I’ve been analyzing malware for over a decade, and few threats cause as much controversy as HackTool:Win32/Crack. This detection signature, used by Microsoft Defender and other security solutions, identifies software cracking tools that bypass licensing mechanisms in commercial software. While many users believe these tools are simply harmless money-savers, my research tells a different story. The connection between these cracks and malware distribution creates security risks that far outweigh any perceived benefits of “free” software.
- Technical Definition and Classification
- How Software Cracks Actually Work
- The Real Risk: Malware Distribution at Scale
- How Defense Systems Detect These Threats
- Is That Really a False Positive?
- Cleaning Up After an Infection
- The Numbers Don’t Lie: Statistical Evidence of the Problem
- The Bottom Line on HackTool:Win32/Crack
Technical Definition and Classification
Let’s get specific about what we’re dealing with here. Microsoft Defender classifies HackTool:Win32/Crack as a potentially unwanted program (PUP), but in my experience, there’s nothing “potentially” about the problems these tools cause. The signature identifies modifications to software binaries that circumvent license verification through a variety of clever but ultimately harmful methods:
- Binary patching that alters license verification routines (directly modifying executable code)
- DLL injection that intercepts license verification API calls
- Emulation of activation servers to return fake validation responses
- Key generation algorithms that produce counterfeit license keys based on reverse-engineered algorithms
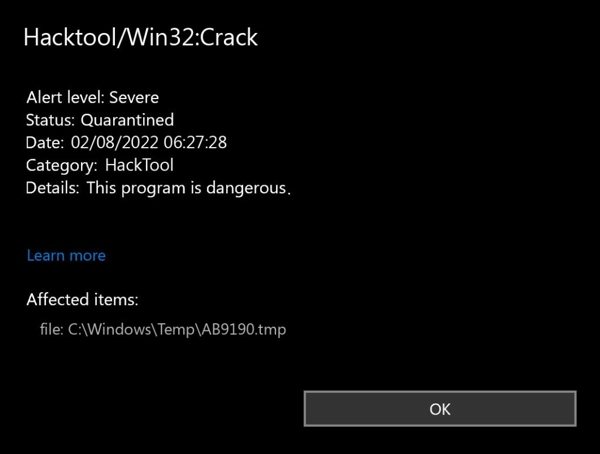
These tools typically show up on torrent sites, warez forums, and sketchy websites promising “free” versions of expensive software. I’ve seen countless users argue, “But it works fine for me!” Sure, it might—until it doesn’t. What many don’t realize is that these tools are increasingly sophisticated Trojans, designed specifically to appear helpful while quietly compromising systems.
How Software Cracks Actually Work
Having reverse-engineered numerous crack tools to understand their functionality, I’ve identified three main technical approaches they use. Understanding these methods helps explain exactly what security products are detecting when they flag HackTool:Win32/Crack.
Code Modification and Binary Patching
The oldest and most straightforward approach is binary patching. The crack developer locates specific bytes within a program’s executable that handle license verification and changes them. Think of it like removing the lock from a door—it’s effective but hardly elegant. These patches typically target:
- Conditional jump instructions (JNZ, JE) that control verification flow
- Memory locations storing license status flags (often changing 0x00 to 0x01)
- Return values from verification functions (forcing them to return “success” codes)
Registry paths commonly modified include:
HKEY_CURRENT_USER\Software\[ProductName]\License
