Beyond Validation: Announcing the Gridinsoft Email Security Checker Upgrade
In an era where phishing attacks are becoming increasingly sophisticated, simply knowing if an email address exists is no longer enough to ensure safety. Phishing messages often look strikingly real,…
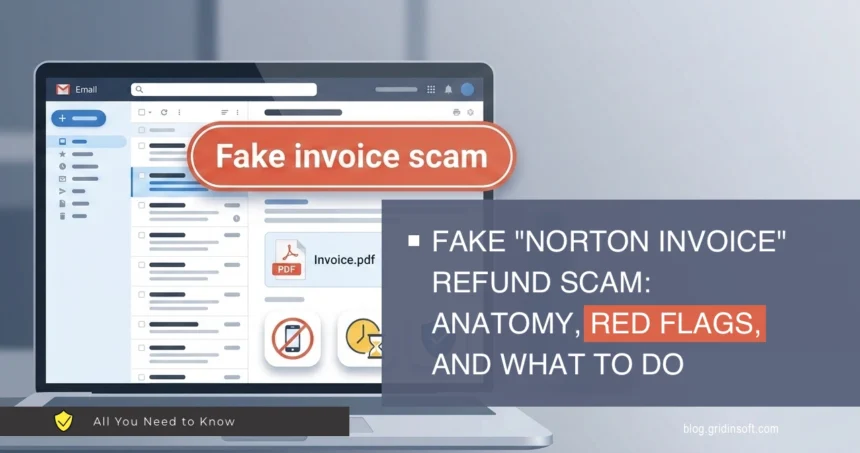
Fake “Norton Invoice” refund scam – anatomy, red flags, and what to do (real example)
A common phishing pattern is the Norton invoice refund scam: an email arrives with a PDF "receipt" that looks like a subscription renewal. The message is designed to create panic…
KimWolf Botnet Hijacks 1.8M Android TVs for Massive DDoS Attacks
If your cheap Android TV box feels slower than usual, it might be busy launching DDoS attacks for someone else. Researchers have uncovered KimWolf, a massive botnet that has quietly…
AI-Generated Fake IDs Are Getting Real – How to Detect and Defend
Fraud teams have been passing around the same kind of screenshot lately: a passport-style fake ID produced by an AI image generator. The output looks clean enough to fool a…
Google Patches Chrome Zero-Day Under Active Attack — Update Now
Google dropped an urgent Chrome update on Wednesday to fix a high-severity vulnerability that's already being exploited in the wild. If you haven't updated your browser yet, now would be…
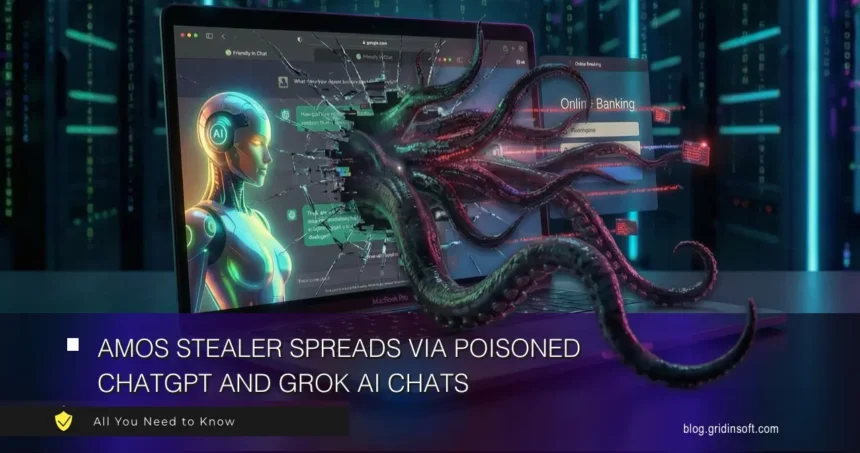
AI Chats Are Delivering AMOS Stealer Through Google Search Results
Here's a novel malware delivery vector that nobody saw coming. Attackers are weaponizing publicly shared conversations with AI assistants like ChatGPT and Grok to deliver the AMOS stealer to Mac…
The Hunter Becomes the Hunted: North Korean Hacker Infected by LummaC2, Exposing Bybit Heist Secrets
In a twist of irony that cybersecurity researchers dream about, a North Korean state-sponsored hacker has been infected by the very thing they usually deploy: commodity malware. A high-end machine…
How to Fix Broken Registry Items in Windows 10/11
The Windows Registry is a massive database containing configuration settings for your operating system, hardware, and installed software. Over time, as you install and uninstall programs, this database accumulates "broken"…
React2Shell Exploitation Goes Live: Chinese APT Groups Strike
Predictably, the exploits are rolling in. Within hours of CVE-2025-55182 disclosure, Chinese APT groups were already hitting targets. And today, valid proof-of-concept exploits started appearing — not useless AI-generated slop,…
React2Shell: Hot December for React and Next.js as Critical 10.0 CVSS Vulnerability Hits RSC
CVE-2025-55182 dropped yesterday evening, and predictably, everyone's losing their minds. Cloudflare rolling out emergency WAF rules, Unit 42 counting nearly a million vulnerable servers, Wiz reporting 40% of cloud infrastructure…
SmartTube YouTube Client Hacked: Your Ad-Free TV App Just Became a Botnet
Using SmartTube on your Android TV to escape YouTube's aggressive ads? Bad news. The popular third-party YouTube client just got compromised, and Google Play Protect is forcibly disabling it on…
Cryptomixer’s €1.3 Billion Laundromat Just Got Washed Out (With Cinematic Flair)
Somewhere in Zurich last week, law enforcement seized Cryptomixer, a cryptocurrency mixing service that spent nine years helping criminals turn dirty Bitcoin into clean Bitcoin. The haul: 3 servers, 12…