Hosting providers and the French CERT warn that more than 3,200 VMware ESXi servers were compromised by the new ESXiArgs ransomware last weekend as part of a massive hacking campaign.
Let me remind you that we also wrote that New RedAlert Ransomware Targets Windows and Linux VMware ESXi Servers, and also that Information Security Experts Told About The Linux Malware Symbiote That Is Almost Undetectable.
Also information security specialists said that Critical Bug in VMware Products Is Used to Install Miners and Ransomware.
Attackers exploit a two-year-old vulnerability (CVE-2021-21974) that allows them to execute remote commands on vulnerable servers via OpenSLP (port 427).
This vulnerability is related to a dynamic memory overflow in OpenSLP, which can be exploited by unauthenticated attackers in simple and effective attacks. CVE-2021-21974 affects the following systems: ESXi version 7.x (up to ESXi70U1c-17325551), ESXi version 6.7.x (up to ESXi670-202102401-SG), and ESXi version 6.5.x (up to ESXi650-202102101-SG).
It is worth noting that the exploit for this issue has been available since the spring of 2021 and appeared shortly after the bug was disclosed. It is completely unclear why the attackers started exploiting this bug only now.
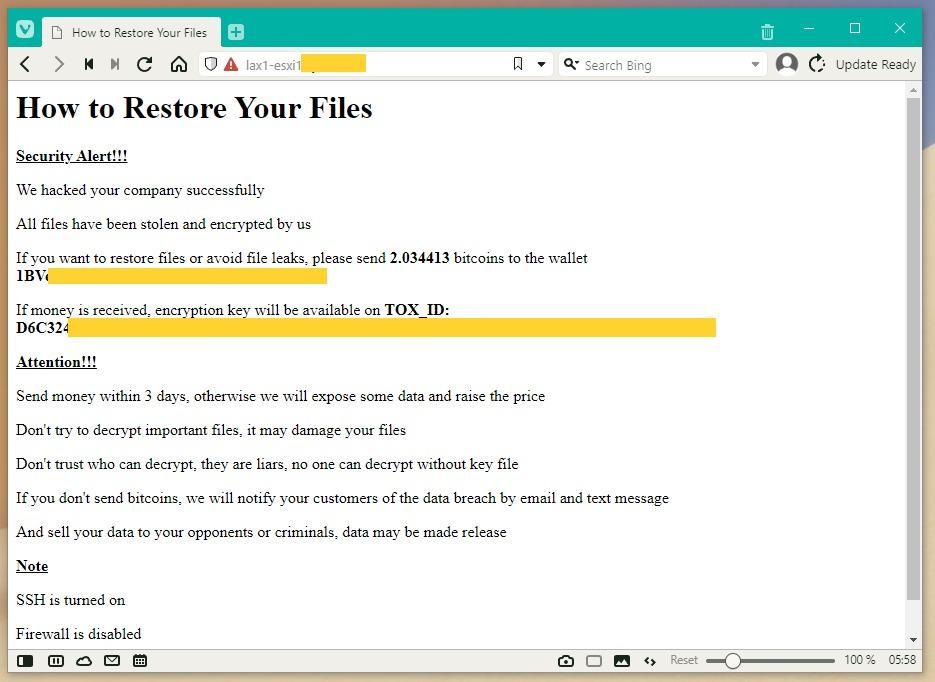
After infiltrating the victim’s system, the hackers encrypt files on the ESXi server and leave a ransom note, extorting $50,000 in bitcoin to decrypt the data.
CERT-FR strongly recommends that everyone install long-available patches as soon as possible, as well as scan all vulnerable systems for signs of compromise. As a last resort, experts advise at least disabling OpenSLP.
In an analysis by experts from cloud service provider OVHcloud, the recent ransomware Nevada was blamed for the massive attacks. The experts wrote that “the attack primarily targets pre-7.0 U3i ESXi servers through the OpenSLP port (427)”.
At the same time, other experts suggested that some version of the Cheerscrypt ransomware, created on the basis of the leaked sources of the Babuk encryptor, could be behind the attacks.
However, in the end, these versions turned out to be incorrect, as a new ransomware called ESXiArgs seems to be behind the attacks.
The publication Bleeping Computer reports that the victims of the attackers are actively communicating and asking for help on its forums. Based on the collected data, most of the affected organizations used ESXi servers leased from cloud providers.
