CVE-2025-24071 Windows File Explorer Spoofing Vulnerability Uncovered, Patch Now
Microsoft uncovered the information about a critical vulnerability in Windows File Explorer, CVE-2025-24071, with a CVSS score of 7.5. It allows attackers to leak NTLM hashes, which can be used…
StilachiRAT: The Emerging Crypto-Stealing Malware Threat
$34.6 million in cryptocurrency could be at risk from StilachiRAT, a complex remote access trojan first detected by Microsoft Incident Response in November 2024. Unlike conventional ransomware that announces its…
Steganography Attack
Researchers have discovered a non-obvious tactic in which attackers use steganography. While classic tactics rely on obfuscation and encryption, this method uses plain images as a malware carrier. In this…
MassJacker Malware
Cybersecurity researchers have found MassJacker, a new, previously undocumented malware. It targets a predominantly freebie-seeking audience, i.e. users of pirated content. MassJacker Malware Targets Piracy Users MassJacker is a recently…
Jaguar Land Rover Data Breach Involved Two Attacks
Jaguar Land Rover suffered a significant data breach. Two hackers are said to have exploited stolen Jira credentials, leaking sensitive information. The leaked data, including source code, employee details, and…
Trojan:Win64/RustyStealer.DSK!MTB
Trojan:Win64/RustyStealer.DSK!MTB is a sophisticated malware designed to infiltrate 64-bit Windows systems, primarily focusing on stealing sensitive information such as login credentials, financial data, and personal details. It operates silently, making…
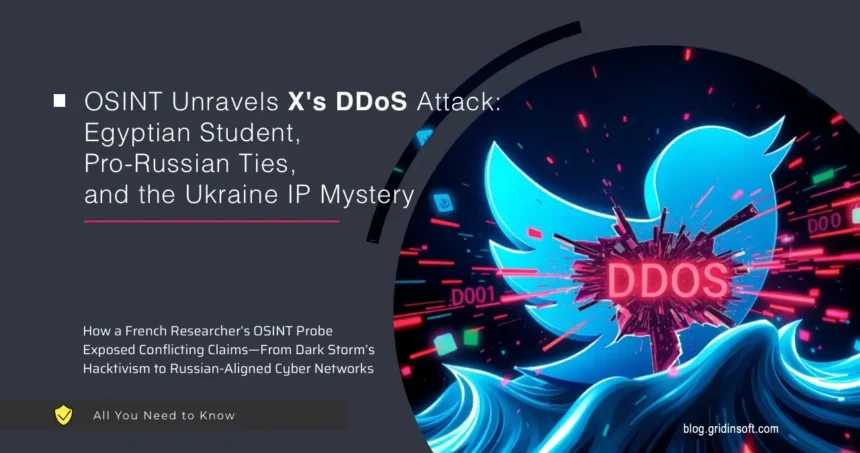
Threat Actor Behind X DDoS Attack Revealed
The X DDoS Attack, reported on March 10, 2025, caused significant outages, affecting tens of thousands of users. Baptiste Robert, a French security researcher, conducted an OSINT investigation and shared…
CISA Adds 5 Exploited Vulnerabilities, Patch ASAP
CISA recently updated its Known Exploited Vulnerabilities catalog, adding five vulnerabilities that are actively being exploited. These affect Advantive VeraCore, used for warehouse and order management in logistics, and Ivanti…
SmartLoader, LummaStealer Abuse Fake GitHub Repositories
A new campaign has been discovered where malicious actors are leveraging AI to craft fake GitHub repositories. They are used to spreading SmartLoader, a malware loader that installs LummaStealer, an…
Microsoft Account Locked
The "Microsoft Account Locked" scam is a deceptive tech support fraud. Users receive pop-up messages falsely claiming their Microsoft account is locked due to suspicious or illegal activities, such as…
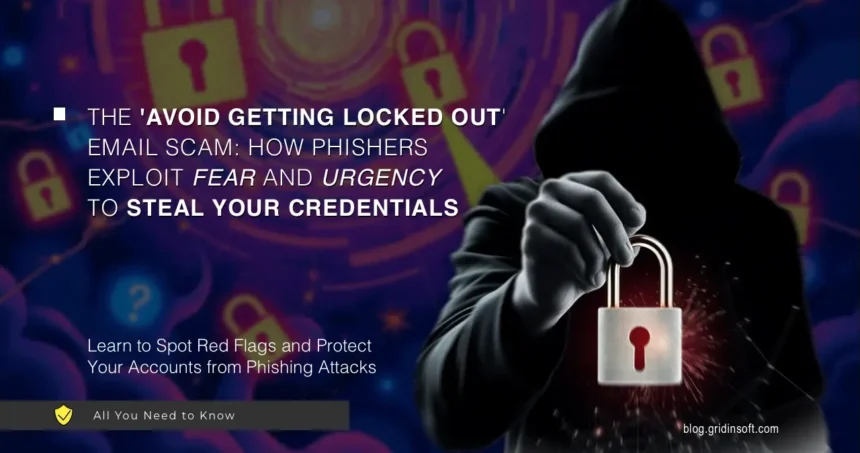
Avoid Getting Locked Out Phishing Email
Avoid Getting Locked Out email scam is a phishing attack designed to exploit fear and urgency, tricking users into revealing their login credentials. As per usual, the message contains a…
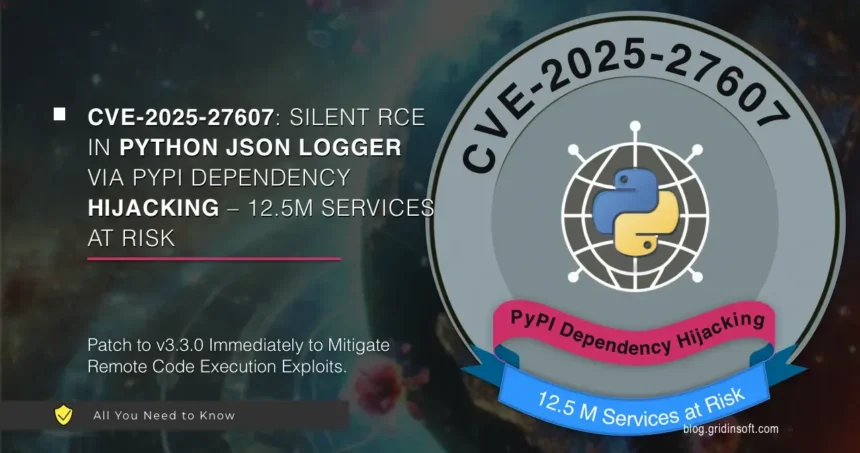
Python JSON Logger Vulnerability Exposes Millions of Users
The CVE-2025-27607 vulnerability was discovered in Python JSON Logger. Its exploitation required no user interaction beyond a standard dependency installation. Attackers could hijack the package name, upload a malicious version,…