MSMQ Vulnerability Allows Remote Code Execution
Recent update released by Microsoft, an April Patch Tuesday, revealed a severe…
Rorschach Ransomware Analysis
Recent research from the CheckPoint Research team revealed a new ransomware sample…
Genesis Market Seized by FBI
Genesis Market, a Darknet marketplace for stolen information, was reportedly seized by…
APT43 Funds Cybercrime With Stolen Crypto
Researchers have identified a new state-backed hacker group in North Korea. The…
Ransomware Actors Target IBM’s Aspera Faspex
File transfer utility Aspera Faspex, developed by IBM, became a riding mare…
3CX Phone System is Struck With Chain Supply Attack
3CX Phone System, a desktop app for business phone communication, fell victim…
Binance US Ban Scams Incoming: What to Expect?
Recent events around one of the world's largest cryptocurrency exchanges Binance sound…
Malicious ChatGPT Add-On Hijack Facebook Accounts
ChatGPT became a worldwide phenomenon in recent months. GPT-4 update created even…
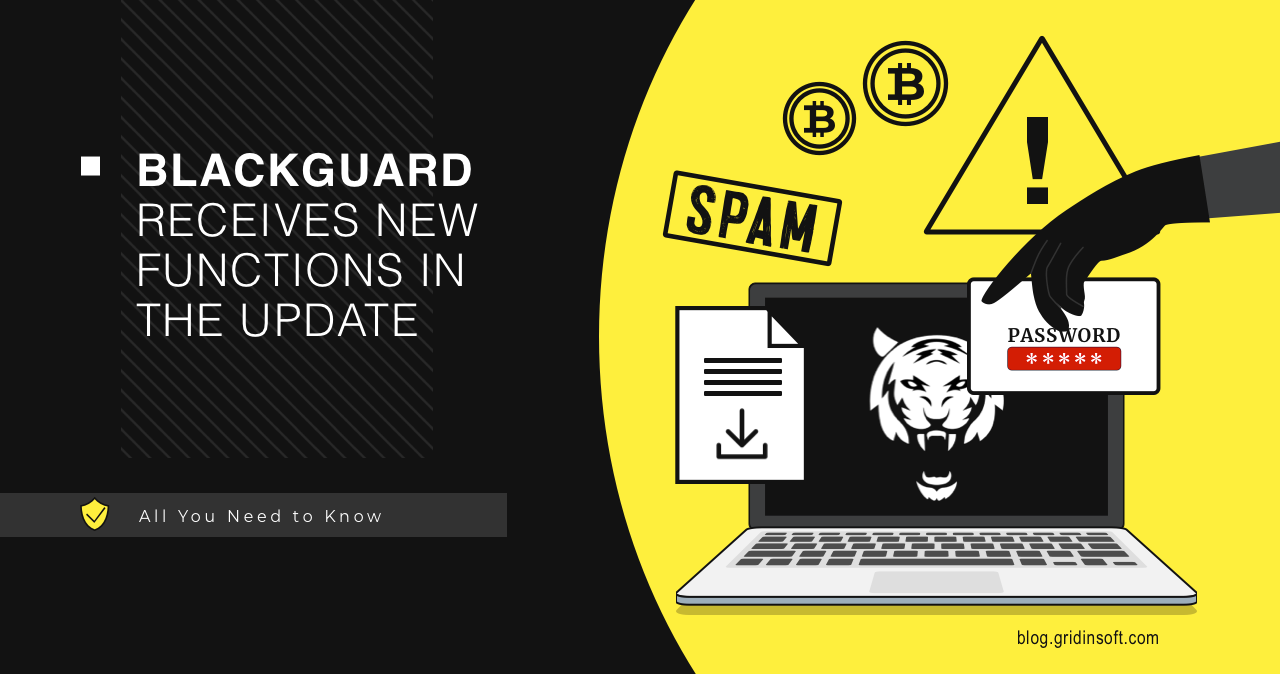
BlackGuard Receives Update, Targets More Cryptowallets
BlackGuard, a prolific infostealer malware, received an update at the edge of…
Linus Tech Tips YouTube Channel Hacked
Linus Tech Tips, a YouTube 15-million tech channel, was hacked and then…
Financial Assistance Department Email Scam to call (855)-XXX-XXXX
Email is one of the oldest ways to exchange information over the…
BreachForums is down. Things got worse?
Recently, one of BreachForums administrators nicknamed PomPomPurin was arrested by the FBI.…