Backdoor:Win32/Bladabindi!ml is a generic detection name used by Microsoft Defender. It specifically refers to a backdoor malware known as njRAT, capable of hacking into and controlling victims’ computers. In which cases it is a dangerous trojan and in which cases it is a false positive detection, we will understand in this article.
What is Backdoor:Win32/Bladabindi!ml?
Backdoor:Win32/Bladabindi!ml is the Windows Defender detection for njRAT malware, that is categorized as backdoor. “Bladabindi” is one of many names used by antivirus companies to categorize and identify various malware, including njRAT.
NjRAT is a trojan and can be installed on a computer without the user’s knowledge. It acts as a backdoor, giving attackers remote access and control over the infected system. Once installed, njRAT can perform various activities including collecting sensitive information, recording keystrokes, stealing passwords, intercepting traffic, and even controlling the computer’s webcam and microphone.
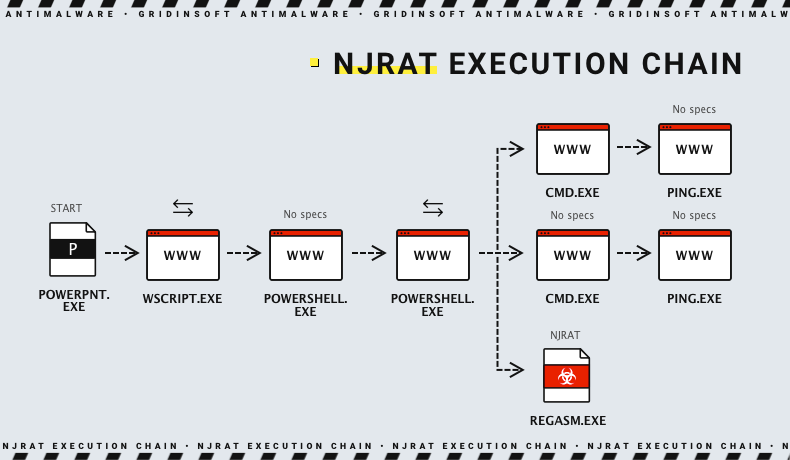
Bladabindi!ml can be spread in a variety of ways. This includes email attachments or malicious links, downloads via malicious websites, exploitation of software vulnerabilities, or social engineering. It can also self-propagate by infecting USB drives connected to an infected computer. Cybercriminals can use various methods to trick users into installing njRAT on their computers.
Bladabindi Backdoor Threat Analysis
NjRAT features several versions, detected in different attacks. Nonetheless, they are not much different in terms of their capabilities and effects. Let’s have a look at what dangers a typical Bladabindi sample carries for the system.
Launch and Detection Evasion
Bladabindi employs various techniques to evade detection upon launch. It comes with its own builder, and before attacking, it allows hackers to pre-configure the payload to their needs before it is delivered to the victim’s computer. This includes the name of the executable file, startup key creation in the registry, directory placement within the target system, host IP address, and network port, among others.
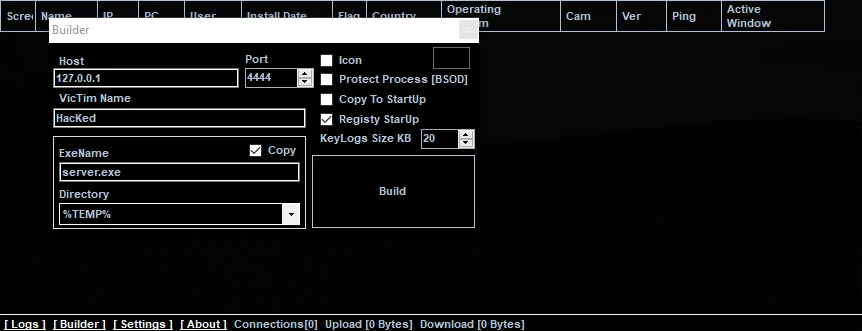
Such customization enables njRAT to circumvent many static checks called to avoid antivirus detection. Additionally, the malware utilizes multiple .NET obfuscators, making its code challenging to analyze for both humans and automated systems. These features make njRAT a tough nut to both analyze and detect and obviously stand for its success.
Establishing Persistence
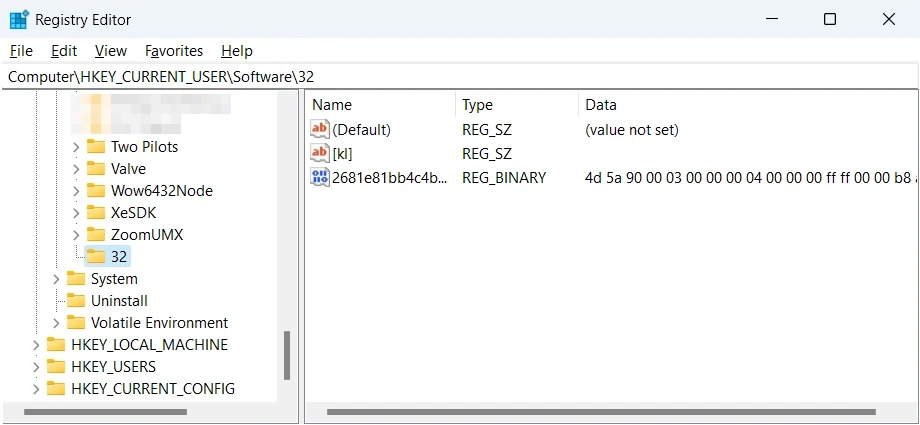
After the initial system checks, the Bladabindi backdoor ensures its persistence within the infected system by creating a startup instance, typically in the “C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp” directory. It also manipulates the Windows registry by creating a key with a unique name and a random set of characters and digits under the “HKEY_CURRENT_USER\Software\32” hive. These actions ensure that the malware executes each time the system boots up. They maintain a foothold within the infected machine even after reboots.
Data Collection & Other Functionality
After finalizing the preparations, njRAT a.k.a Bladabindi performs some basic callouts to the command server. Depending on the response, malware can switch to the idle, start collecting user data or pull the additional payload from the remote server. The overall list of actions it can perform is the following:
- Executing remote shell commands
- Downloading and uploading files
- Capturing screenshots
- Logging keystrokes
- Camera and microphone access
- Stealing credentials from web browsers and desktop crypto applications
Is Win32/Bladabindi!ml false positive?
Some programs may have features or behaviors that may be mistakenly considered suspicious by antivirus software. As a result, Windows Defender shows a false positive detection. This may be due to the use of certain APIs, network requests, or data encryption that may be characteristic of malware but are also present in legitimate applications.
It’s also worth noting that antivirus often adds “!ml” to the end of its name – to indicate the use of the AI detection system. Although it is a highly effective method, without the confirmation from other detection systems, it is easy to make it generate false positive detections.
How to Remove Backdoor:Win32/Bladabindi!ml Virus?
The most reliable way to remove Backdoor:Win32/Bladabindi!ml is to use a reliable antivirus program with updated virus databases. I recommend an antivirus like GridinSoft Anti-Malware, it is best to detect and remove even the sophisticated malware like Bladabindi/njRAT.
After removing Win32/Bladabindi!ml, it is recommended to perform additional system scans to make sure that all threats have been successfully removed. And in the future, be vigilant when surfing the Internet and downloading files. Avoid visiting suspicious websites and opening attachments from unreliable sources.





