Radware experts discovered the DDOSIA crowdsourcing DDoS project, in which a Russian-speaking hack group pays volunteers for participation in attacks on Western organizations.
Let me remind you that we also wrote that Ukraine Was Hit by DDoS Attacks from Hacked WordPress Sites, and also that Fake DDoS App Targets Pro-Ukrainian Hacktivists.
The researchers note that DDoS attacks have long become a powerful weapon in the hands of hacktivists from various countries, because such attacks are easy to organize and carry out, and the damage caused by interruptions in the work of companies and organizations can lead to both financial losses and more serious consequences.
However, usually volunteers involved in DDoS attacks are not rewarded for their “work”, so the discovery of a DDOSIA project is a rather unusual event.
According to Radware, the project was launched in August 2022 by the NoName057(16) group, which appeared in March this year.
This hack group was first mentioned in a September report by Avast, which described a module for DDoS attacks loaded by the Bobik remote access trojan (this malware has been known since 2020 and is distributed by the RedLine stealer). Avast experts observed NoName057(16) for three months, from June to September of this year, and came to the conclusion that the group is carrying out DDoS attacks against Ukrainian organizations, although only about 40% of them are successful.
As Radware analysts now say, relatively recently, the group launched the DDOSIA project on Telegram, where operators posted a link to GitHub with instructions for potential “volunteers”. To date, the group’s main Telegram channel has more than 13,000 subscribers.
Sometimes DDOSIAs attack the same targets set by the pro-Russian hack group KillNet, the researchers say. In particular, they took part in a recent large-scale DDoS attack on major airports in the United States.
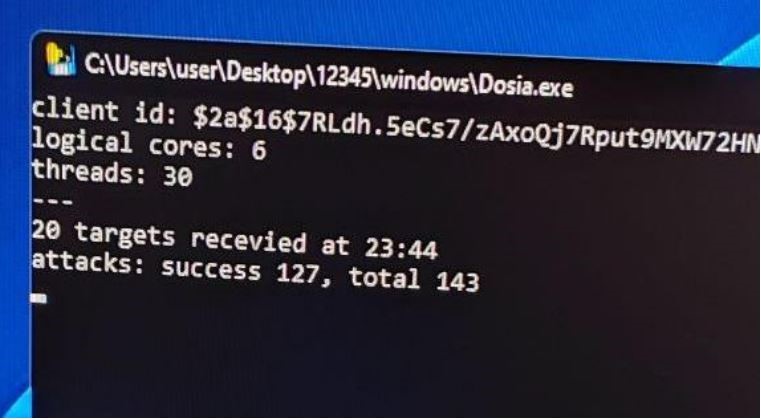
DDOSIA volunteers register via Telegram to receive a ZIP archive with malware (dosia.exe) that contains a unique ID for each user. The most interesting feature of this project is the fact that participants can link their ID to a cryptocurrency wallet and receive money for participating in DDoS attacks. Moreover, payment is proportional to the capacities provided by a particular participant.
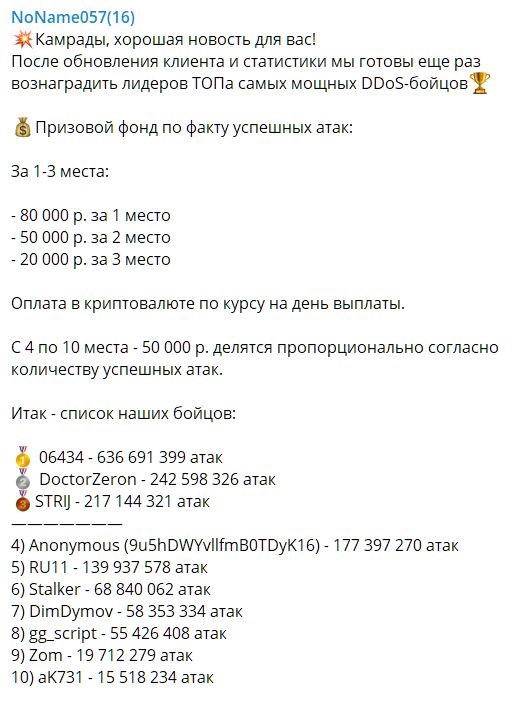
Distribution of “prizes”
The best participants in each wave of attacks receive: 80,000 rubles (approximately $1,255) for first place, 50,000 rubles (approximately $785) for second place, and 20,000 rubles (approximately $315) for third place. In addition, during the attacks on American airports, DDOSIA operators announced that they would distribute additional payments among the Top 10 participants.
Experts summarize that DDOSIA currently has about 400 members and remains a semi-closed invite-only group that regularly attacks more than 60 military and educational organizations.
At the same time, Radware expresses concern that the financial incentive will allow NoName057(16) to attract a lot of volunteers to DDoS attacks, and may set a trend for other DDoS groups.




