Microsoft developers are going to block some Excel add-in (.XLL) files for Microsoft 365. The new measures will include automatic blocking of such files downloaded from the Internet.
Let me remind you that we also wrote that Hackers use the .NET library for creating malicious Excel files. Moreover, the media noted that For security reasons, Microsoft disabled macros in Excel 4.0 (XLM).
More recently, researchers have warned that after Microsoft began blocking VBA macros in Office documents downloaded from the Internet (marked Mark Of The Web), attackers had to rethink their attack chains.
Now hackers are increasingly using XLL files in phishing campaigns, disguising them as important documents, promotions, and so on.
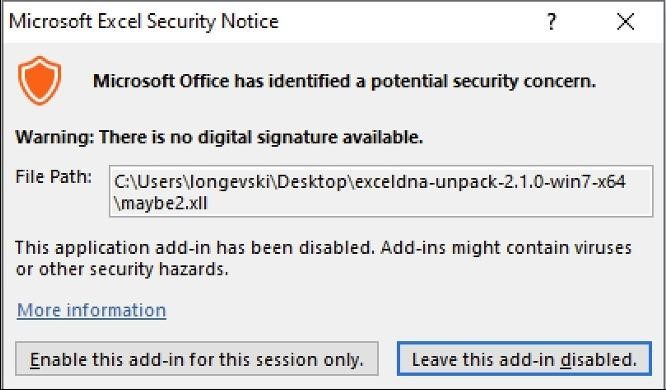
Although Excel warns about the potential dangers of XLLs, these warnings are usually overlooked by users.
Although the recently developed VBA macro blocking only covers the latest versions of Access, Excel, PowerPoint, Visio, and Word, attackers have already started experimenting with alternative ways to infect and deploy malware.
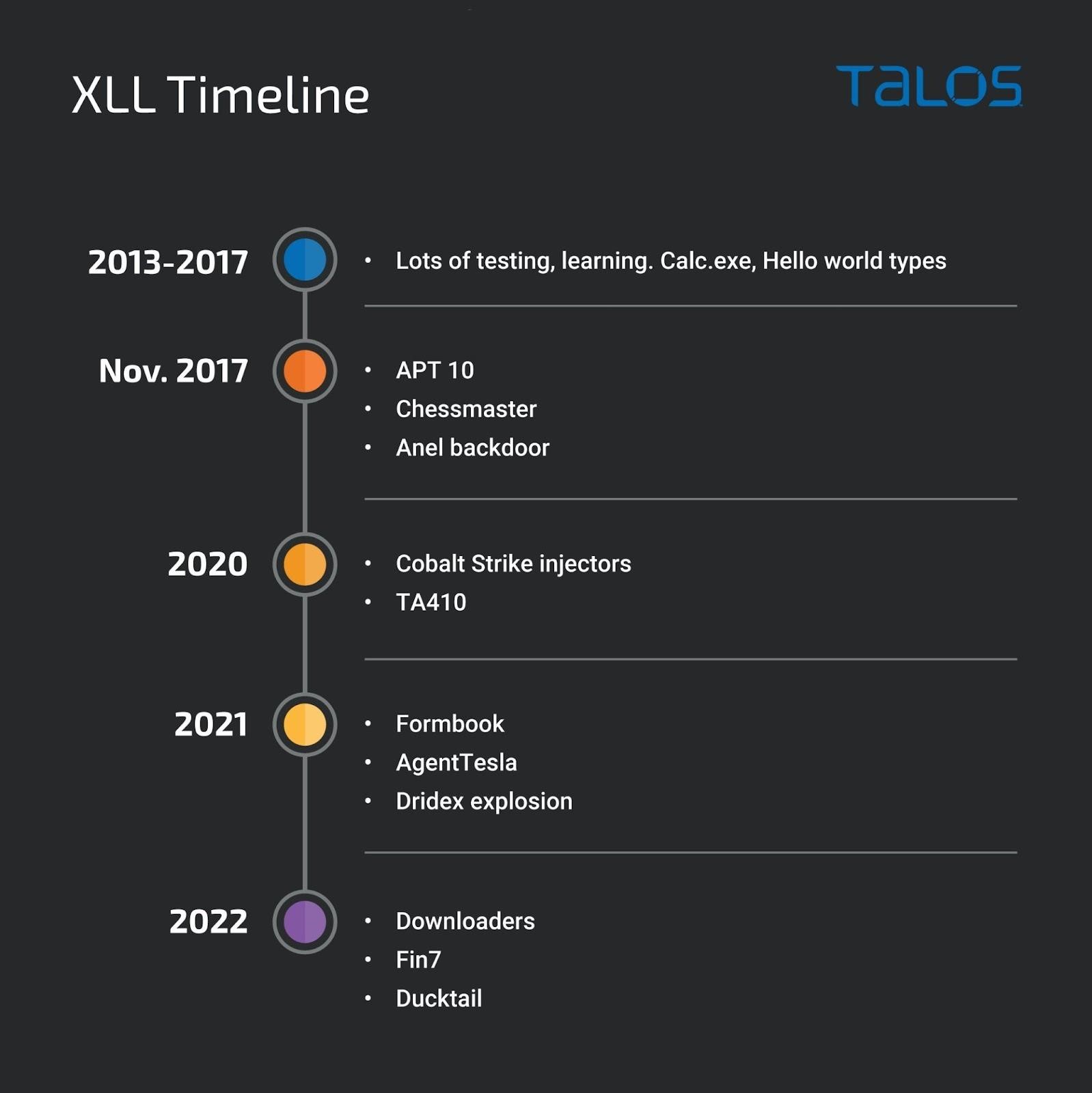
As Cisco Talos researchers reported, one such “innovation” was the use of XLL files, which Microsoft describes as “a kind of DLL file” that are used to extend the functionality of Microsoft Excel.
Because XLL files are executable, attackers can use them to run malicious code. Even last year, experts warned that XLL files were already being abused by the Chinese hack groups APT10 and TA410 (and they started back in 2017); the Russian-speaking group FIN7, which began using add-on files in their campaigns last summer; famous Dridex malware loader and FormBook loader; as well as other major malware families, including AgentTesla, Ransomware Stop, Vidar, Buer Loader, Nanocore, IceID, Arkei, AsyncRat, BazarLoader, and so on.
The company said that the new functionality will become generally available worldwide in March 2023 and will work for users in the Current, Monthly Enterprise and Semi-Annual Enterprise channels.