The CVE-2025-27607 vulnerability was discovered in Python JSON Logger. Its exploitation required no user interaction beyond a standard dependency installation. Attackers could hijack the package name, upload a malicious version, and execute arbitrary code on affected systems. Users are advised to update to version 3.3.0, which addresses the issue.
CVE-2025-27607 Overview
Numerous reports point at a newly discovered critical security vulnerability identified as CVE-2025-27607, affecting the Python JSON Logger, a popular JSON formatting library for Python logging. This vulnerability has a CVSS score of 8.8 and was discovered between December 30, 2024, and March 4, 2025. It is a remote code execution flaw, which is considered one of the most dangerous flaws one can encounter.
It is caused by a missing dependency—specifically, the msgspec-python313-pre package. The package was deleted by its owner, leaving the name open for malicious actors to claim. The issue was resolved in version 3.3.0 of Python JSON Logger, released to patch the vulnerability. Some of the estimations expec over 12.5 million services to be affected, so the updating to the patched version is a necessity, not an option.
Python JSON Logger Vulnerability Technical Details
CVE-2025-27607 arises due to a supply chain attack vector in Python’s package ecosystem, specifically PyPI (Python Package Index). The Python JSON Logger library, when installed with development dependencies (e.g., using pip install python-json-logger[dev]), relied on the msgspec-python313-pre package for Python 3.13 compatibility. However, the owner of this dependency removed it, leaving the package name available for anyone to claim. A malicious actor could claim the package name, upload a malicious version, and introduce code that executes remotely on any system installing or updating Python JSON Logger with the development dependencies.
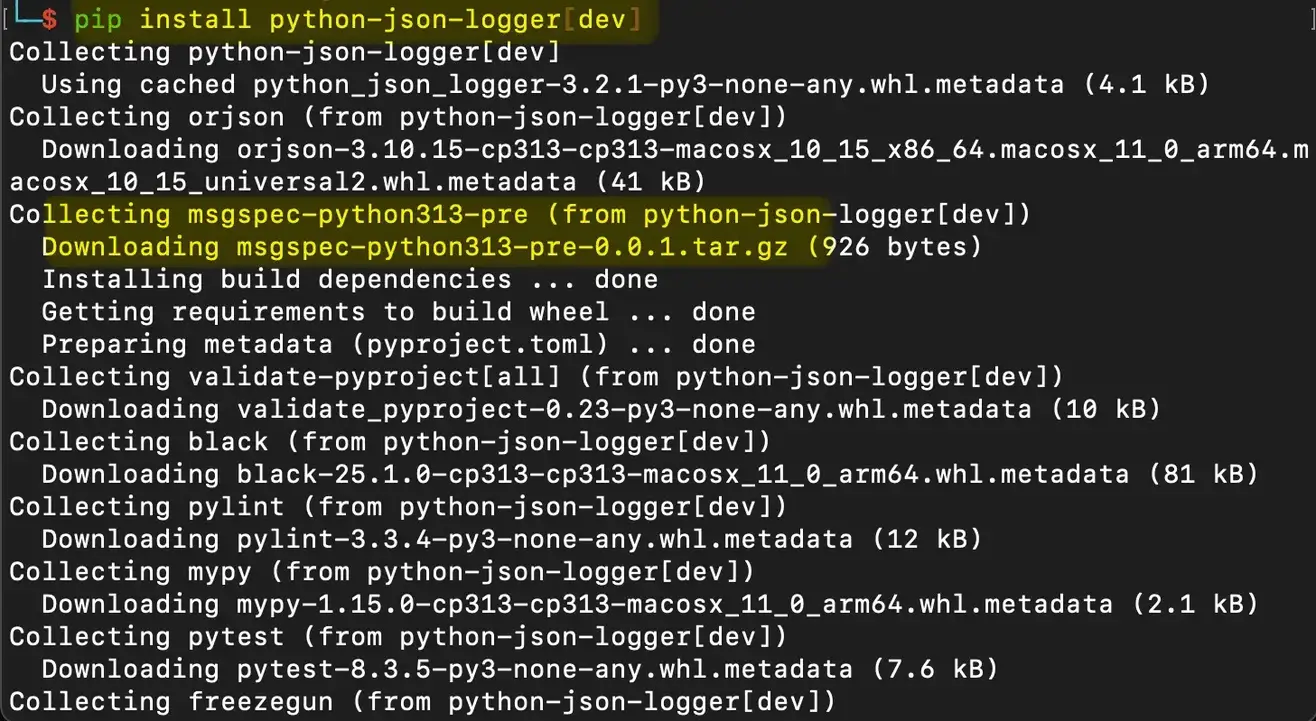
This RCE vulnerability allows attackers to run arbitrary code on affected systems, potentially compromising servers, applications, or entire networks that use the library. The vulnerability is particularly dangerous because Python JSON Logger is widely used in logging configurations across various applications, and the attack requires no user interaction beyond a standard dependency installation.
Expected Impact of the Flaw
The impact of CVE-2025-27607 is significant due to its potential for remote code execution, classified as a high-severity vulnerability. Systems running Python JSON Logger versions prior to 3.3.0, especially those using Python 3.13 and the development dependencies, are at risk of complete compromise if a malicious version of msgspec-python313-pre is installed.
This could lead to data breaches, malware deployment, or unauthorized access to sensitive systems. A post on X/Twitter indicates that 12.5 million services worldwide may be vulnerable. The vulnerability’s exploitation window, from December 30, 2024, to March 4, 2025, also means many systems could have been exposed during this period, especially if automatic dependency updates were enabled.
Response and Mitigations
The response to CVE-2025-27607 came from the maintainers of JSON Logger, who acted swiftly to address the vulnerability. After the issue was identified, likely through community reports or security research, the maintainers released version 3.3.0 of the library to resolve the problem. This update ensures that the dependency on msgspec-python313-pre is either removed, replaced with a secure alternative, or properly secured to prevent package hijacking.
The report confirms that the vulnerability was patched by March 7, 2025, with clear guidance for users to upgrade to version 3.3.0 or higher to mitigate the risk. Users are also advised to monitor their dependencies closely to prevent similar issues in the future.