A new campaign has been discovered where malicious actors are leveraging AI to craft fake GitHub repositories. They are used to spreading SmartLoader, a malware loader that installs LummaStealer, an information-stealing malware.
LummaStealer and SmartLoader Use AI-Powered Fake GitHub Repos
Cybersecurity researchers have discovered a fraudulent campaign leveraging GitHub. The incident involves a sophisticated cyber campaign where threat actors leverage AI to create fake GitHub repositories. These repositories are designed to distribute SmartLoader, a malware loader known for delivering LummaStealer, an information-stealing malware, and potentially other payloads.
The campaign exploits GitHub’s reputation as a trusted platform for code hosting, with over 100 million developers relying on it. Unlike previous attacks, here the crooks used AI to make the repository look convincing. This is a notable evolution, aligning with trends observed in other recent campaigns. This also aligns with the particular attitude towards unusual spreading methods that Lumma infostealer masters tend to rely on.
Technical Details of Fake GitHub Repositories Trick
Like most attacks these days, this one relies primarily on social engineering – a win-win of all time. The execution of the campaign involves creating fake GitHub repositories that mimic legitimate projects, such as gaming cheats, cracked software, or system tools. These repositories are designed to look authentic, often featuring detailed README.md files and documentation.
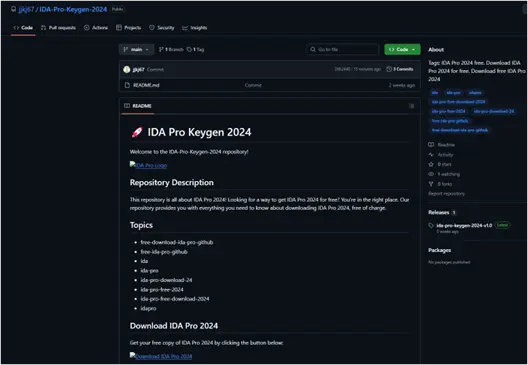
When users download and execute the code, they inadvertently install SmartLoader, a versatile malware loader capable of hosting and distributing various malware. The ZIP archive contains the following files:
- lua51.dll. The LUAJIT runtime interpreter.
- luajit.exe. The Lua loader executable.
- userdata.txt. A malicious Lua script.
- Launcher.bat. A batch file used to execute luajit.exe with userdata.txt passed as an argument.
The batch file launches luajit.exe, which in turn executes the Lua script concealed within userdata.txt, serving as the true malicious payload responsible for compromising the victim’s system. SmartLoader then connects to GitHub to download additional files, lmd.txt and l.txt, renaming them to search.exe and debug.lua, respectively, with search.exe being LummaStealer. The LummaStealer uses a misnamed AutoIt interpreter and connects to a C2 (C&C) server at pasteflawwed[.]world to exfiltrate logs and sensitive information.
The campaign’s evolution is also noted, showing a shift from previous tactics of using GitHub file attachments to creating entire repositories, as seen in the October 2024 campaign, which used fake webpages. This shift introduces new lure mechanisms, where AI-generated repository README files replace traditional fake webpages. Additionally, evasion tactics continue to evolve, helping maintain operational resilience despite increasing security scrutiny.
Role of AI in the Deception
Continuing with the theme of repository design, it’s worth paying special attention to the role of AI. Here, AI is leveraged to craft convincing README files and documentation, giving repositories a professional and authentic appearance. This increases the chances that users will trust and install the malicious content.
Experts also highlighted specific traits like excessive emoji usage, unnatural phrasing, and overly structured content as clear indicators of AI assistance. This aligns with broader cybercrime trends, where machine learning and natural language processing are used to create persuasive social engineering content.
