The hacker, known as Nam3L3ss, posted the data of over 1000 corporations, leaked in 2023 during the active exploitation of MOVEit Transfer vulnerabilities. This includes smaller organizations along with giants like Amazon, McDonald’s, HSBC, and HP. There is a huge potential of this information being used for spam and other hacks.
Hacker Uploads Data Leaked in MOVEit Breaches
Back in 2023, attackers exploited a newly-discovered critical vulnerability in MOVEit. As a result, employee data from over 1,000 companies worldwide leaked, even the biggest names. But only now, more than a year after the mayhem, a hacker nicknamed Nam3L3ss, posted the compromised data on a cybercrime forum.
This breach was made possible by a vulnerability tagged CVE-2023–34362, identified in mid-2023. This flaw allowed attackers to bypass MOVEit’s authentication protocols, granting them unrestricted access to sensitive files. Since MOVEit is commonly used across sectors such as finance, healthcare, technology, and retail, the breach quickly escalated, becoming one of the largest data leaks recorded in recent years.
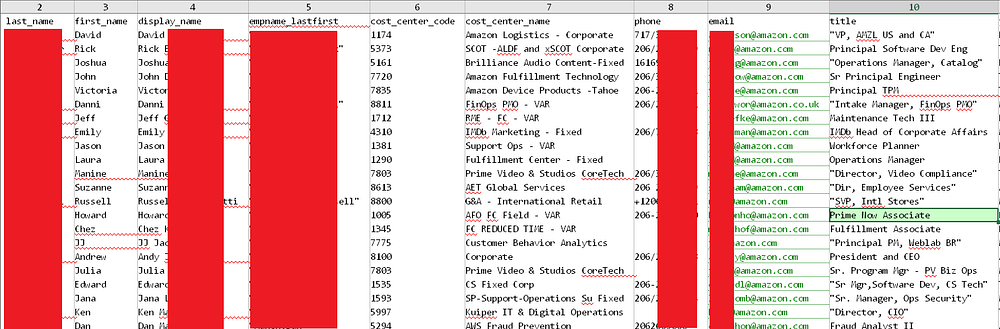
Hackers extracted extensive employee records from these vulnerable systems. They obtained names, email addresses, phone numbers, cost center codes, and internal organizational structures. As a result, all of which could fuel phishing, identity theft, or sophisticated social engineering attacks.
Scope of the Breach
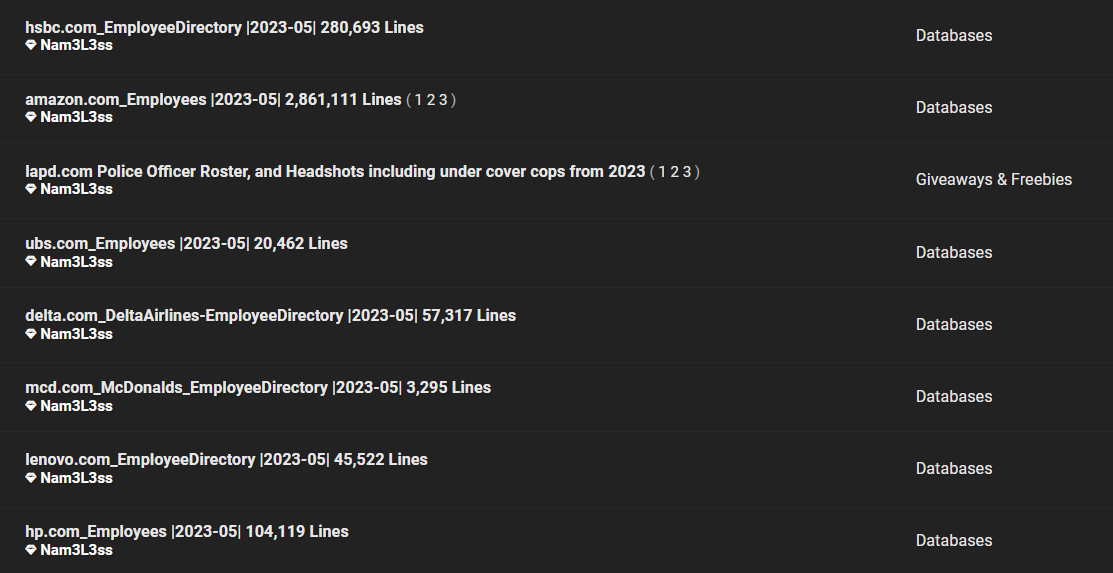
The breach affects a wide array of companies, with datasets organized by company and date-stamped as of May 2023. The data is comprehensive, containing millions of employee records across industries. It includes Amazon (2.86 million), MetLife (585,000), HSBC (280,000), HP (104,000), Canada Post, Delta Airlines, and 3M, with tens of thousands of records each.
List of allegedly compromised organizations
- Amazon
- MetLife
- Cardinal Health
- HSBC
- Fidelity
- U.S. Bank
- HP
- Canada Post
- Delta Airlines
- Applied Materials (AMAT)
- Leidos
- Charles Schwab
- 3M
- Lenovo
- Bristol Myers Squibb
- Omnicom Group
- TIAA
- Union Bank of Switzerland (UBS)
- Westinghouse
- Urban Outfitters (URBN)
- Rush University
- British Telecom (BT)
- Firmenich
- City National Bank (CNB)
- McDonald’s
With granular data fields like full names, email addresses, and job titles, the compromised data offers a detailed glimpse into corporate structures and personnel roles. For instance, Amazon’s dataset includes specific employee details like cost center codes and department names. HSBC’s data includes additional identifiers such as user IDs and city locations, stretching across the UK, India, and other regions. This fine-grained level of information increases potential risks even further, as it is a perfect basis for highly targeted cyberattacks.
