Trojan:Win32/Qhosts is malware that provides remote access to the target system and modifies the Hosts file. It is primarily distributed through illegal activation tools found on torrent and warez sites. While the mentioned interaction with the system configuration file as a definitive feature, it is capable of much, much more unpleasant activities.
Trojan:Win32/Qhosts Overview
Trojan:Win32/Qhosts is a Microsoft Defender detection for dropper malware or remote-access trojans. Such malware is made to provide access to an infected system and deliver a payload. It is known for modifying the HOSTS system file, which is used to map hostnames to IP addresses. By doing so, it can provide itself with stable connectivity to the command server. In some cases, it does this to prevent the user from accessing antivirus vendors’ websites and getting security updates from Microsoft.
This malware is typically spread through dodgy software, like unauthorized activation tools, keygens and the like. Depending on the version, Trojan:Win32/Qhosts may block access to various services and sites, including those of Adobe and Microsoft. This partly explains its actions concerning the HOSTS file but does not account for its remote access capabilities. Sometimes, it also prevents antivirus software from accessing the Internet. This happens particularly often to software of renowned security vendors, whose server addresses are well-known.
Technical Analysis
Let’s get into the behavior analysis of Trojan:Win32/Qhosts using a specific instance as an example. In this case, it is a Windows activator, which has both its declared functionality and hidden malicious features. We’ll start with its launch, which is initiated by the user. Since this is an activator, it implies that the anti-malware software on the system must be disabled for its use. Despite this, the program performs standard checks for the presence of sandboxing/debugging or anti-malware software. It checks the following registry values:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows
HKEY_LOCAL_MACHINE\Software\Policies
HKEY_LOCAL_MACHINE\System\Setup
C:\Program Files (x86)\Common Files\Oracle\Java\javapath\
C:\Program Files (x86)\Windows Defender\MpClient.dll
C:\Program Files (x86)\Windows Defender\MpOAV.dll
C:\Program Files (x86)\Windows Defender\MsMpLics.dll
C:\Program Files\Windows Defender\MsMpLics.dll
C:\ProgramData\Microsoft\Windows Defender\Platform\4.18.2102.4-0\X86\MpOav.dll
Delivering the Payload
The malware then drops files into the system’s temporary directory. Among these files are both the payload and the files necessary for Windows activation. Regarding the former, the files include:
C:\Users\user\AppData\Local\Temp\RarSFX0\Install.cmd
C:\Users\user\AppData\Local\Temp\RarSFX0\bin\bootsect.exe
C:\Users\user\AppData\Local\Temp\RarSFX0\bin\grldr
It also drops a large number of certificates into the folder C:\Users\user\AppData\Local\Temp\RarSFX0\certs.
Malicious Activity
Next, the malware creates several new processes from the temporary folder, then creates and runs additional executable files.
C:\Users\
C:\Users\
The malware then executes Visual Basic scripts (install.vbs) using cscript.exe:
cscript //nologo "C:\Users\
cscript //nologo C:\Windows\system32\slmgr.vbs -ipk HERE-GOES-WINDOWS-ACTIVATION-KEY
As you might have guessed, this script installs a license key into the system. That is actually one of the dangers of this malware: the victim sees the system activation process and thinks everything is fine. But meanwhile, the malware does its dirty job in the background.
Gaining Persistence
The actions of the program do not end there; the malware continues with establishing persistence in the system. This specific sample appears to work as a dropper, so maintaining constant access to the system is crucial. To achieve this, it modifies settings in HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows and other system-level keys to ensure it can survive reboots and maintain control over the system. Additionally, the malware manipulates the following keys:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{E8433B72-5842-4d43-8645-BC2C35960837}.check.100\CheckSetting
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{E8433B72-5842-4d43-8645-BC2C35960837}.check.101\CheckSetting
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{E8433B72-5842-4d43-8645-BC2C35960837}.check.102\CheckSetting
The first four keys are associated with checks performed by the Security and Maintenance feature in Windows. Each “CheckSetting” entry can correspond to specific checks such as firewall status, antivirus status, etc. This information also goes as a part of system fingerprinting – action that all malware does to distinguish attacked systems.
Hosts File Manipulation
The malware then proceeds to manipulate the hosts file. To do this, it creates a specific registry key:
HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX\C%%Windows%System32%drivers%etc
This key is associated with self-extracting WinRAR archives. Based on the path, it is linked to a WinRAR operation affecting the hosts file. The malware drops a temporary file named __tmp_rar_sfx_access_check_34985937, which WinRAR creates during the extraction process of the self-extracting archive (SFX). The filename indicates a temporary access check to ensure the program has sufficient rights to overwrite the hosts file in this directory. Subsequently, the malware replaces the Hosts file with the one it needs.
This could be done for several reasons:
- To prevent the system from contacting the license verification server, ensuring that the illegal activation remains in place.
- To block system or anti-malware updates.
- To redirect the user to fraudulent websites.
How To Remove Trojan:Win32/Qhosts?
