The Security Blog From Gridinsoft
Hackers Can Use ChatGPT Hallucinations to Distribute Malicious Packages
According to vulnerability and risk management company Vulcan Cyber, attackers can manipulate ChatGPT to distribute malicious packages to software developers.…
Microsoft Researchers Link Clop Gang to MOVEit Transfer Attack
Microsoft has linked the Clop ransomware gang to a recent attack that uses a zero-day vulnerability in the MOVEit Transfer…
ChatGPT has become a New tool for Cybercriminals in Social Engineering
Artificial intelligence has become an advanced tool in today’s digital world. It can facilitate many tasks, help solve complex multi-level…
The AI-Controlled Drone Did Not “Kill” Its Operator Even During the Simulation. At Least for Now
At the recent Future Combat Air and Space Capabilities summit, the head of AI testing and operations at the US…
Russian Hacker Sells Terminator Tool That Is Allegedly Able to Bypass Any Antivirus Programs
A tool called Terminator appeared on one of the Russian hacker forums, and, according to its author, can destroy any…
Hackers majorly use Microsoft and DHL brands in phishing attacks
Hackers majorly use the Microsoft and DHL brands in phishing…
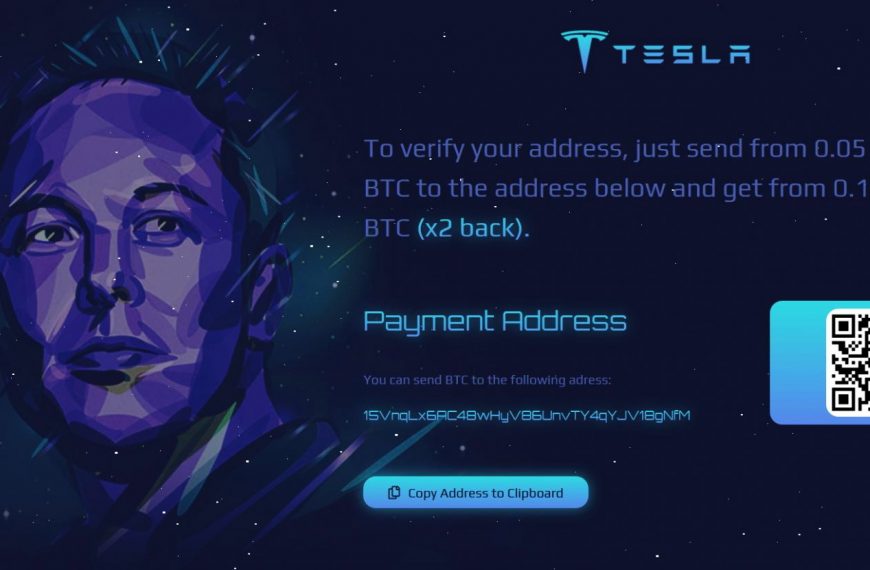
Fake cryptocurrency giveaways on behalf of Elon Musk brought scammers $580,000
The media have repeatedly written that scammers sometimes impersonate famous…
Google experts exposed sophisticated hacking campaign against Windows and Android users
Google published a large report detailing how they exposed a…
Experts discovered SolarLeaks website with data stolen in a recent massive hacker attack
Bleeping Computer reports the discovery of the SolarLeaks website (solarleaks[.]net),…
Extortionists hack into Cellmate men’s chastity belts
Last fall, researchers from Pen Test Partners reported on the…
Nissan source code leaked due to admin: admin credentials
The source code for mobile apps and internal tools for…
Storming of the US Congress poses a serious threat to cybersecurity
Storming of the US Congress in Washington, in addition to…
Researcher discovered vulnerability in Telegram, which allows to locate user
The researcher discovered a vulnerability in Telegram. The fact is…
Millions of Windows 7 users refuse to upgrade to Windows 10
In early 2020, Microsoft officially ended support for the Windows…
Nintendo spied on a hacker who prepared attack on the 3DS console
The TorrentFreak magazine reported about leaked documents that shed light…
Microsoft says SolarWinds hackers hunted for access to cloud resources
Microsoft continues to investigate the supply chain attack that SolarWinds…
New web skimmer found in Shopify, BigCommerce, Woocommerce and Zencart stores
Sansec experts have discovered a new multi-platform MageCart skimmer capable…