FakeUpdate, a campaign of fake browser updates that pops up during regular Internet browsing, now targets users from France. The final target of the campaign appears to be deployment of WarmCookie backdoor, a recently discovered malware specimen.
FakeUpdate Spreads WarmCookie as Chrome, Edge Updates
Researchers at Gen Threat Labs have uncovered a campaign spreading the WarmCookie backdoor. The core of the is a previously known FakeUpdate, that involves tricking victims into downloading and running a fake web browser update. As I’ve mentioned in the introduction, these attacks are currently targeting users in France. Besides popular browsers like Google Chrome, Mozilla Firefox, and Microsoft Edge, the campaign also offers “updates” for apps like Java, VMware Workstation, Proton VPN, and WebEx. To do this, attackers hack or create websites that display fake web browser update requests. And, sure enough, as one follows the demand, they receive a malicious program under the guise of browser update.

In fact, FakeUpdate campaign is not entirely new, as previous similar campaigns have circulated online. It is also not new for WarmCookie to use tricky and unusual spreading schemes. Researchers previously encountered this backdoor being distributed under the guise of job offers. This time, however, aside from the new distribution method, there is an updated version of WarmCookie. It can now enable data and file theft, device profiling, program enumeration (through the Windows Registry), arbitrary command execution via CMD, screenshot capture, and additional malware installation capabilities.
FakeUpdate France Campaign Details
In brief, the FakeUpdate site is designed to mimic the real one, featuring a pretty convincing URL. As of the time of writing, the site edgeupgrade[.]com was still operational. Clicking the Update button downloads an installation file “Install_x64.exe”, which is the WarmCookie backdoor. According to the researchers’ report, once launched, the malware performs standard checks for a virtual environment. If no virtual environment is detected, it gathers the system fingerprint and sends it to the attackers’ C2 server.
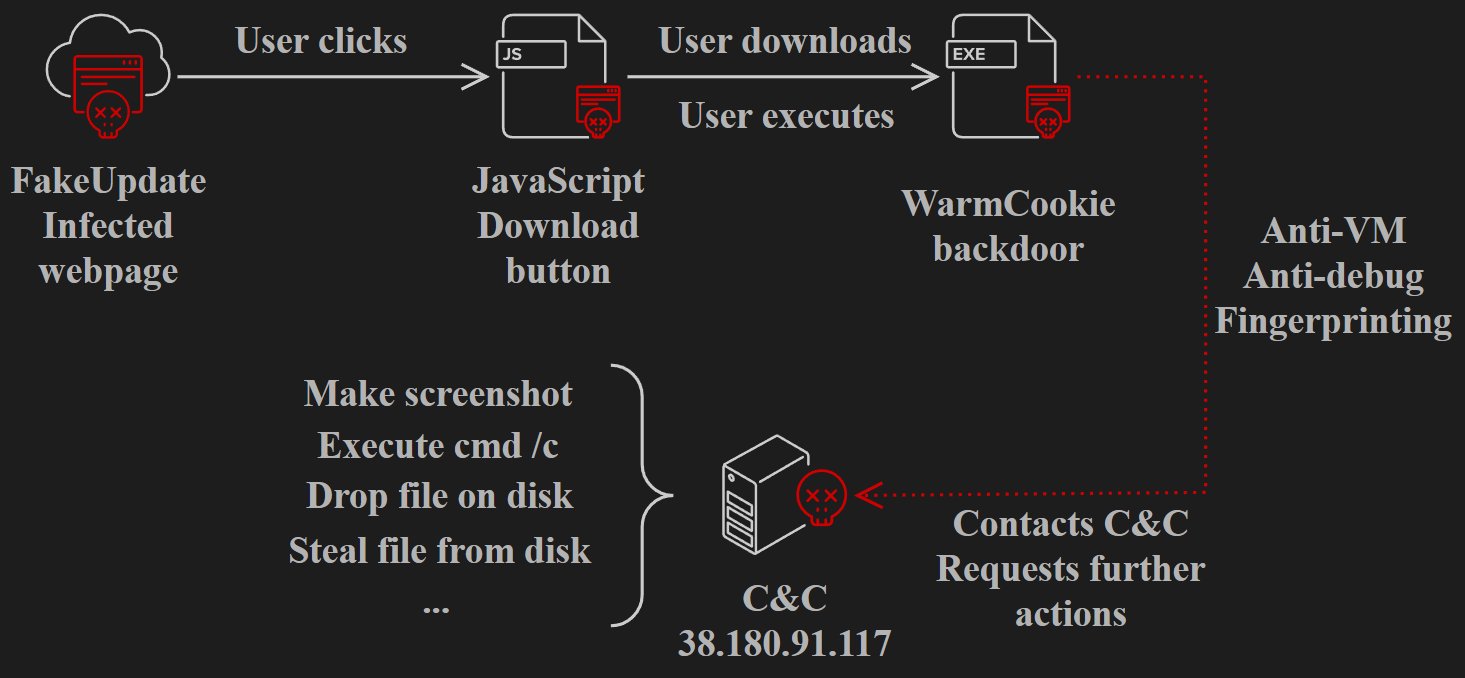
As previously mentioned, this backdoor provides attackers with unrestricted access to the compromised system. The latest campaign observed by Gen Threat Labs shows WarmCookie has been upgraded with new capabilities. Among others, running DLLs from the temp folder and transmitting the output, alongside the ability to transfer and execute EXE and PowerShell files. Beyond basic data theft, attackers can also deliver payloads like ransomware.
Regarding legitimate web browser updates, all modern browsers on Windows are now automatically updated. This eliminates the need to download any installation files manually – the user may only need to restart the browser.
How to Stay Protected?
As this campaign has several distinct milestones in user interaction, the key to avoiding this threat will be in proactive counteraction. First and most effective solution is to remain vigilant while browsing the web. Even with highly convincing phishing campaigns, exercise caution when prompted to download or update software. Instead, always visit the official website of the application you intend to update.
Another proactive option is to use advanced anti-malware software with built-in Internet security. If the first precaution is overlooked, anti-malware software will block access to phishing pages. GridinSoft Anti-Malware offers advanced protection, including an Internet Security feature, making it a strong option to consider.