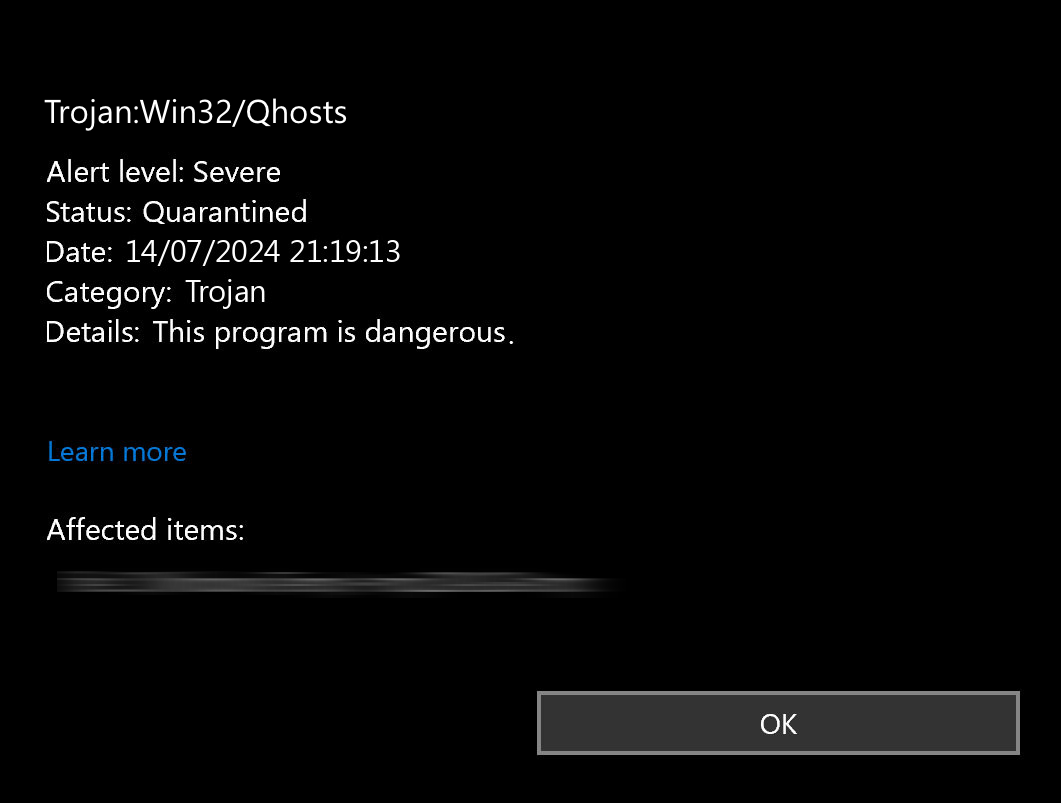
Removing Trojan:Win32/Qhosts involves several steps and requires an advanced anti-malware solution. GridinSoft Anti-Malware is the one that you can rely on in this question. Initially, you need to clean the system of malware. After cleaning the system, you need to restore the hosts file. Follow the instructions below for each of the steps.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Restore the Hosts File
- Go to the Tools tab and click Reset Browser Settings.
- Uncheck all boxes except for the one next to the HOSTS file and click Reset.
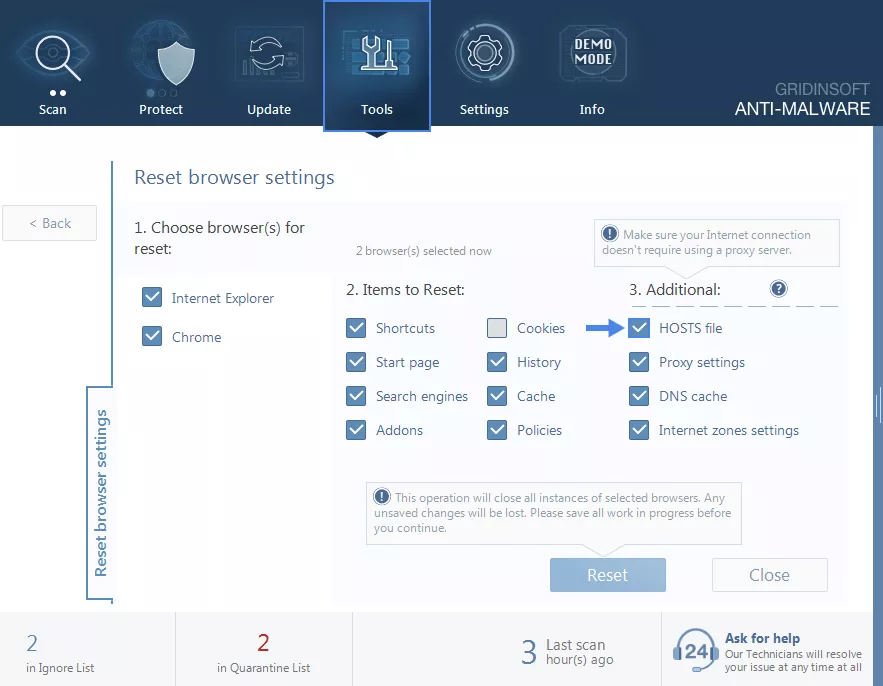
By following these steps, your system will be fully restored and ready for use.