The X DDoS Attack, reported on March 10, 2025, caused significant outages, affecting tens of thousands of users. Baptiste Robert, a French security researcher, conducted an OSINT investigation and shared his findings in an X post. I’ve got through the voluminous investigation and made a list of key findings that explain what is going on.
X DDoS Attack Overview
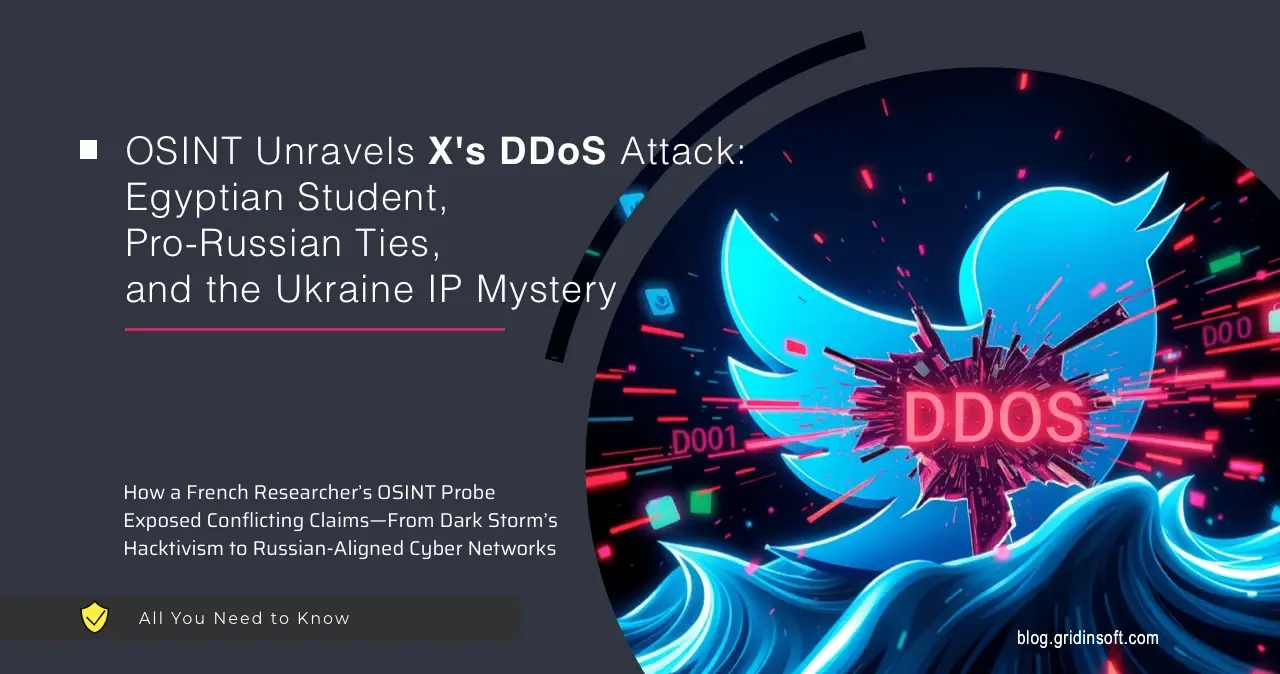
On March 10, 2025, X experienced multiple outages due to a Distributed Denial-of-Service (DDoS) attack, which overwhelmed the platform with traffic, disrupting service for tens of thousands of users. The attack was significant enough to prompt statements from X owner Elon Musk, who described it as a “massive cyberattack” involving “a large, coordinated group and/or a country.”
Musk specifically mentioned that the attack was traced to IP addresses originating from the “Ukraine area,” as reported in various news outlets. Concurrently, the pro-Palestinian hacktivist group Dark Storm claimed responsibility via a Telegram post, which was later deleted for violating platform terms.
