A group of researchers has published information on 16 serious vulnerabilities, dubbed BrakTooth, which threaten billions of devices around the world. Vulnerabilities affect the Bluetooth stack in many popular SoCs that are used in laptops, smartphones, industrial devices, and IoT devices.
BrakTooth problems can disable or frozen the device, and in the worst case, help to execute arbitrary code and take over the entire system.
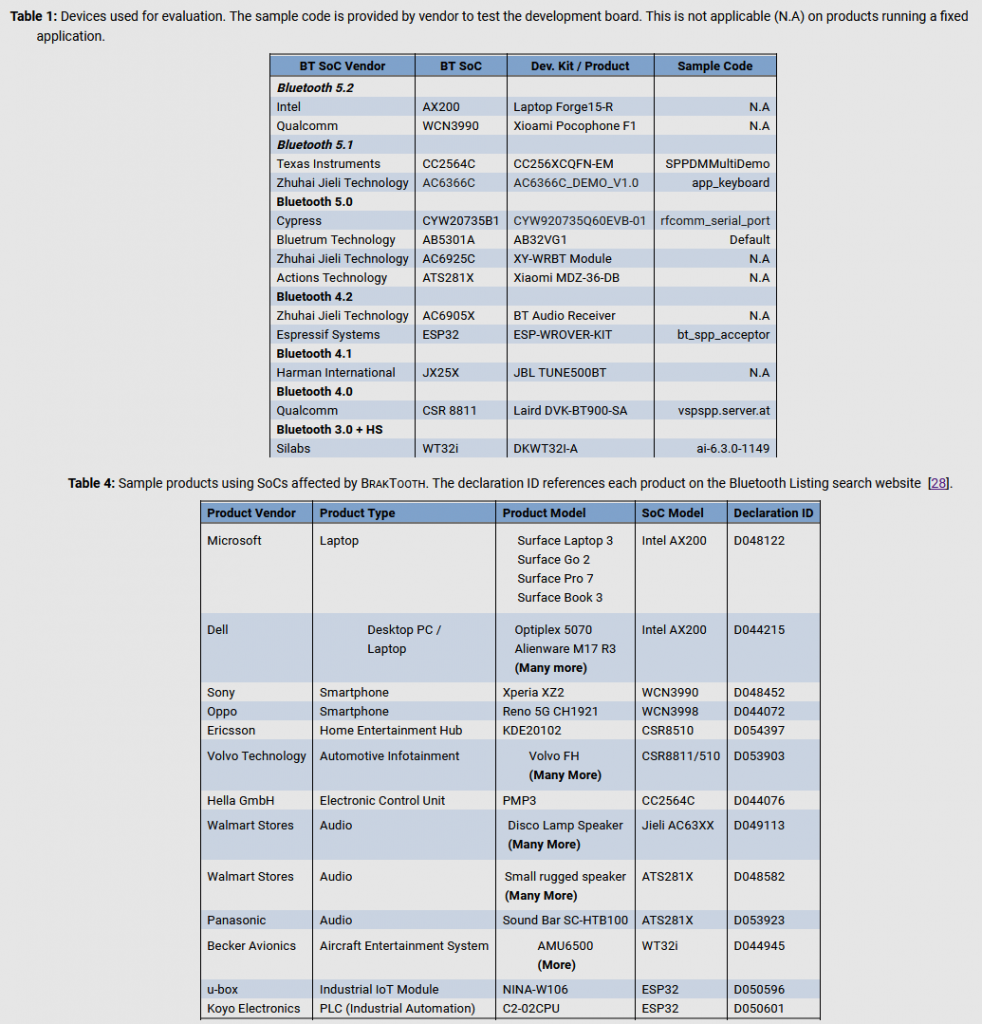
As part of their research, the specialists studied Bluetooth libraries for 13 different SoCs from 11 manufacturers. As it turns out, the same Bluetooth firmware was used in over 1,400 SoCs, which were the basis for a wide variety of devices. Worse, all BrakTooth attacks can be performed using standard Bluetooth hardware, which costs no more than $ 15.
The authors of the report believe that the number of problematic devices is counted in billions, although the degree of vulnerability depends on the SoC of the device and the Bluetooth software stack.
The most serious issue in BrakTooth is the CVE-2021-28139 vulnerability, which allows remote attackers to run their own malicious code on vulnerable devices via Bluetooth LMP.
According to the research group, CVE-2021-28139 affects smart devices and industrial equipment based on Espressif Systems ESP32 SoC, but the problem can affect many other commercial products as well.
Other BrakTooth bugs are less severe. For example, a number of vulnerabilities can be exploited to crash Bluetooth on smartphones and laptops by sending garbled Bluetooth LMP packets to devices. Microsoft Surface laptops, Dell desktops and several Qualcomm-based smartphones are vulnerable to these attacks.
Attackers can also use truncated, enlarged, or out-of-order Bluetooth LMP packets to cause the device to freeze, after which a manual reboot will be required, as shown in the demo below.
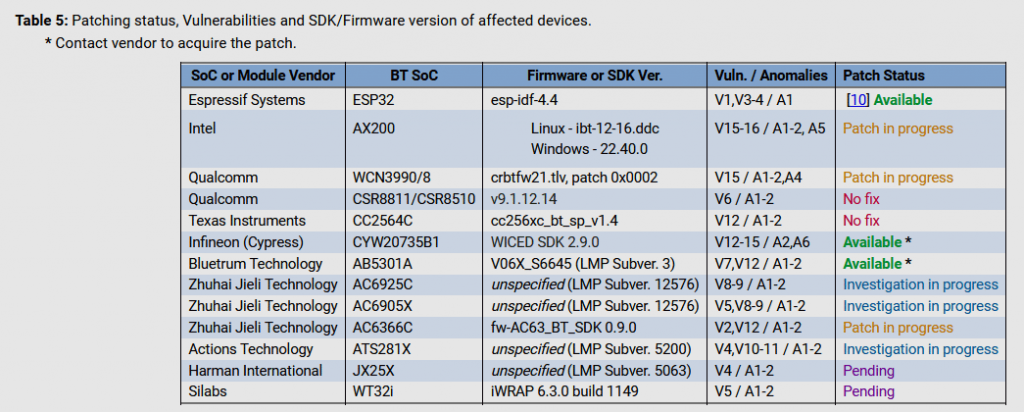
The report states that all manufacturers of vulnerable equipment were warned of the problems several months ago. Alas, despite the elapsed time, not all companies managed to release fixes on time.
At the moment, only Espressif Systems, Infineon (formerly Cypress) and Bluetrum have released patches, and Texas Instruments has generally stated that it will not fix the found deficiencies. Other vendors have confirmed the findings of the researchers, but so far have not even named the exact release dates for the patches.
Representatives of the Bluetooth Special Interest Group, which is leading the development of the Bluetooth standard, say that they are aware of the BrakTooth problems, but cannot put pressure on manufacturers to release patches, since the vulnerabilities do not affect the standard itself, but specific vendor implementations.
Since there are no patches yet, the research team has stated that it is not planning to develop PoC exploits for BrakTooth. Instead, the experts have prepared a special web form through which manufacturers can contact them and request a PoC to conduct self-tests.
Let me also remind you that I talked about the fact that ProxyToken Vulnerability Allows Stealing Mail Through Microsoft Exchange.