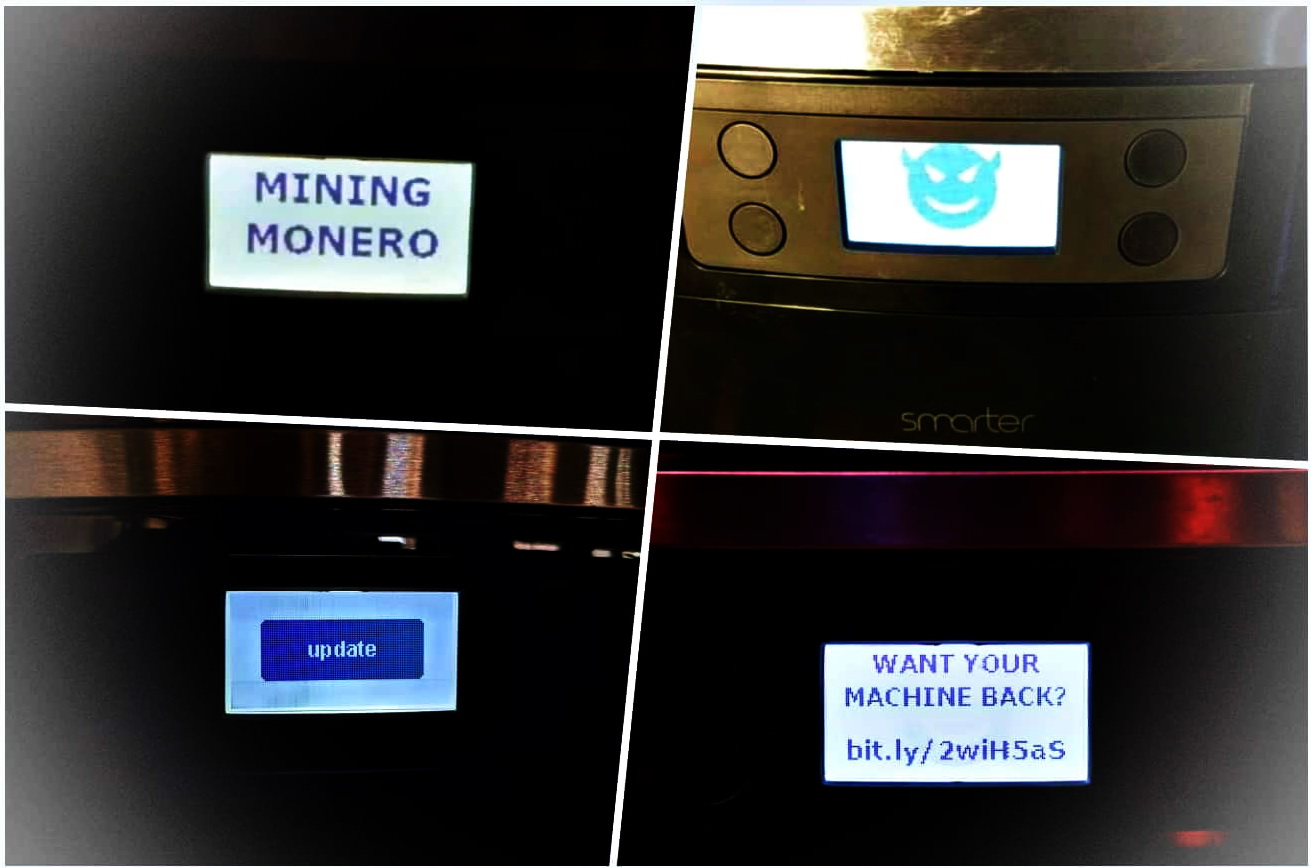
Avast expert taught Smarter Coffee machine to ransom money
Back in 2015, experts from Pen Test Partners talked about a way to hack Wi-Fi networks through the iKettle, created by Smarter, and then discovered that Smarter Coffee maker machine,…
Attackers can bypass TikTok multi-factor authentication through the site
Journalists of the ZDNet publication, citing one of their readers, report that the web version of TikTok did not receive multi-factor authentication (via mail and SMS), which developers established for…
Windows XP source codes leaked
4chan has published a 42.9 GB torrent file, which contains the source codes for several operating systems, including Windows XP and Windows Server 2003. The person who published the file…
Alien malware steals passwords from 226 Android apps
ThreatFabric analysts have discovered a new Android malware Alien. The malware primarily targets banking applications. Overall, Alien steals passwords and other credentials from 226 apps. Alien is sold on hacker…
CISA experts warned about the growth of LokiBot infostealer activity
Specialists from the Agency for Cybersecurity and Infrastructure Protection, organized by the US Department of Homeland Security (DHS CISA), warned about growth of activity of LokiBot infostealer aka Loki and…
Microsoft left open one of the internal servers of the search engine Bing
Ata Hakcil, cyber security specialist at WizCase, discovered that Microsoft employees mistakenly left one of the Bing backend servers open - it was available to anyone. The researcher writes that…
Spammers hide behind hexadecimal IP addresses
Trustwave experts have discovered that pharmaceutical spam attackers have started to insert unusual URLs into their messages. Spammers hide behind hexadecimal IP addresses. They use hexadecimal IPs to bypass email…
Mozilla completely stops development of Firefox Send and Firefox Notes
This summer, I talked about how ZDNet journalists drew attention of Mozilla engineers to numerous abuses of the Firefox Send service, which was actively used to spread malware. As a…
Chinese hackers attack US organizations and exploit bugs in F5, Citrix and Microsoft Exchange
The Department of Homeland Security (DHS CISA) Cybersecurity and Infrastructure Protection Agency (DHS CISA) has published security guidelines for the private sector and government agencies. CISA said that Chinese hackers…
Qbot Trojan Entered The Top Of The Most Widespread Malware
Check Point has released its monthly Global Threat Index for August 2020. According to the researchers, the updated Qbot Trojan (aka QuakBot, Qakbot, and Pinkslipbot) first entered the TOP of…
The researcher kept the INVDoS bug in Bitcoin Core secret for many years
Back in 2018, cyber security specialist and engineer Braydon Fuller discovered a dangerous bug in Bitcoin Core (versions 0.16.0 and 0.16.1). The problem appeared in 2017 and was named INVDoS.…
Intel engineers fixed critical bug in AMT and ISM
Intel engineers fixed this week a critical bug with updates to Active Management Technology (AMT) and Intel Standard Manageability (ISM). The AMT and ISM bug was one of the most…