Recent UK NCA publications uncover the identities of 16 cybercrime actors that belong to Evil Corp/REvil and LockBit ransomware groups. Some of them were detained synchronously with the news, with others getting sanctioned by the US and UK governments. The newsletter also contains details about the interconnections between two gangs and Russian government agencies.
NCA Unveils Identities of Lockbit, REvil Cybercriminals
New report from the UK National Crime Agency (NCA) shows the further investigation on several most notorious cybercrime groups in the world, namely REvil (a.k.a Evil Corp) and LockBit. It goes on since 2019, when the former started its activity, and had several large announcements earlier this year. This time, however, they went deeper into the structure of both organizations, which appear to be interconnected. Moreover, some of the actors appear to be related not only in their trade, but also in family matters.
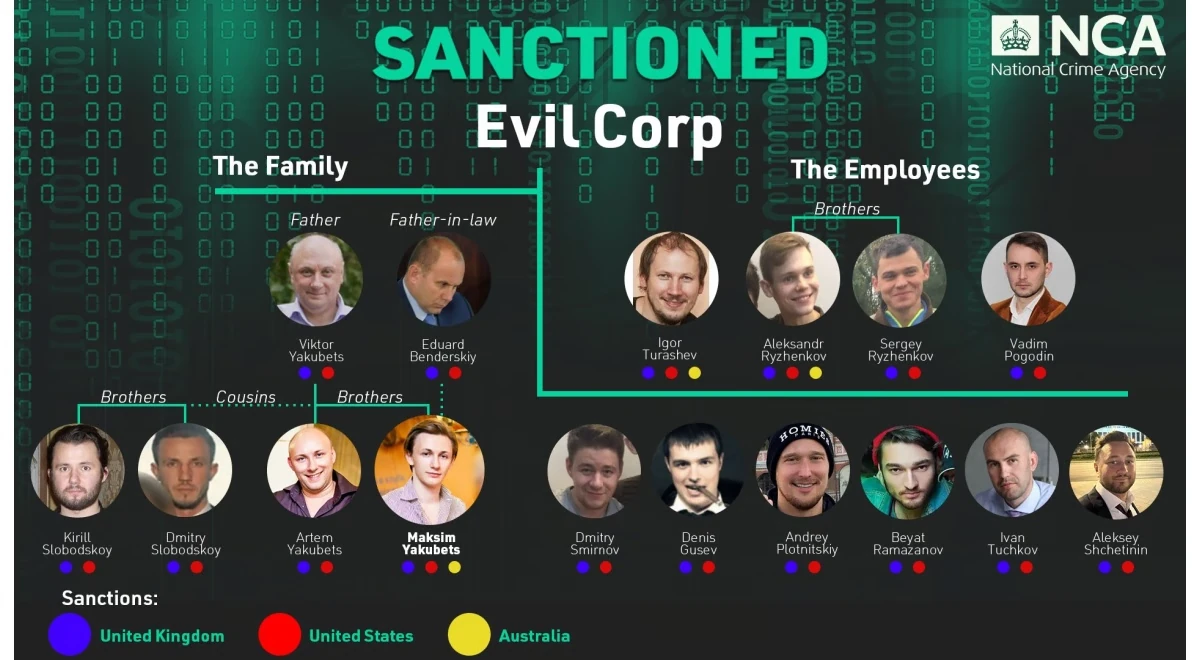
According to the NCA investigation report, the key figure of REvil gang, Maksim Yakubets, has got quite a bit of his family into the shady business. His father, Viktor Yakubets, has a significant background in money laundering, and likely works for the very same direction in Evil Corp. Same is true to his brother Artem and cousins Kirill and Dmitry. Maksim’s father-in-law, Eduard Bendersky, has ties in the highest offices of the Russian government, and is likely responsible for providing the cybercrime gang with immunity against any law enforcement activity.
An interesting detail surfaced about one of LockBit affiliates, who was unmasked back in February 2024, under the course of Operation Cronos. Aleksandr Ryzhenkov, known for working for LockBit, is also named as a right hand of REvil’s chief Maksim Yakubets. There are a lot of rumors about the white-and-red gang being an offspring of the Evil Corp, and this is yet another clue for this. Still, it is not uncommon to see hackers working for several gangs simultaneously, or them sharing their staff to their colleagues.

Arrests of LockBit Gang Members
The report was not only about the announcement of successful investigation results, but also disclosing several arrests and infrastructure takedowns. In August 2024, law enforcement detained 2 affiliates, presumably in the US. In France, a suspected developer of the group’s ransomware was captured, while Spanish police managed to take over quite a lot of server infrastructure and handcuff a person responsible for its handling.
