The Microsoft Tech Support Scam has recently gained popularity as a new sector of cyber attacks. Scammers, masquerading as Microsoft Technical Support, pressure internet users into calling a supposedly toll-free phone number. Contrary to their claims, this number incurs significant charges, enabling fraudsters to profit from each call made.
Responding to numerous claims from our users about these cyber attacks, we have conducted a detailed investigation into this fraudulent scheme. In this post, we will answer the most frequently asked questions about Microsoft Tech Support scammers. Being forewarned is being forearmed! We encourage you to stay vigilant to the signs and protect your safety while browsing. Do not allow scammers to exploit your fears!
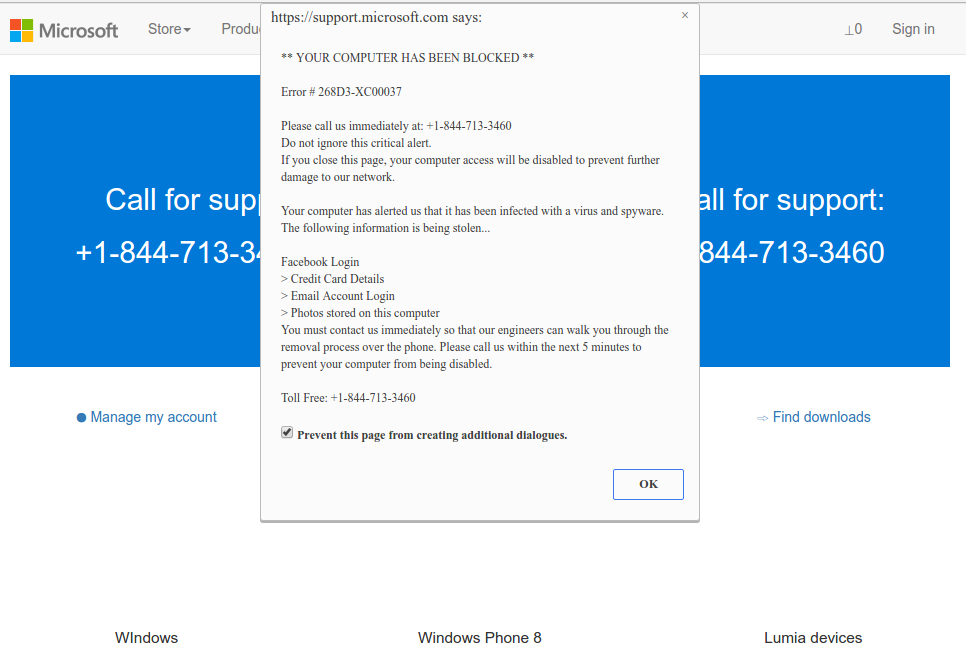
How Do Scammers Intimidate People?
Hackers employ various tactics to intimidate their victims, aiming primarily to profit. Fraudulent landing pages can switch to full-screen mode, disable main keys, and prevent the context menu from opening. Scammers can easily execute these actions using the following JavaScript code:
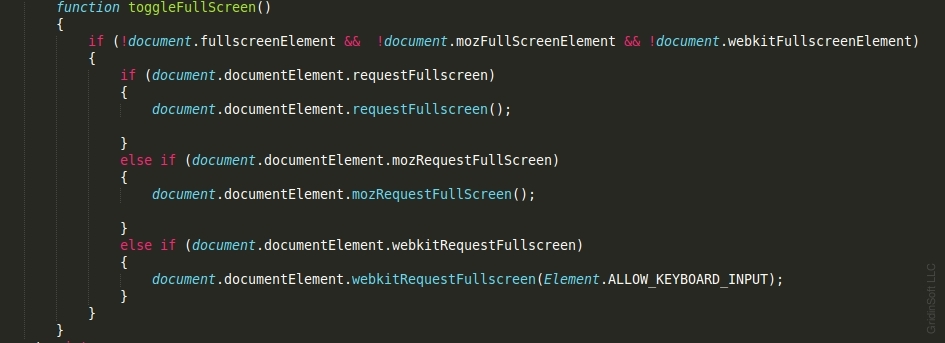
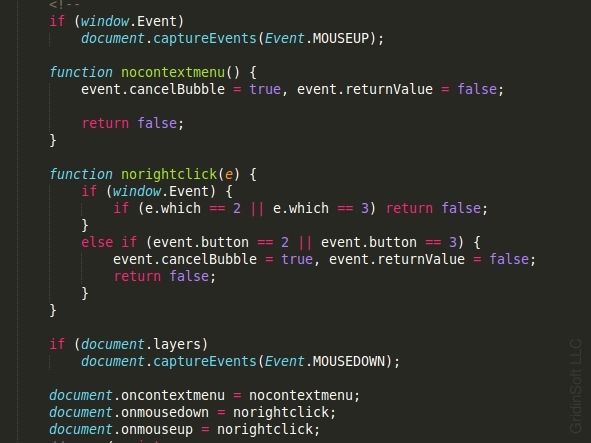
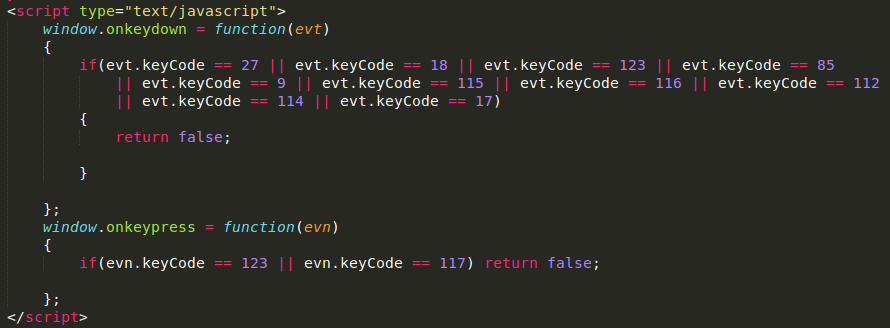
Interestingly, fraudsters even integrate Google Analytics into their malicious web pages!
The horrible text messages are not the only thing which scammers are using to terrify their victims. There are also threatening voice notifications played. Usually, they are stored here:
However, terrifying text messages are not the only tool scammers use to intimidate their victims. They also employ threatening voice notifications. Typically, these audio files, such as alert messages, are hosted at URLs like this:
MALICIOUS_URL/chrm/alert2.mp3