Verification and Hacker’s Message
Hudson Rock, a cybersecurity research firm, confirmed the authenticity of the leak. They matched email addresses from the breach to LinkedIn profiles and cross-referencing them with known infostealer malware infections.
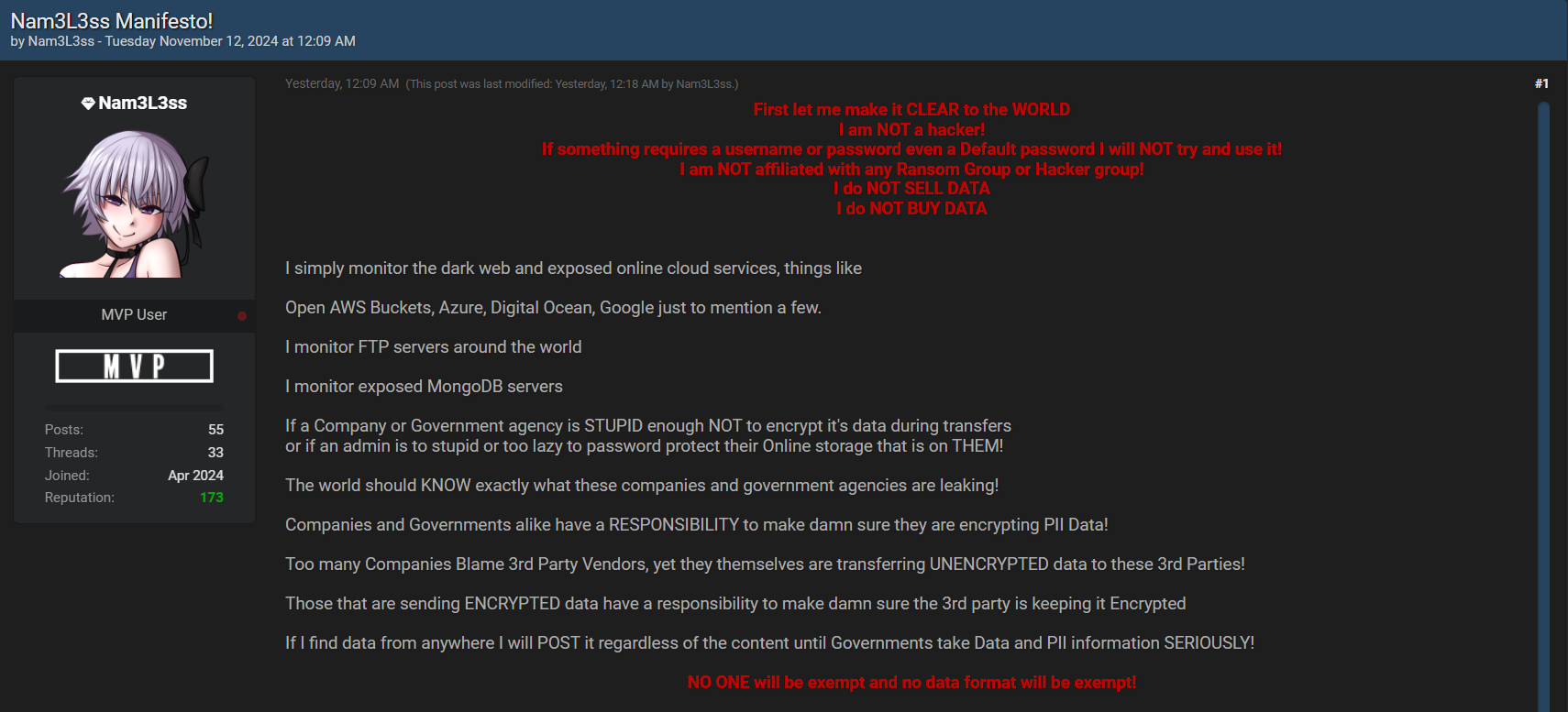
On the forum, Nam3L3ss themselves said they see a huge value in this data, due to how sensitive those details may be. The hacker also hinted that this breach represents just a fraction of the data they hold, with more possibly to be released soon.
Is CL0P Ransomware Involved?
CL0P ransomware gang was one of the hacker groups that massively used MOVEit’s vulnerabilities in their attacks. In 2023, they targeted several dozen companies that did not patch the flaw in time. However, it remains unclear if the recent leaks are tied to CL0P, its affiliates, or if Nam3L3ss independently exploited these companies. The hacker, as expected, did not share any information in this regard.
What Are the Potential Risks?
The breach presents a number of significant security risks to both the organizations affected and their employees. With access to comprehensive employee contact details and organizational structures, cybercriminals can craft convincing phishing emails aimed at individuals. Not only will these emails be convincing, but they will be hard to filter with regularly available spam and security. In turn, such emails can lead to further malware attacks.
The detailed internal corporate data can also be used for corporate espionage, from competitors or malicious actors. Both of these parties can gain valuable insights into internal company operations. For high-profile companies like Amazon and HSBC, the leak can lead to reputational damage. The financial sector is particularly vulnerable, with companies like Cardinal Health and UBS. Fraudsters can use the stolen contact information to target employees more effectively.