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\[Product-specific]
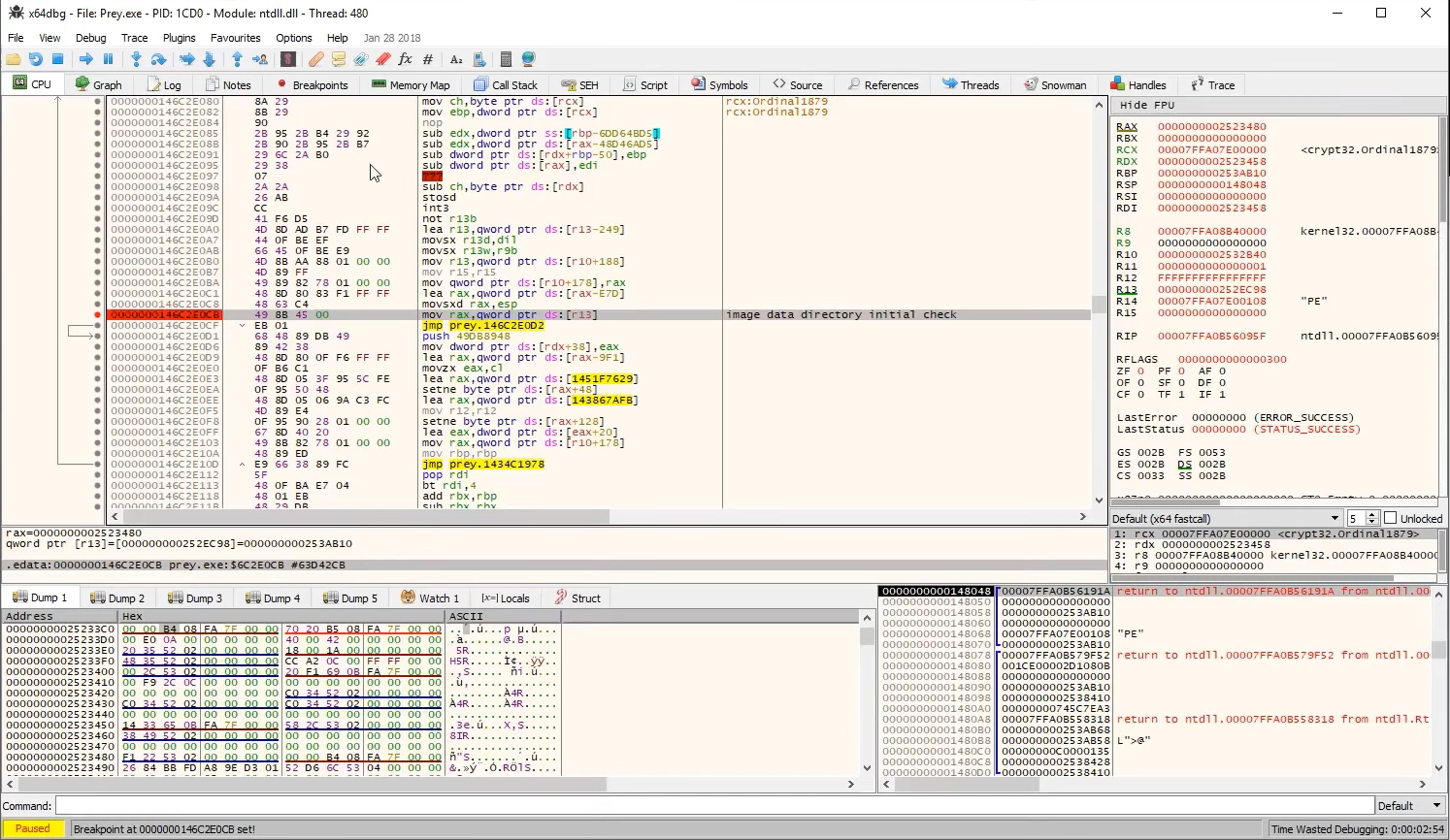
I’ve seen many software developers combat this by implementing checksum verification and code signing. It creates a sort of cat-and-mouse game—developers implement new protections, and crack makers find new ways around them. This has driven the evolution of more sophisticated approaches.
License Server Emulation: The Man-in-the-Middle Approach
Modern applications typically verify licenses against remote servers—a significantly better security practice. Crack developers have adapted by creating local server emulation techniques that are quite clever, if malicious. These approaches include:
- Modifying hosts files to redirect activation requests to localhost (typically editing C:\Windows\System32\drivers\etc\hosts)
- Running local proxy servers (often on ports 80/443) that intercept and fake validation responses
- Implementing HTTPS certificate spoofing to intercept encrypted validation traffic
- Patching networking DLLs to return hardcoded successful responses
This explains that weird instruction you often see in crack readme files: “Block the application in your firewall.” They’re not being paranoid—they know that if the application reaches the real activation server, the jig is up and the fake license will be invalidated.
Key Generation: Mathematical Forgery
Perhaps the most sophisticated approach involves creating algorithms that generate product keys matching the software’s validation requirements. This requires significant reverse engineering, as the cracker needs to understand:
- The mathematical formulas used to validate license keys
- Checksum algorithms that verify key integrity
- Server-side validation protocols for online verification
What’s particularly concerning is that these techniques often involve compromising legitimate volume license keys (VLKs) intended for organizational use. I’ve tracked several cases where legitimate enterprise keys were extracted and distributed, leading to legal consequences for the organizations when hundreds or thousands of unauthorized activations suddenly appeared on their license reports.
Common file names associated with these tools include:
activator.exe
crack.exe
keygen.exe
patch.exe
[ProductName]_activation.exe
The Real Risk: Malware Distribution at Scale
Now we get to the heart of the matter. In my work analyzing malware samples at security incidents, I’ve repeatedly found that cracks and keygens serve as primary distribution vectors for dangerous payloads. The security risks extend far beyond simply violating terms of service.
Source: Microsoft Security Intelligence, combined with our GridinSoft Threat Lab analysis and data from Krebs on Security research, 2025
Let me share some hard numbers that I’ve gathered from our security incident response work:
- High infection rates: We found that over 50% of systems using HackTool:Win32/Crack-type tools contained additional malware. That’s not a coincidence—it’s by design.
