Researchers have discovered that the young ransomware group Bl00Dy is already using in its attacks the LockBit builder, which leaked to the network last week.
Let me remind you that the builder of the well-known encryptor LockBit was published in the public domain about a week ago. It is assumed that the LockBit 3.0 builder was leaked to the network by a disgruntled developer or competitor of the one-dimensional grouping.
At the time, experts warned that regardless of the source of this leak, publishing the builder online would likely increase the number of ransomware attacks. After all, the builder allows criminals to quickly create the executable files needed to launch their own extortion campaign (including the ransomware itself, the decryptor, as well as specialized tools).
Unfortunately, the experts were not mistaken in their predictions: it became known that the builder of LockBit 3.0 had already been adopted by the extortionate group Bl00Dy.
Bl00Dy was first seen in May 2022 when it attacked a network of medical and dental offices in New York. Like other ransomware groups, Bl00Dy hacks into the victim’s network, steals data, and then encrypts the devices. The only difference with other ransomware lies in the fact that instead of a “leak site” in Tor, these hackers use the Telegram channel to publish victims’ data.
In addition, back in the spring, security researchers noted that the criminals behind Bl00Dy did not develop their ransomware themselves. Instead, they created ransomware using leaked builders and source code from other ransomware, including Babuk and Conti.

At the beginning of this week, information security specialist Vladislav Radetsky published a report on the new Bl00Dy encryptor, which was used to attack an unnamed Ukrainian company. However, it was unclear what the Bl00Dy malware is based on in this case – on Conti, as it happened earlier, or on the LockBit.
Shortly after the release of this report, the MalwareHunterTeam security expert confirmed that the ransomware was indeed built on the basis of the recently leaked LockBit 3.0 builder. Intezer’s analysis also revealed many overlaps between Bl00dy and LockBit 3.0 code.
The publication Bleeping Computer, which also studied the new ransomware, notes some of the limitations that Bl00Dy participants encountered. For example, in past campaigns, attackers added the .bl00dy extension to encrypted files. However, in the LockBit 3.0 builder, this parameter is not configurable, and attackers had to use ready-made extensions.
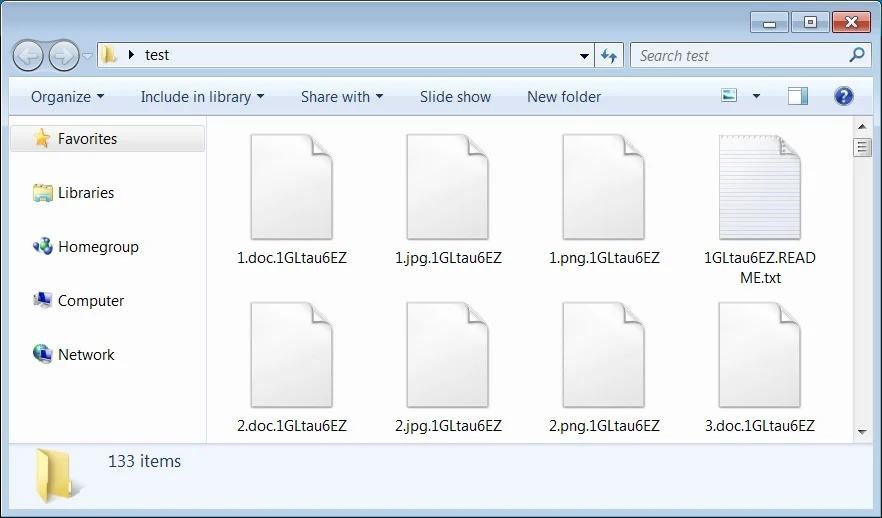
As for the ransom note, the attackers were able to customize it to contain their own text and contact information.


![Lazarus Hackers Attack MacOS Users by impersonating Crypto[.]com 5 Lazarus attack macOS users](https://gridinsoft.com/blogs/wp-content/uploads/2022/09/Lazarus-attack-macOS-users-150x150.jpg)