If you ever come across these scare tactics, remain calm and recognize that there is no real danger as long as you avoid calling the “free” phone number provided by the fake technical support team.
Microsoft Tech Support Scam: Scam-as-a-Service
The landing pages that our users unfortunately encountered are just the tip of the iceberg. In the world of cybercrime, Malware-as-a-Service has flourished for a long time. These newer scam techniques can aptly be termed Scam-as-a-Service.
On a recently discovered semi-private Russian underground forum, exploit.in, we came across a description of an affiliate program:
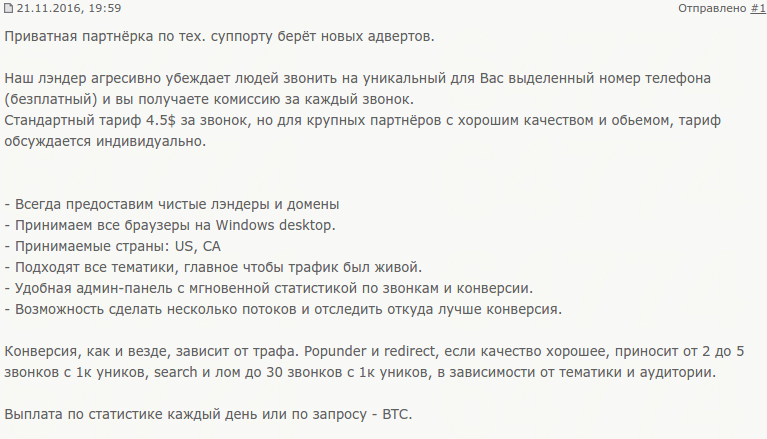
English translation:
- Always provide clean landings and domains.
- Accept all browsers for the Windows desktop.
- Accepted countries: US, CA
- All subjects are suitable, the main thing was that the traffic was alive.
- Handy admin panel with the instant statistics of calls and conversion.
- The ability to make multiple streams and their conversion’s comparison.
Conversion, as elsewhere, depends on the traffic’s quality. If the quality is good, the popunder and the redirect bring from 2 to 5 calls from 1k unique visitors. The search and scrap bring up to 30 calls from the 1k unique visitors, depending on the subject and the audience. You’ll get your payments every day or O/R – BTC. The usual working time is from 19:00 to 02:00. But, it’s highly recommended to ask the support if it has changed each time before delivering the traffic.
As you can see from the description, the scheme is quite straightforward: the creators of the affiliate program provide publishers with domains, admin panels with statistics, and payments through BTC, which has become the standard currency in the cyber underworld. Publishers simply need to direct traffic to these affiliate domains and then wait for their profits.
Could Google Eliminate Microsoft Tech Support Scam Fraud?
