Sonatype identified four npm packages that collected and sent to their creator’s data about user machines, such as IP addresses, computer username, home directory path, processor model, and country and city information.
The discovery originally made Sonatype malware detection robots that scan millions of applications.
“Following alerts from the Sonatype bots, our security research team verified the presence of malicious code in npm packages and traced the intended exploit path”, — told Sonatype specialists.
npm (Node Package Manager) — this is the package manager included with Node.js.
The malicious code was found in the following packages:
- electorn: 255 downloads;
- lodashs: 78 downloads;
- loadyaml: 48 downloads;
- loadyml: 37 downloads.
All four packages were developed by the same author (simplelive12) and uploaded to the npm portal this August. Two packages (lodashs and loadyml) were removed by the author shortly after publication, soon after they infected users.
The remaining two packages (electorn and loadyaml) were removed last week, on October 1, 2020 by the npm security team following the publication of the Sonatype report.
As you can see, to attract users, all malicious packages used typosquatting, namely, in their names were deliberately misspelled names of other popular packages (this is how users are most often typed in).
All malicious packages collected from infected machines were published as new comments in the Issues section of the GitHub repository.
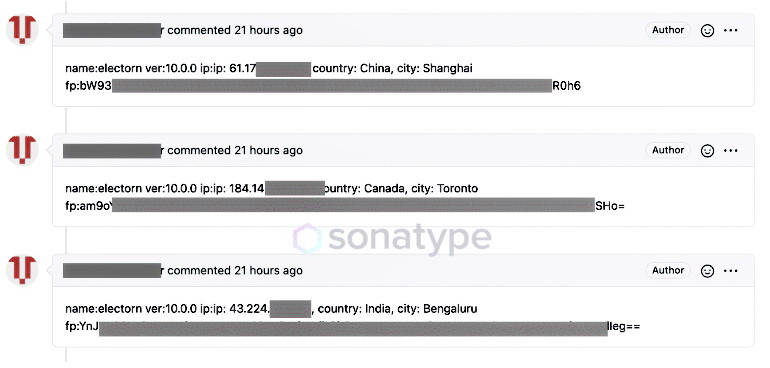
The researchers write that, most likely, we will not know what was the ultimate goal of this campaign.
“The essence of the malicious behavior lies in the “update()” function which is called every hour. The function uploads all of this collected information to a public page on GitHub. But nowhere in the file are any obvious URLs present”, — tell the experts about one of the detected malicious packages.
It was probably someone’s reconnaissance operation. Thus, the collected data helped to understand whether the victim works from home or is in a corporate environment.
The home directory path and CPU model could have been used to fine-tune and deploy malware for a specific architecture. In essence, for the next stage of the attack, the attacker only needed to update the electorn and loadyaml packages and equip them with additional malicious code.




