How To Use Public Wi-Fi Safely: Risks To Watch Out For
In a world where almost everything comes with a price it's sometimes…
Who stands behind cyberattacks? Top 5 types of attackers
When accessing the internet, we are often introduced to seemingly wonderful websites,…
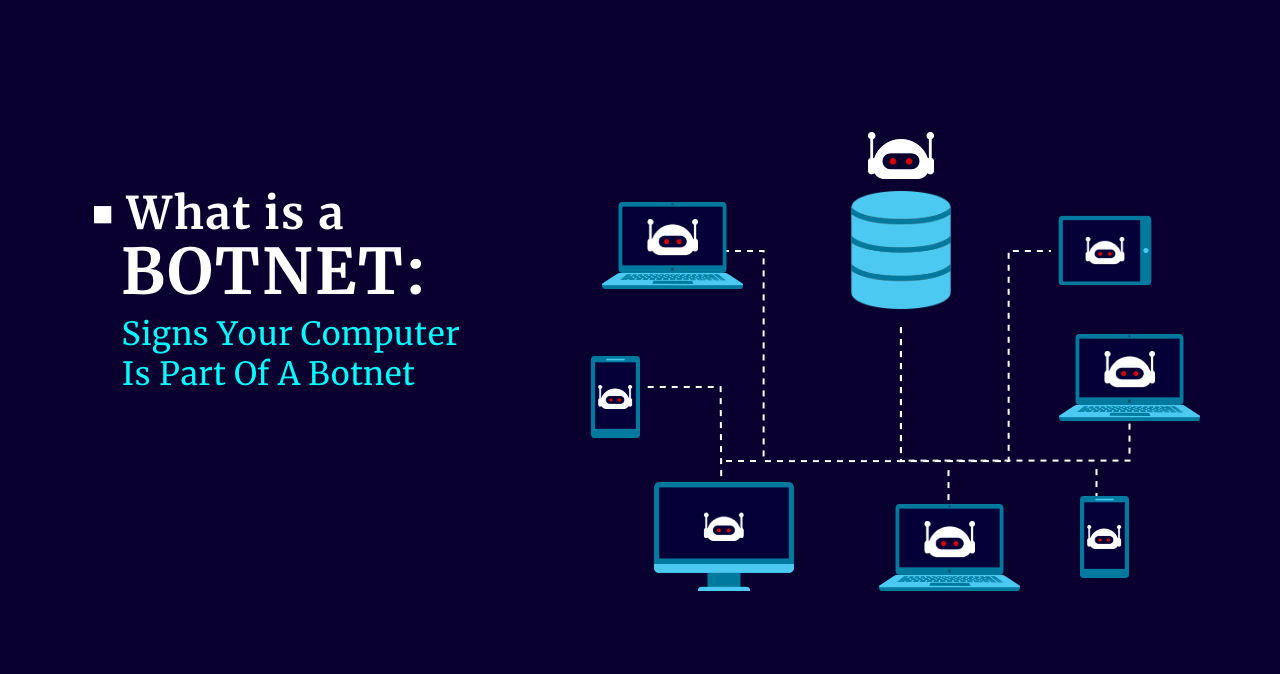
What is a Botnet: Signs Your Computer Is Part Of A Botnet
Botnets are a new reality that seems to have somehow imperceptibly swooped…
How to clean space on your Windows computer?
Nothing is more annoying than receiving a notification about your device’s storage…
How can you enhance the security of your browser?
Which is the most secure Web browser? Google Chrome? Mozilla Firefox? Microsoft’s…
How To Fix a Computer That Randomly Restarts
Modern computers have working stability much higher than the stability of the…
Google Fined Record €4.3 Billion for Abusing Dominance in Smartphone Market
On July 18, 2018, the European Commission announced that it had fined…
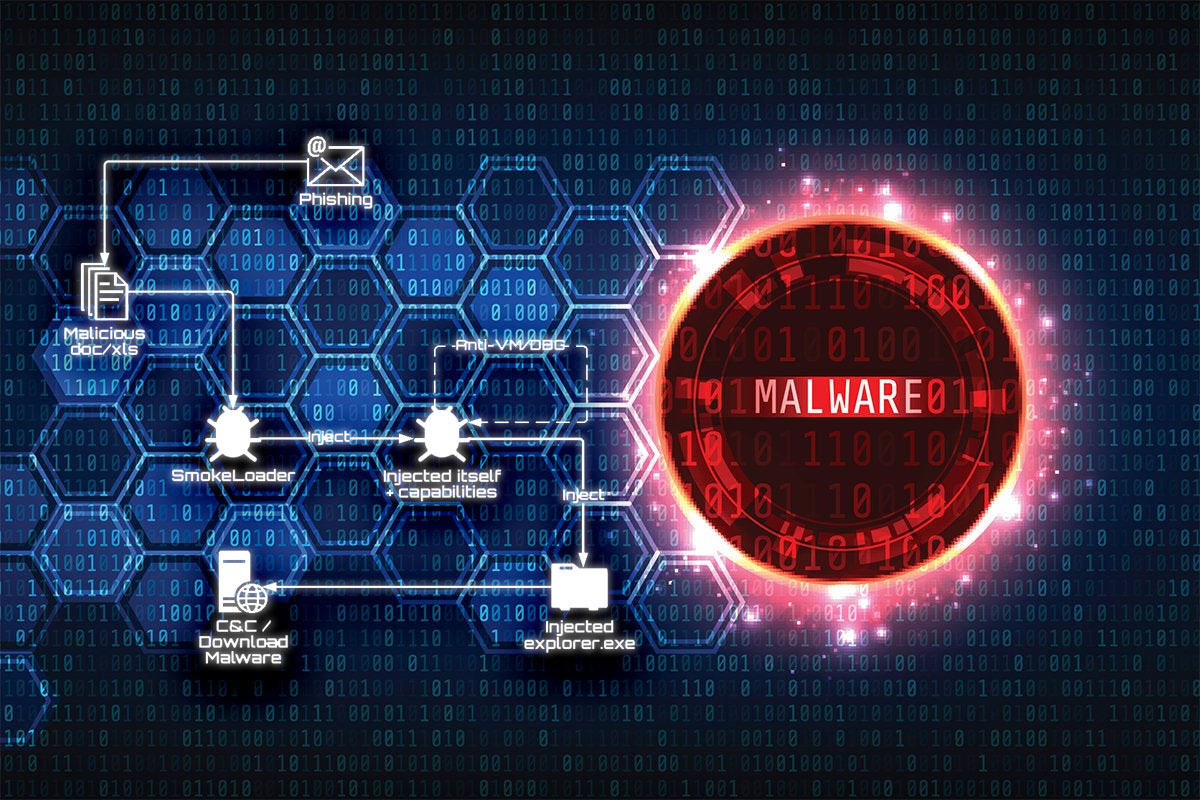
Smoke Loader Malware: New Password-Stealing Infection Method
A new variant of the Smoke Loader malware has been discovered that…
How to Disable Push Notifications in Your Browser
More and more sites use push notifications to show you the latest…
Facebook Gives US Lawmakers the Names of 52 Firms with Deep Data Access
Facebook has been under scrutiny for its handling of user data, with…
How To Send System Information For Analysis
Viruses are very tricky and even after the scan with reliable anti-malware…
Age restrictions and children : what is important
15 years ago it was hard to imagine that personal devices will…