OSINT Investigation Reveals the Threat Actor
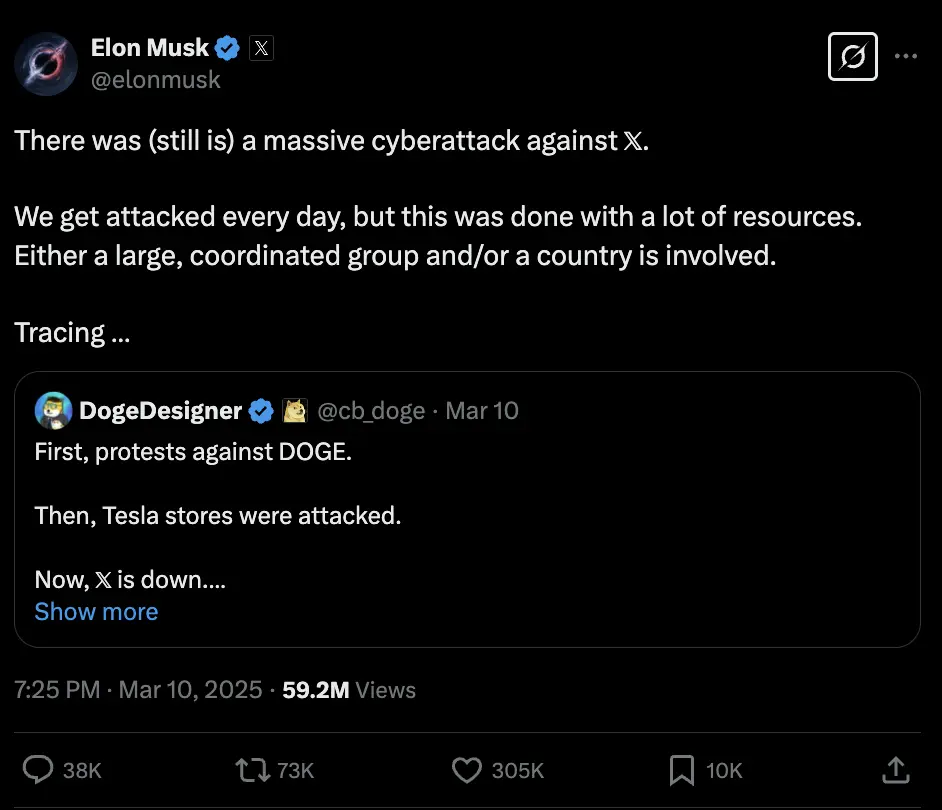
Baptiste Robert, a French security researcher from Predicta Labs, conducted an Open Source Intelligence (OSINT) investigation to identify the individual behind the X DDoS Attack. His findings were shared in an X/Twitter post, where he detailed his process and expressed interest in meeting Elon Musk to discuss the discovery.
Robert’s investigation began with examining the social media handles of Dark Storm’s alleged leader on Telegram, identified as MRHELL112, who had previously used usernames like Darkcrr, GLITCHAT1, and GLITCHcracker. He traced connections to another Telegram user, DrSinaway, mentioned in a DDoS attack services channel, whose bio referenced the CyberSorcerers group. Robert noted similarities between Dark Storm and CyberSorcerers logos, suggesting a connection.
Further, Researcher found an email address, [email protected], and used a tool to obtain a phone hint (+20 1• ••••1939), which matched the phone hint for DrSinaway’s official Instagram account. This led him to a Linktree profile with a bio matching a Facebook account of an Egyptian student named Mohammed Hany. Searching “Brain Hack – KSU” on LinkedIn revealed a page with associated people, including Mohamed Hany, a student located in Giza, Egypt.
Robert’s analysis indicated that Hany joined a DDoS-focused Telegram group aligned with a Russian group in August-September 2023, “for the benefit of Russia and the Arab world,” and suggested Hany has at least one accomplice. The researcher provided a link to an investigation-related graph for further details.
Conflicting Claims and Discrepancies
Despite Robert’s detailed OSINT work, there is a significant discrepancy with Elon Musk’s claims. Musk’s assertion that the attack originated from IP addresses in the “Ukraine area,” contradicts the Egyptian origin suggested by Robert. Robert’s OSINT investigation is impressive, with security insiders praising his work on X, as noted in the cybernews.com article. However, given Musk’s tendency to post questionable and sometimes misleading and false information, the researcher’s report looks very convincing.
Many on X were impressed by Robert’s OSINT skills, calling his work “mindblowing” and “a masterclass in digital sleuthing.” His detailed timeline earned praise, with some joking he deserved a “cyber detective award.” The blurred image of the alleged hacker, paired with Robert’s call to meet Elon Musk, fueled excitement, with users tagging Musk and speculating about a possible collaboration.
However, skepticism emerged, with comments like “A script kiddie took down X? Sounds like a movie plot,” questioning whether a single Egyptian student could pull off such an attack. Though given how Elon Musk has been downsizing the social network’s staff, it’s no surprise.
Humor played a big role, as users mocked the idea of a “noob skiddie” challenging X—one quipped, “Thought it was a state-sponsored hack, but it’s just some kid in Giza with a laptop.” The revelation of Mohammed Hany’s identity sparked memes like “Mohamed vs. Musk: the ultimate showdown,” complete with popcorn emojis.
Cybersecurity and tech news outlets reacted with intrigue but also cautious skepticism, framing the investigation within the broader context of the X DDoS attack and Musk’s conflicting claims. Some praised it as a groundbreaking OSINT achievement, highlighting the identification of the alleged attacker and the power of tracing digital footprints. Others acknowledged its value but pointed out alternative attack origins, citing traffic from multiple countries. Given the complexities of DDoS attribution, many emphasized the need for deeper forensic analysis.
Some reports focused on the narrative clash, critiquing Musk’s claim as speculative while viewing the investigation as an intriguing but inconclusive counterpoint. Others examined the hacker group’s history, suggesting possible Russian ties and its evolution since 2023. Across all coverage, the findings were seen as a compelling lead but not definitive proof, with experts stressing the need for official confirmation.