiating and leaking data. The design of this page, however, is strikingly similar to what BlackCat gang used to have. Evidence of copying is also present in the HTML code of the page.




