Fox Ransomware is believed to be a variant of the Dharma family, a notorious ransomware actor that encrypts user files and demands payment for decryption. The files affected by this virus are recognizable by the .FOX extension that the malware appends to every single one of them. This malware can severely disrupt personal and organizational data access, often targeting systems with weak security.
Fox Ransomware Overview
Fox Ransomware is categorized as a member of the Dharma family, a prominent ransomware lineage first noted in 2016. It is known for its evolution into Ransomware-as-a-Service (RaaS) models. This family is notorious for encrypting both local and network-shared files. It also disables system firewalls and deletes Volume Shadow Copies to hinder recovery efforts. Fox, specifically, is designed to lock user files, demanding a ransom for decryption, and can cause significant data loss and financial impact.
The Dharma family’s characteristics include manual installation via RDP exploitation, often targeting small and medium-sized businesses. Its variants, including Fox, are distributed through brute-force attacks on port 3389. This manual distribution method, unlike automated spam emails, highlights the targeted nature of these attacks. It exploits vulnerabilities in remote access protocols to gain unauthorized access.
How Does It Work?
Fox ransomware’s infection vector primarily involves manual intrusion through compromised RDP connections. Attackers scan the internet for computers with open RDP, typically on TCP port 3389, and attempt to brute-force passwords. Once access is gained, the malware is installed and begins encrypting files. It uses a combination of AES-128 and RSA-2048 algorithms, ensuring strong encryption that is nearly impossible to break without the unique decryption key, which is stored on a remote server.