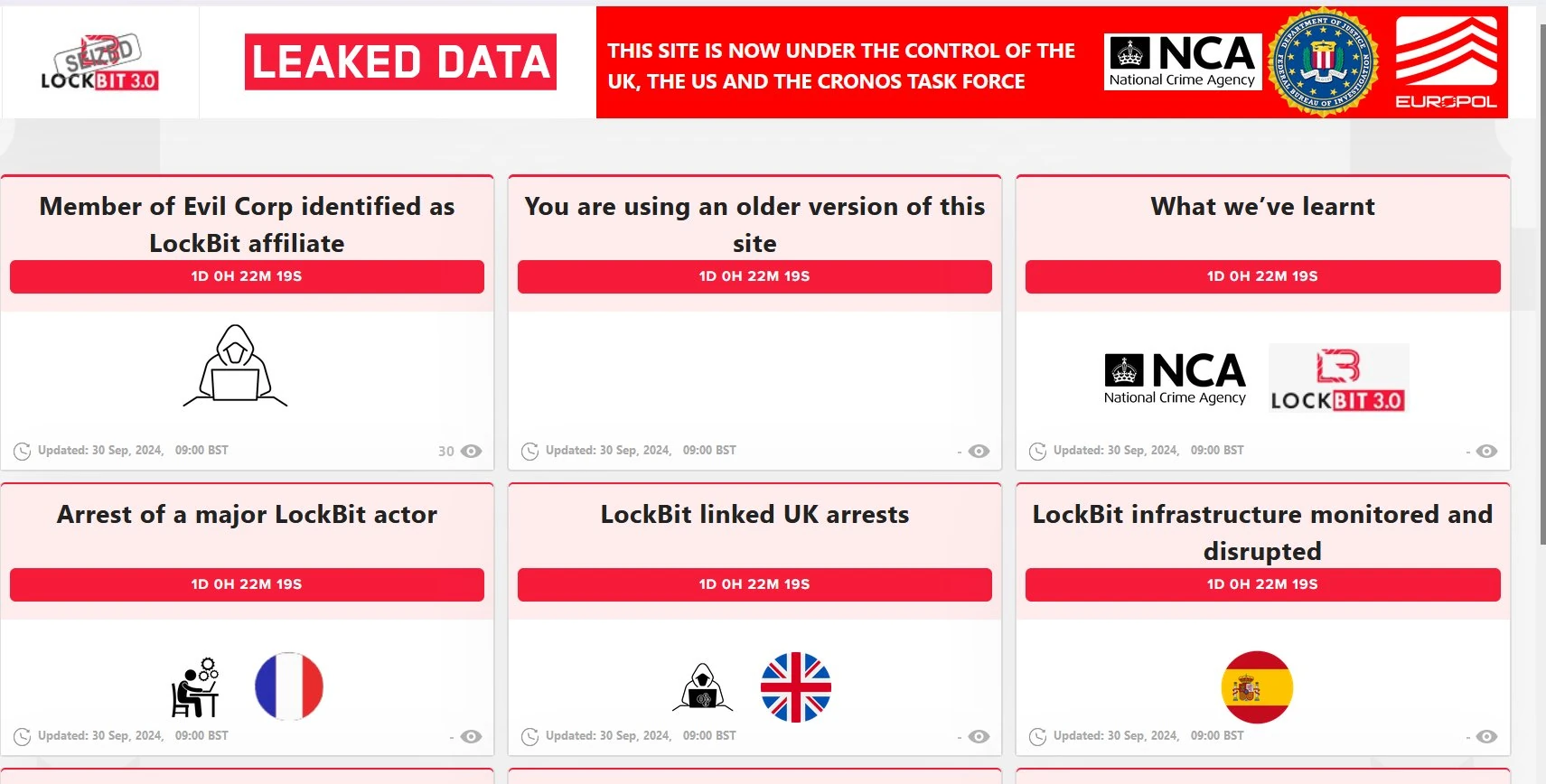
It may look strange that only LockBit members are getting caught, while REvil remains almost untouched. Well, the infamous LockBitSupp stated several times that “LockBit group is an international organization”, and that claim appears to be true. REvil, on the other hand, has most of their members located in Russia, who ceased most of anti-cybercrime cooperation with the US and European law enforcement agencies. The group also ceased their activity, so there are much less possibilities to get any new data about them. Moreover, they are protected with the aforementioned immunity from any internal investigation, meaning that it is particularly hard to do anything about them.
Still, that does not mean they are invulnerable and can’t be punished in any other way. Throughout the quite long investigation process, NCA was sharing data with US and UK Treasuries, so they can locate the hackers’ belongings under their jurisdiction. That resulted in all the tops of REvil getting under sanctions in the US, UK and Australia. With LockBit though it is a bit more complicated: not much is known about their tops, except for LockBitSupp a.k.a Dmitri Yurievich Khoroshev. Affiliates, meanwhile, are getting arrested, so the sanctions are, well, pretty straightforward.
Will This go Further?
Throughout the last 2 years, law enforcements definitely changed their approach in the combat against cybercrime gangs. Instead of attempts to capture cybercrime actors, they rather opt for disrupting infrastructure and trying to get as much information as possible from such actions. Sure, that does not stop the cybercriminals, but make them pause for several months, or even longer. For instance, QakBot, an infamous backdoor/loader malware still struggles one year after the takedown. So yes, hackers are still free, but they are about to start everything from scratch.
Another possible vector of further law enforcement activity is actions against Darknet infrastructure. Forums, specialized data selling platforms and ones that offer various hacking-related services are a backbone of hiring new staff, getting access to corporate networks and selling leaked information. This also happened in the past, with takeovers of BreachForums, RaidForum and numerous services that offered infrastructure for selling and using leaked data. Without such an important pillar, the activity becomes scattered, with cooperation becoming much more problematic.