Google can effectively mitigate such aggressive scams by adding fraudulent landing pages to its Google Safe Browsing filters. However, scammers are relentless. They frequently register a large number of similar domains with names that subtly reference Microsoft to perpetuate their schemes:
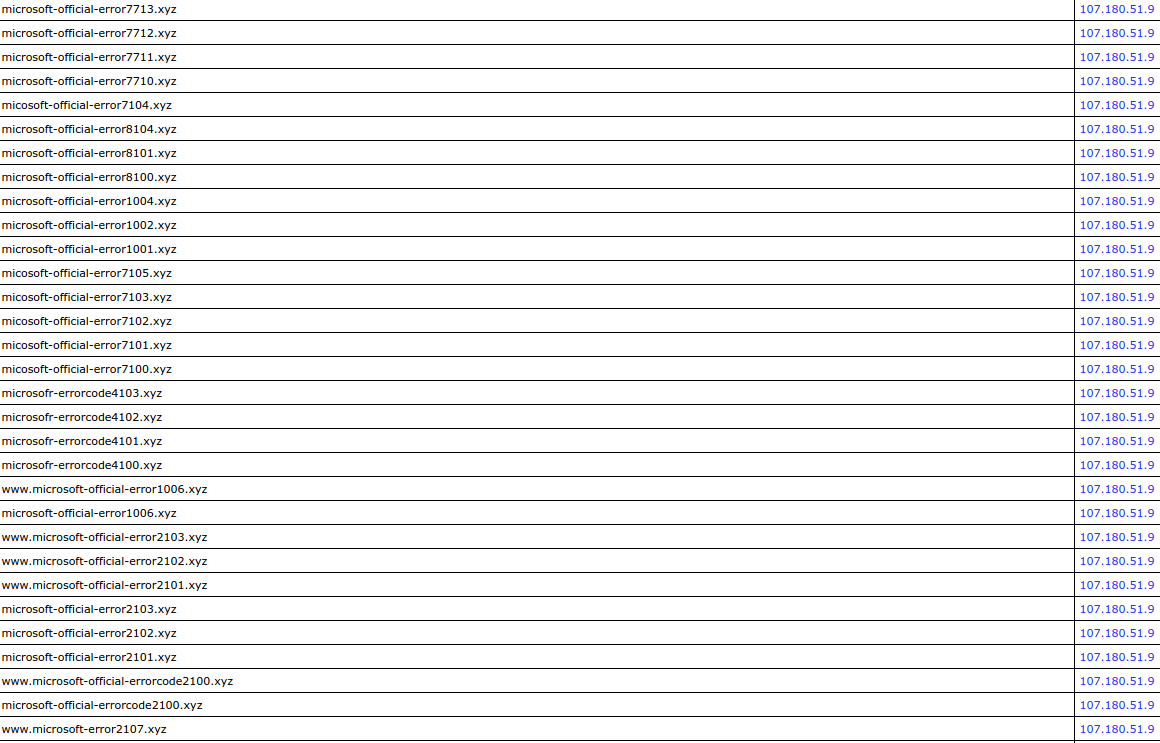
It is important to remember that the lifespan of individual scam pages is usually very short. They should not cause undue alarm.
What Happens to Those Who Made the Call?
All scam pages involved in this scheme share the same phone number: +1-844-713-3460. We have collected typical user complaints about this number:
A message popped up on my computer: “Microsoft-error4113.xyz says: *** YOUR COMPUTER HAS BEEN BLOCKED ***” and it warned that personal information was being stolen, including my photos. It threatened to disable my computer within five minutes and provided this number to call. This is a SCAM! The signs include Microsoft spelled in lowercase, an error code that doesn’t align with legitimate ones, and the overt threat. When I researched this number on another reporting site, I found a person who mentioned that his mother had made the mistake of calling and allowing them remote access to her computer—they changed her passwords and hijacked it, demanding money to release it! BAD MOJO!!!
While using my computer, this number appeared with a message saying, “Critical Alert from Microsoft.” I called the number back, and the person on the line wanted access to my computer to ‘fix’ the problem, threatening to shut down my computer if I did not comply. We denied access. The error message linked to this number was Microsoft error 3111.xyz.
As the complaints suggest, the scammers’ objective is to coerce victims into granting them full access to their computers for further intimidation. You should never allow access to your system to anyone you don’t know, especially if they are performing these questionable activities independently.
Conclusion
The Microsoft Tech Support Scam is a new, widespread scheme in the cybercrime world. Scammers capitalize on users’ fears by employing simple scare tactics, typically involving disabled keys, full-screen modes, and alarming audio messages. We hope this information convinces you to not give in to such threats. Such deceptive and rudimentary schemes do not deserve your attention or financial support!