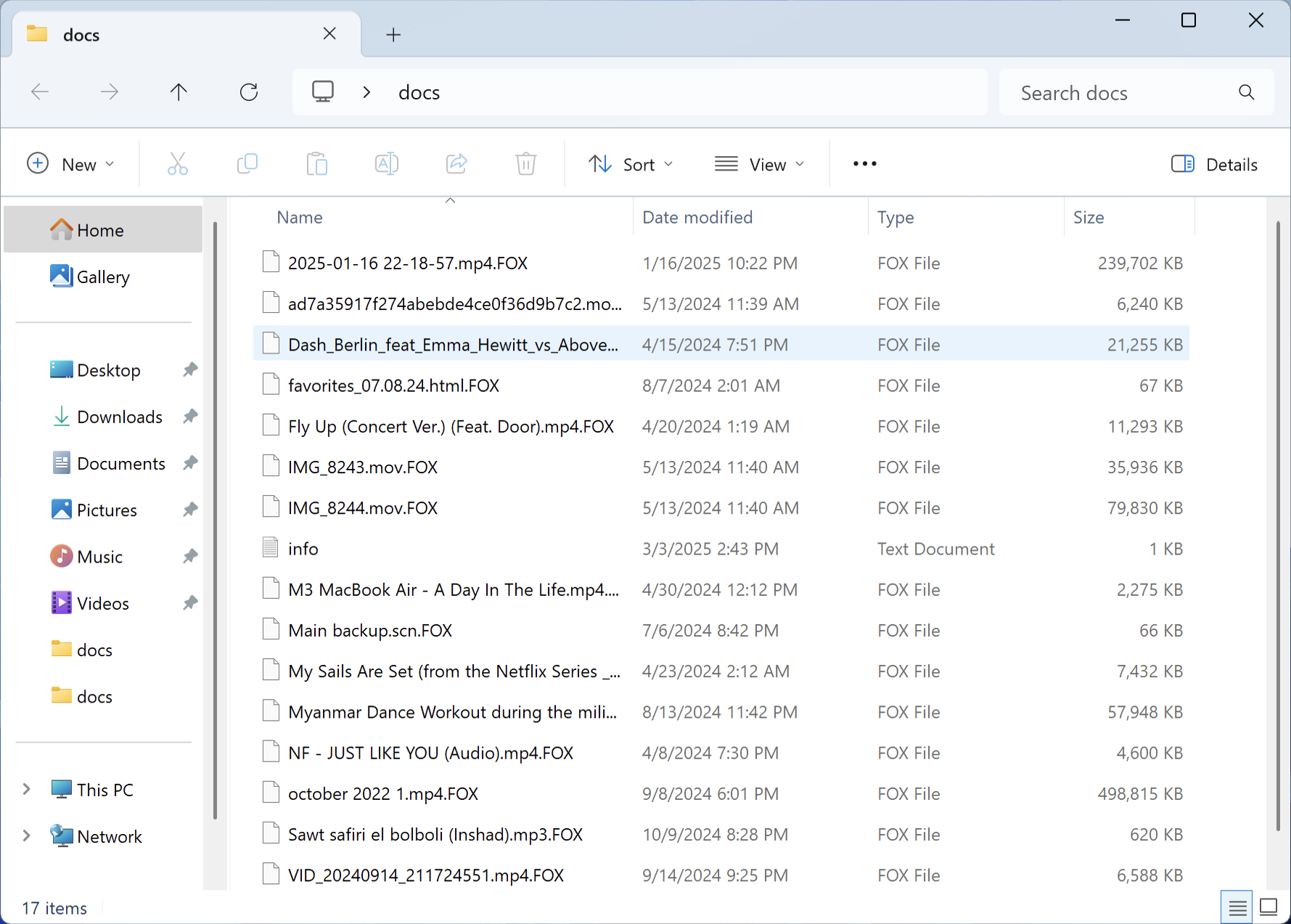
The encryption process involves renaming files, with Fox appending the .FOX extension. For example, a file named “document.pdf” might be renamed to “document.pdf.FOX”. Fox ensures persistence by copying itself to the %LOCALAPPDATA% directory and registering with Windows Registry Run keys. It also gathers location data and may exclude predefined locations from encryption. This thorough approach makes detection easier during encryption due to its slow process. However, by the time it is noticed, significant damage may already be done.
Ransom Note Overview
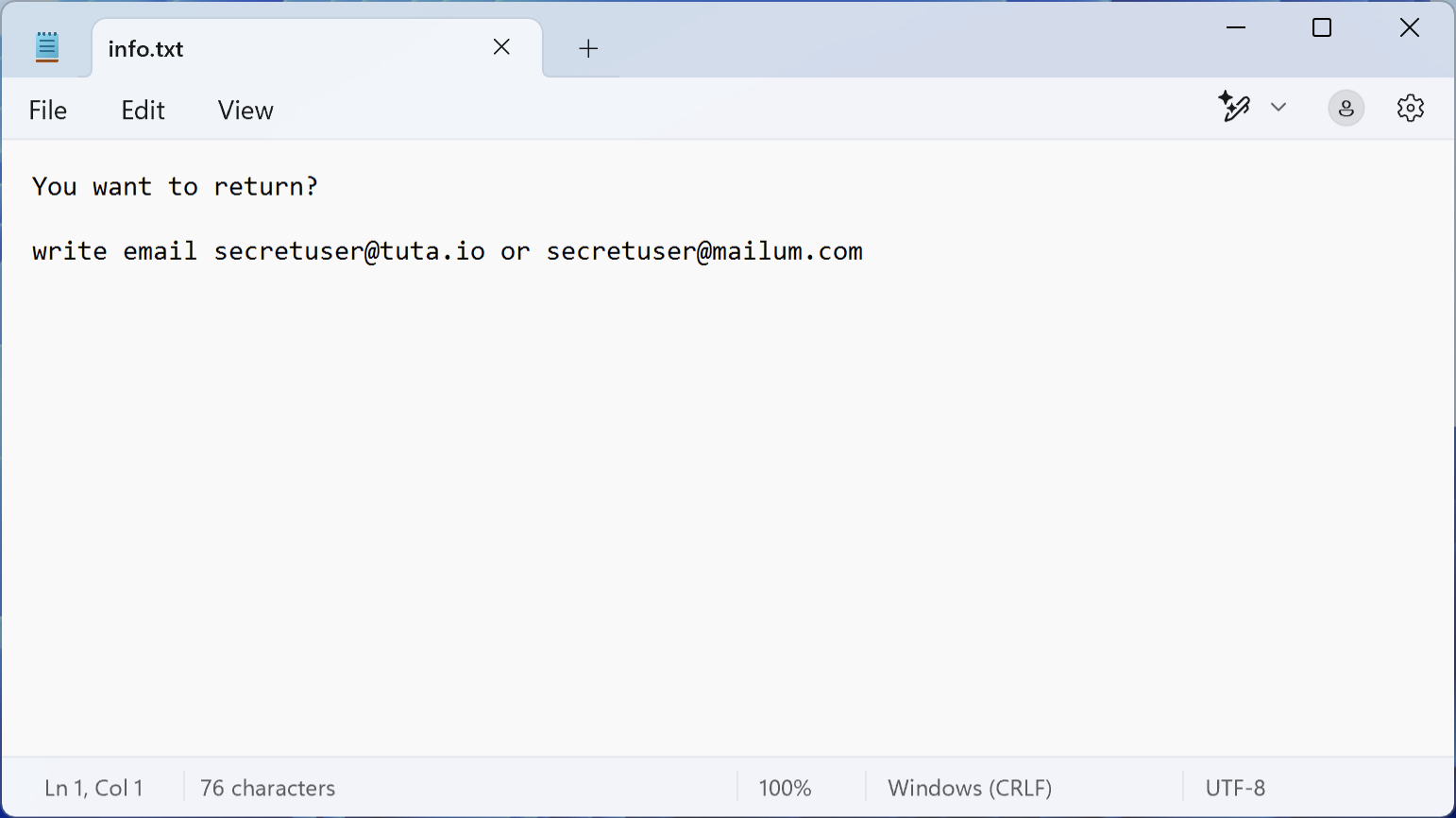
The ransom note for Fox ransomware is typically named #FOX_README#.rtf and is placed on the desktop, a common tactic within the Dharma family to ensure visibility. This note contains contact emails such as [email protected], [email protected], and [email protected]. It instructs victims that their files are encrypted with AES-128+RSA-2048 and demands payment, usually in Bitcoins, Monero, or other cryptocurrencies.
The ransom typically ranges from $500 to $1500, though exact amounts are provided via email. The note often sets a deadline, threatening data deletion if not paid within a specified period. This approach aligns with Dharma family’s tactics, where ransom notes vary by strain but consistently aim to extort money, leveraging fear and urgency. The use of multiple contact emails suggests a network of operators, potentially affiliates within the RaaS model, enhancing the family’s reach and profitability.
How to Remove Virus?