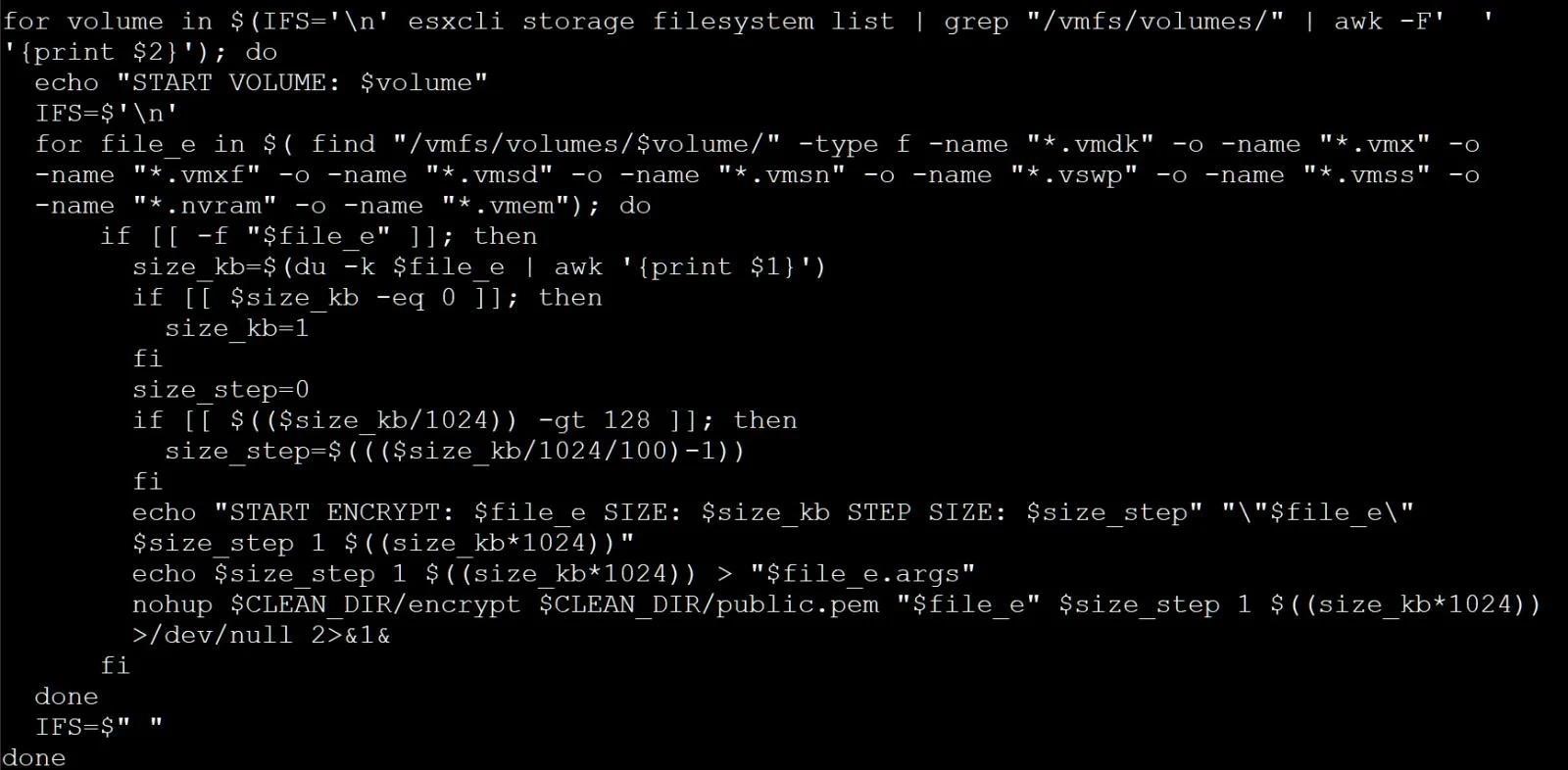
The ransomware encrypts .vmxf, .vmx, .vmdk, .vmsd and .nvram files on compromised servers and creates an .args file with metadata for each encrypted document (probably needed for decryption).
Although the malware operators claim that they steal data before encryption, the victims deny this information: according to the traffic statistics of the victims, no signs of data theft could be found.
An analysis of the malware, conducted by information security expert Michael Gillespie from ID Ransomware, shows that, unfortunately, the ransomware has no obvious “weak points” that would allow victims to recover files without paying a ransom. Gillespie also noted that the malware uses the Sosemanuk algorithm, which is quite unique and is usually used only in ransomware based on the Babuk source code (ESXi version). The researcher believes that the hackers may have modified the code to use RSA instead of the Babuk Curve25519 implementation.
While the ransom notes left behind by ESXiArgs and the Cheerscrypt mentioned above are very similar, the encryption method is different. Therefore, while experts are not sure whether the new malware is some kind of Cheerscrypt variant, or whether both of these threats are simply based on the Babuk code.
French cloud provider OVH and French CERT were the first to report about the incident, as France hosts most of the affected servers. For example, according to Censys data (search of the ransom note file), over 3,200 servers are currently encrypted, and about a third of them are located in France.