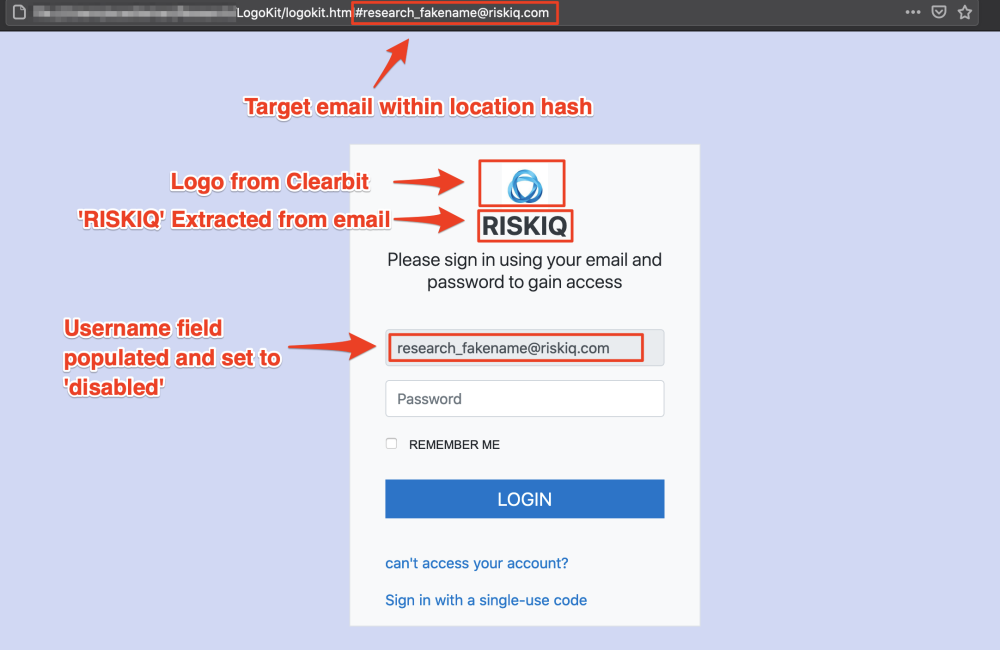
RiskIQ researchers said that the new LogoKit phishing kit was detected on more than 700 unique domains in the last month alone and on 300 in the last week.
Worse, this tool allows hackers to modify logos and text on phishing pages in real-time, tailoring sites for specific purposes.
LogoKit relies on sending users phishing links containing their email addresses. LogoKit pulls up the company logo from a third-party service, such as Clearbit or the Google favicon database when the victim goes to such a URL.
The malware accomplishes this through an embedded set of JavaScript functions that can be integrated into any standard login form or complex HTML documents. This is the main difference between LogoKit and other phishing kits, as most require pixel-accurate templates that mimic company-specific authentication pages.
Analysts point out that modularity allows LogoKit operators to organize attacks on any company, spending a minimum of time and effort. For example, over the past month, LogoKit has created fake login pages that mimic various services, from regular login portals to fake SharePoint login pages, Adobe Document Cloud, OneDrive, Office 365, and several cryptocurrency exchanges.
Even worse, because LogoKit is just a collection of JavaScript files, its resources can even be hosted on Firebase, GitHub, Oracle Cloud, etc. Most of them are whitelisted in corporate environments and may appear harmless to security solutions and users.
Let me remind you that Cybercriminals started using Google services more often in phishing campaigns
.