As other serious malware, removing Fox Ransomware requires a complex approach. The first step is to isolate the infected system by disconnecting it from the network or booting your Windows into Safe Mode. This prevents lateral movement and additional encryption, limiting the ransomware’s spread. Next, use GridinSoft Anti-Malware to detect and remove the threat all at one time, with a guarantee of it not returning. Download it by clicking the banner below and run a Full scan, so the program will scan the system down to the most remote corner.
After the attack, I would recommend you to keep GridinSoft Anti-Malware on the device, with its proactive protection enabled. This will ensure an immediate reaction on any phishy activity happening in your system. Keep all your software up to date: ransomware actors often use exploits to infect systems and networks, and updates often contain fixes for important flaws that you should not miss.
Can I Recover Encrypted .FOX Files?
File recovery for Fox ransomware victims depends on pre-existing measures and post-infection options. Without backups, recovery is challenging, as there are no known public decryption tools for Fox (Dharma) Ransomware. Some antivirus vendors offer decryption tools for specific ransomware families, but these are not guaranteed for Fox.
Paying the ransom is strongly discouraged, as research shows criminals often ignore victims post-payment, offering no positive result and potentially scamming users. This approach not only fails to guarantee file recovery but also fuels further criminal activity, with risks that attackers may not provide the decryption key, aligning with cybersecurity best practices to avoid funding cybercrime.
The most reliable method is restoring files from backups, provided they are stored securely off-site and not accessible to the malware during infection. Regular backups, maintained on remote servers or unplugged storage devices, are critical, as the malware can encrypt backups if stored locally.