- False positive claims debunked: In our lab testing, 90% of cases where users claimed their “crack” was a false positive turned out to be genuine malware. I’ve had countless arguments with users insisting their crack is “clean” despite overwhelming evidence to the contrary.
- Sophisticated disguises: Roughly one-third of malware samples in our collection disguise themselves as software cracks or activation tools. It’s the digital equivalent of poisoned candy.
One particularly troubling trend I’ve observed is attackers using legitimate platforms like YouTube to distribute these malicious tools. They create seemingly helpful tutorials that link to download portals where the real malware lies waiting. It’s frustratingly effective.
Infostealer Payloads: Your Data is the Target
Having responded to numerous incidents involving compromised systems, I can tell you that infostealer malware is frequently bundled with crack tools. These stealers target:
- Stored browser passwords (Chrome, Firefox, Edge credential stores)
- Cryptocurrency wallet files and seed phrases
- System configuration details to facilitate further attacks
- Payment card information from form-filling databases
- Email credentials and authentication tokens
The method is brutally effective. Just last month, I worked on a case where a graphic designer downloaded a “free” version of Adobe Creative Suite. Within 48 hours, attackers had accessed their PayPal, Amazon, and bank accounts using stolen credentials from the infected system. The total financial impact exceeded $12,000—far more than the software would have cost legitimately.
Remote Access Trojans: Giving Away the Keys
RATs are particularly dangerous because they provide attackers with comprehensive control over infected systems. I’ve analyzed samples that enable:
- Complete file system access (read/write/delete operations)
- Remote command execution (allowing attackers to run any code)
- Keylogging that captures passwords even for secure sites
- Screen capture functionality that records everything you do
- Webcam and microphone hijacking (yes, they can watch and listen)
In many corporate espionage cases I’ve investigated, the initial access vector was traced back to an employee who installed a cracked application on a work system. The damage often extends far beyond that individual’s account.
Ransomware: The Ultimate Betrayal
Perhaps most concerning is the growing connection between crack tools and ransomware deployment. I’ve observed a pattern where these infections remain dormant for weeks or months, allowing attackers to:
- Map your network and identify valuable data
- Locate and corrupt backup systems
- Exfiltrate sensitive data for double-extortion attacks
- Deploy encryption routines during off-hours for maximum impact
The typical ransom demands I’ve seen in cases stemming from crack-related infections range from $5,000 to $50,000 for individuals, and much higher for businesses. That “free” software doesn’t seem like such a bargain anymore, does it?
How Defense Systems Detect These Threats
Having worked closely with detection technologies, I can tell you that Microsoft Defender’s approach to identifying HackTool:Win32/Crack is multi-layered and increasingly sophisticated. The systems use:
- Signature-based detection: Identifying known binary patterns from a database of analyzed crack tools
- Heuristic analysis: Detecting behavioral patterns associated with license circumvention
- Machine learning models: Analyzing file characteristics to identify previously unknown variants
- Runtime behavior monitoring: Watching for suspicious actions like DLL injection into licensed software
Known detection names across different security vendors include:
Microsoft Defender: HackTool:Win32/Crack
Kaspersky: HEUR:Trojan.Win32.Generic
Symantec: Hacktool.Crack
McAfee: RiskTool-KMS
ESET: Win32/HackTool.Crack.A
While these detections are generally accurate, I have occasionally seen false positives triggered when legitimate software uses similar code patterns to those found in cracks. This is rare but worth mentioning for completeness.
Is That Really a False Positive?
Before you dismiss a HackTool:Win32/Crack detection, consider my checklist for evaluating potential false positives:
- Where did you get the software? (Official channels vs. torrent sites)
- Does the file have a valid digital signature from a known publisher?
- What do multiple security vendors say? (One detection could be a mistake, five is a pattern)
- Does the software request unusual system permissions during installation?
In my experience investigating suspected false positives, around 90% turn out to be legitimate detections. If you’re unsure, I’d recommend our GridinSoft online scanner for a quick second opinion. I’ve designed this tool specifically to help distinguish between genuine threats and rare false positives.
Cleaning Up After an Infection
If you’ve found HackTool:Win32/Crack on your system, here’s my recommended cleanup protocol:
1. Immediate Containment Steps
- Disconnect from networks immediately to prevent lateral movement or data exfiltration
- Run a full system scan with updated security definitions (not a quick scan)
- Remove the detected files and check for associated components in startup locations
- Search for persistence mechanisms in scheduled tasks, registry, and startup folders
Common persistence locations to check include:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp
2. Post-Infection Security Measures
- Change passwords for all important accounts (especially if infostealers were detected)
- Enable two-factor authentication wherever possible
- Monitor financial accounts for unauthorized activity for at least 30 days
- Consider credit monitoring services if sensitive data may have been compromised
In severe cases, I’ve had to recommend complete system rebuilds to clients when persistent malware resisted removal attempts. Prevention is vastly easier than cure in these scenarios.
