Spring Framework has released an update that fixes the CVE-2024-38819 vulnerability, which potentially enables attackers to exploit HTTP requests for unauthorized file access.
CVE-2024-38819 Overview
The Spring Framework team has issued a patch for security vulnerability CVE-2024-38819. This is a path traversal vulnerability in the widely used Spring Framework. It carries a CVSS score of 7.5 and affects applications serving static resources via the WebMvc.fn or WebFlux.fn functional web frameworks. In brief, this flaw enables attackers to craft malicious HTTP requests to access files on the server’s file system that are accessible to the same process running the Spring application.
As for the risks this vulnerability poses, it primarily threatens corporations that use the framework to develop their apps and handle auxiliary data. Firstly, it could result in the leakage of proprietary code, whether partially developed or fully completed closed-source projects. Secondly, it could expose users’ personal data that is used in those applications, as Spring supposes handling databases as well.
Spring Framework is a popular open source framework for building Java applications. It offers many modules and tools that simplify common tasks such as dependency management, security, working with databases, and building web applications.
Technical details
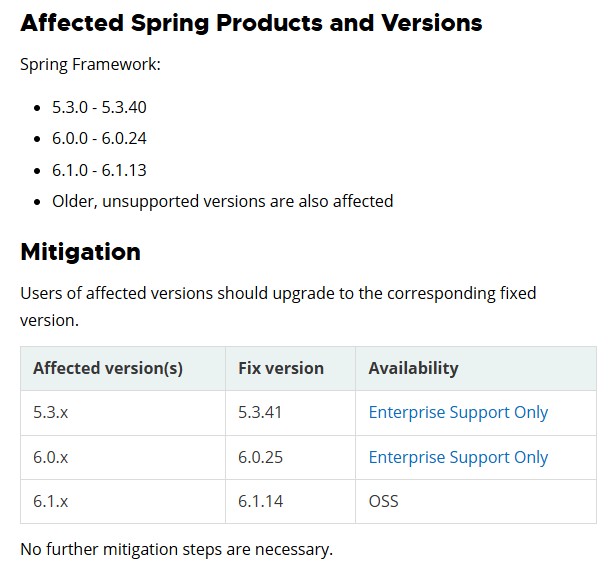
The vulnerability was responsibly disclosed by Masato Anzai of Aeye Security Lab, Inc. along with another anonymous researcher. It impacts various versions of the Spring Framework, ranging from 5.3.0 to 5.3.40, 6.0.0 to 6.0.24, and 6.1.0 to 6.1.13, along with older, unsupported releases. CVE-2024-38819 stems from improper input validation in applications that serve static resources using Spring’s WebMvc.fn and WebFlux.fn frameworks. This improper validation enables directory traversal attacks, where a remote attacker can exploit the application by sending specifically crafted HTTP requests.
In turn, these crafted requests can bypass file system protections, granting access to sensitive files. These could be configuration files, logs, or credentials that are readable by the application’s process. In simpler terms, an attacker can use crafted HTTP requests to gain access to arbitrary files.
The number of potential victims is quite concerning, with almost 32 thousand services being exposed to the Web. And that is only a conservative estimate, as there may be more of them that were just missed by search engines, or ones that hackers could access from within the enterprise network. All users of this software solution should check whether they are using the flawed version and, if so, install the required updates.
Mitigation Guidance
Although there are no reports of active exploitation in the wild, users are advised to upgrade to patched versions of the Spring Framework. There are no workarounds or alternatives that provide complete protection against CVE-2024-38819. So, users of versions 5.3.x, 6.0.x, and 6.1.x should immediately upgrade to versions 5.3.41, 6.0.25, and 6.1.14, respectively, to prevent potential exploitation. Spring Boot commercial users can also utilize the Spring Boot Hotfix release for additional protection.




