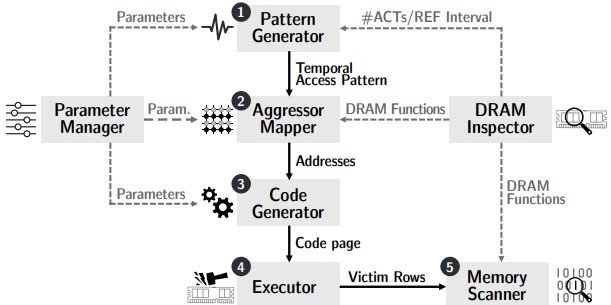
Researchers have unveiled a new fuzzing attack technique, Blacksmith, which proves that a Rowhammer attack on DDR4 memory is possible and bypasses existing defense mechanisms. It is worth noting that many of the authors of this work have previously participated in the creation of a similar TRRespass attack.
Let me remind you that the original Rowhammer attack was invented by experts from Carnegie Mellon University back in 2014. Its emergence relates to the fact that a certain effect on memory cells can lead to the influence of electromagnetic radiation on neighbouring cells, and the values of the bits in them will change.
Over the years, researchers have managed to prove that a wide variety of memory can be vulnerable to Rowhammer attacks, and they learned how to exploit the attack through JavaScript, and managed to adapt it against Microsoft Edge and Linux virtual machines. There is even a variation of Rowhammer, which poses a threat to Android devices, and we learned how to increase the effectiveness of attacks using video cards.
In response, manufacturers have implemented Target Row Refresh (TRR), a combination of various software and hardware fixes created over the years, into their products. Basically, these mechanisms were effective and they were enough to protect the then new DDR4 memory.
However, last year, experts managed to bypass TRR using the TRRespass attack, which is also based on fuzzing and allows using the good old Rowhammer problem against modern and secure products.
But if the TRRespass attack was effective against 14 out of 40 DIMMs tested, achieving 37.5% success, the new Blacksmith attack demonstrates effective Rowhammer patterns for all 40 DDR4 DIMMs. The fact is that this time the researchers did not approach the hammering patterns uniformly, but instead used uneven structures to bypass the TRR. According to experts, Blacksmith generates an average of 87 times more coups than other attacks.
To prove that these attacks can be applied in real life, a team of experts conducted tests that allowed them to obtain private keys for the RSA-2048 public keys used for SSH authentication.
It should be noted that DDR5 modules already available on the market are still safe, since they replace TRR with a refresh management system, which makes scalable fuzzing much more difficult.
Let me remind you that we also said that Trojan Source attack is dangerous for compilers of most programming languages.