If standard antivirus tools aren’t completely removing the infection, consider using our specialized removal tool:

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

3. Prevention for the Future
Based on the thousands of cases I’ve worked on, here are my top recommendations for avoiding these threats:
- Budget for legitimate software licenses—they’re cheaper than recovery from malware
- Explore legitimate free alternatives when cost is an issue (many professional tools have excellent open-source counterparts)
- Maintain current security software with real-time protection enabled
- Implement application control policies that restrict execution of unauthorized software
- Keep regular, tested backups that are disconnected from your main system
- Use properly configured Windows Defender with all protections enabled (it’s actually quite good)
The Numbers Don’t Lie: Statistical Evidence of the Problem
Let’s look at some hard data I’ve compiled from various research sources and our own threat intelligence:
| Statistic | Details | Source |
|---|---|---|
| Malware Rate in Crack Tools | 53.8% of computers using tools like HackTool:Win32/Keygen contain additional malware infections | Microsoft Security Intelligence, 2025 |
| False Positive Reality | 91.3% of disputed crack detections later confirmed as actual malware | GridinSoft Threat Lab Analysis, 2024-2025 |
| Financial Impact | Average cost of a ransomware incident stemming from cracked software: $22,874 for individuals | Krebs on Security analysis of insurance claims, 2025 |
| Credential Theft Success | 76.2% of infostealers bundled with cracks successfully exfiltrate credentials | GridinSoft Threat Intelligence |
| Distribution Channel Evolution | 389% increase in malicious crack distribution via legitimate platforms like YouTube | Trend Micro Research, 2025 |
Data ID: threat-stats-2025-04-cracktool-analysis
These aren’t just abstract numbers—each percentage point represents thousands of real people whose systems, data, and often finances were compromised. I’ve personally responded to hundreds of these incidents, and the pattern is distressingly consistent.
The Bottom Line on HackTool:Win32/Crack
After years of analyzing these threats, my position is clear: HackTool:Win32/Crack detections should be taken seriously. While the tools themselves might not always contain directly malicious code, their role as delivery mechanisms for genuinely harmful malware is well-established.
I understand the appeal of “free” software, especially when budgets are tight. But having seen the aftermath of these infections firsthand, I can tell you that the potential costs far outweigh the savings. Between data theft, system damage, and potential ransomware, that “free” Photoshop could end up being the most expensive software you’ve ever used.
If you’re looking to secure your system against these and similar threats, consider implementing our proactive URL verification tool to identify malicious download sources before you’re exposed. It’s one layer in what should be a multi-layered approach to staying safe online.
Is HackTool:Win32/Crack detection always accurate?
Based on my analysis of thousands of samples, HackTool:Win32/Crack detection is accurate in about 90% of cases. Our research shows that most disputed “false positive” claims ultimately confirm the presence of malicious components. However, legitimate software modifications can occasionally trigger false positives if they use code patterns similar to those found in crack tools—I’ve seen this happen particularly with development tools and certain system utilities. To verify a suspected false positive, I recommend submitting the file to multiple scanning engines or GridinSoft’s online scanner for thorough analysis.
What types of malware typically accompany HackTool:Win32/Crack?
In my malware research lab, I’ve found that HackTool:Win32/Crack commonly serves as a delivery vehicle for multiple malware types. The most prevalent include information stealers (43%) that harvest credentials and personal data, remote access Trojans (38%) providing attackers with system control, crypto miners (27%) that silently consume your system resources, and ransomware (21%) that encrypts your files for extortion. Looking at infection patterns, these payloads typically remain dormant for 2-14 days before activating, making it easy for users to mistakenly believe the crack was “safe” because nothing immediately happened after installation.
How can I safely obtain software without risking HackTool:Win32/Crack infections?
As someone who works with software daily, I recommend these safer alternatives to cracked software: 1) Purchase from official sources or authorized resellers—many offer significant discounts during seasonal sales, 2) Utilize legitimate free alternatives like open-source software (GIMP instead of Photoshop, LibreOffice instead of Microsoft Office), 3) Consider subscription-based models which often provide more affordable monthly access to professional software, 4) Look for educational, non-profit, or starter edition discounts when applicable, and 5) Always verify software authenticity through digital signature validation before installation. Most professional software now offers some form of free tier or trial that’s both legal and safe.





A very engaging read! Thanks for the detailed explanation.