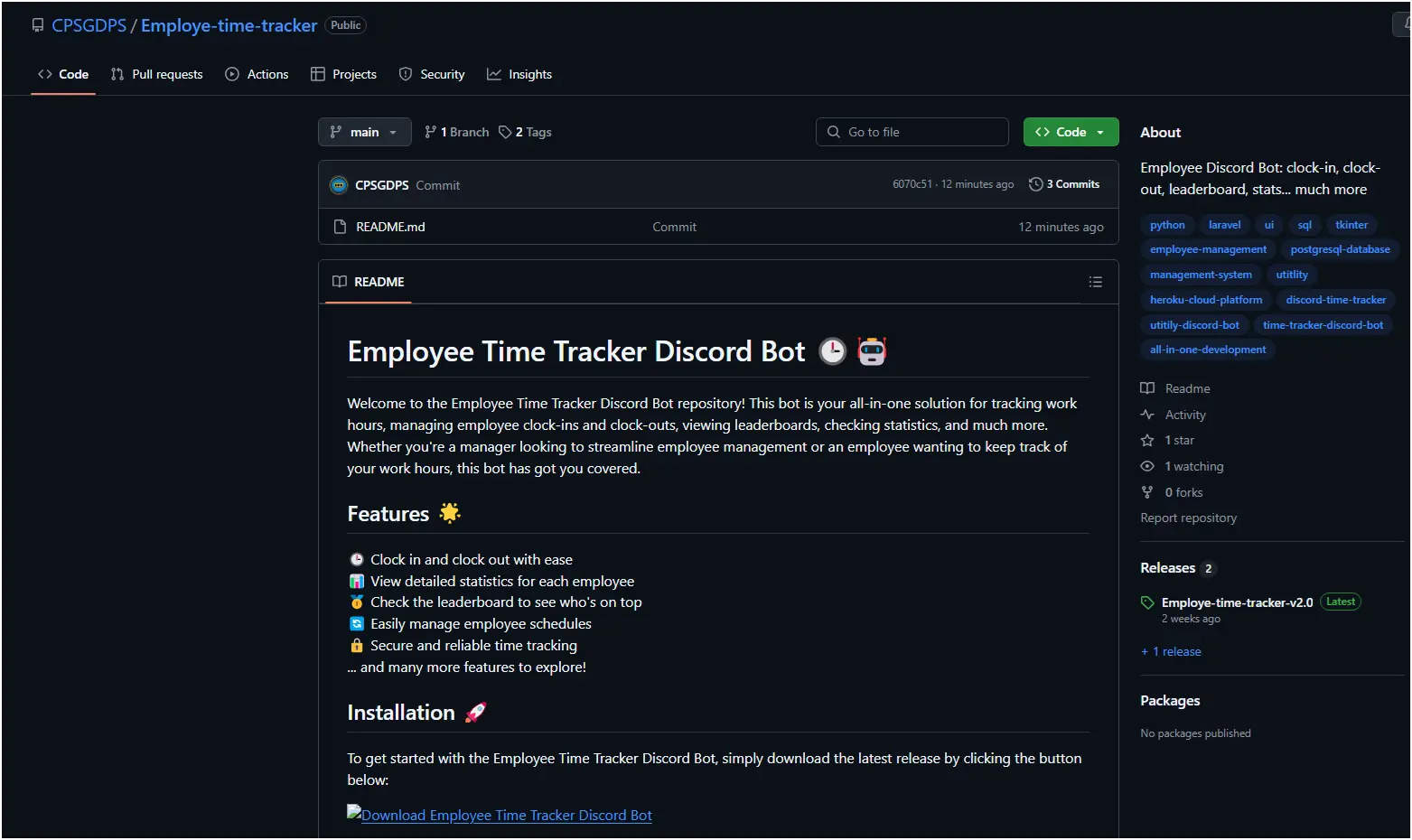
This adaptability is evident in the transition from file attachments to repositories, where AI helps threat actors scale operations and reach a global audience. They specifically target users searching for gaming mods, software cracks, or other tools, as highlighted in the text.
Impacts and Broader Implications
As for the impact, this campaign affects individuals, organizations, and the broader software ecosystem. LummaStealer is capable of extracting sensitive data such as login credentials, payment details, and cryptocurrency wallets. Additionally, it targets two-factor authentication (2FA) extensions, increasing the risk of identity theft, financial fraud, and unauthorized access to critical accounts.
Smart Loader, on the other hand is a term that identified as a malware loader. It use of Lua, a lightweight scripting language, which enhances its flexibility and ability to evade detection. SmartLoader with samples first seen on June 10, 2023, and last seen on February 27, 2025, indicating active presence.
Once installed, it establish communication with command and control (C2) servers to receive tasks and additional payloads. SmartLoader’s capabilities also include information gathering, such as IP, country, and city via services like http://ip-api[.]com/json/, screenshot capture, and leveraging FFI (Foreign Function Interface) libraries for C code execution, utilizing modules like shell32.dll and advapi32.dll.
For organizations, the reputational damage can be severe, especially if customer data is compromised, leading to loss of trust and regulatory penalties under laws like GDPR or CCPA. Threat actors can also sell this stolen data on the dark web, amplifying risks to victims.
Mitigation Strategies and Challenges
Mitigation requires a multi-layered approach, addressing both technical and human factors. Users should download software only from official sources, verify repository authenticity by checking for legitimate contributors, repository history, and signs of AI-generated or suspicious documentation, and enable security features like proper antivirus tools or endpoint security solutions. However, challenges remain, particularly in detecting AI-generated content, which can mimic legitimate documentation closely.
To ensure the protection on your end, consider using GridinSoft Anti-Malware as a personal security tool. It provides excellent on-run security, capable of stopping even the most novel threats, and an online security module which prevents you from exposure to any online sources of danger. Download it by clicking the banner below, and do not miss out on the 6-day free trial period.






GITHUB IST THE PLACE WHERE YOU MEET DIFFERENT GEEKS WHO CAN HELP YOU TO SOLVE DIFFERENT PROBLEMS ON TODAYS WORLD.