An FBI study guide has been made publicly available as part of a Freedom of Information law request filed by Property of the People, an American non-profit organization that deals with government transparency.
The resulting document contains training tips for agents and explains what kind of data can be obtained from the operators of various messengers and what legal permissions will be required for this.
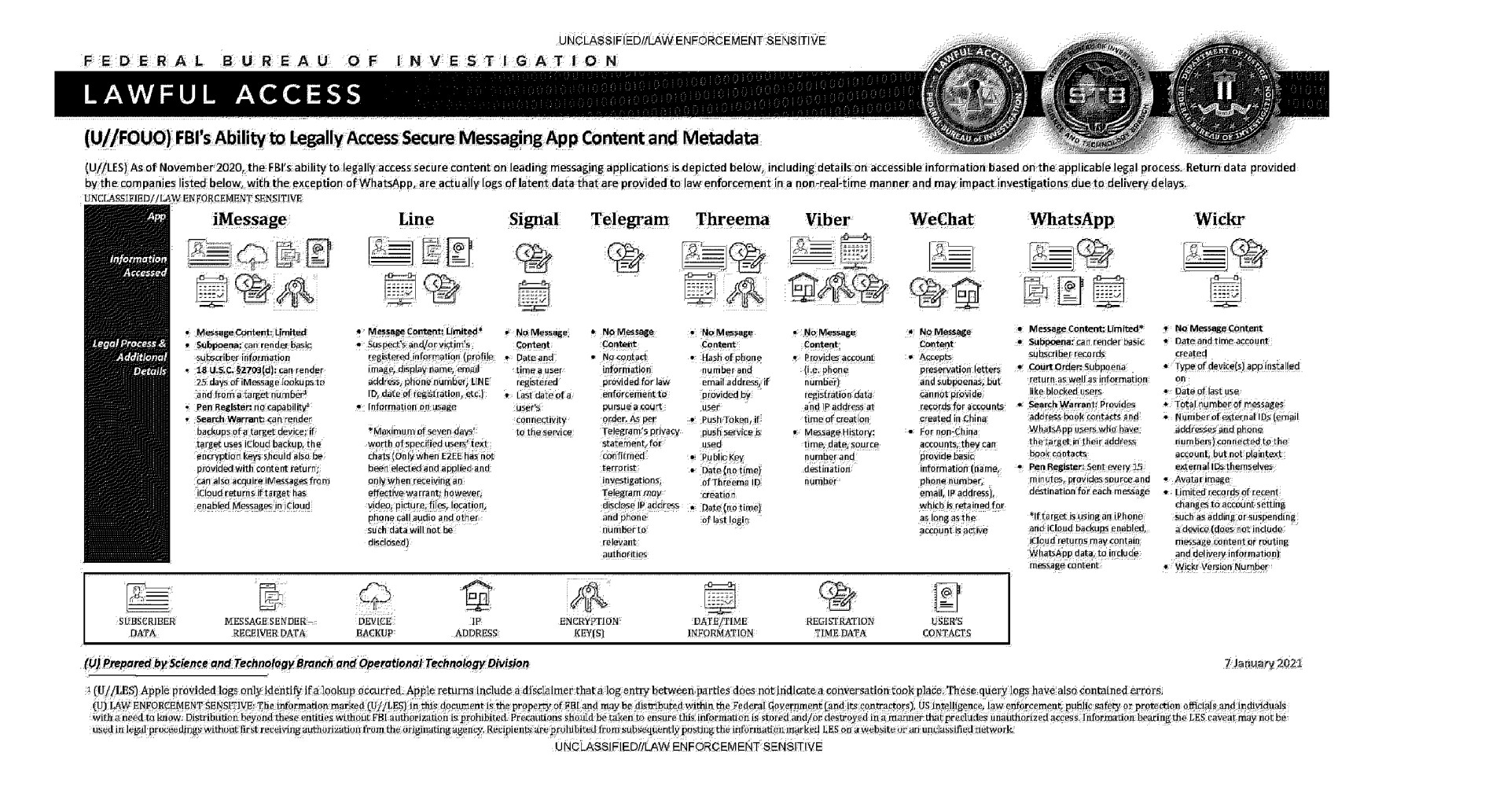
The document is dated January 7, 2021, and, in general, does not contain any fundamentally new information, but it gives a good idea of what information the FBI can currently receive from services such as Message, Line, WhatsApp, Signal, Telegram, Threema, Viber, WeChat and Wickr.
In general, the training document confirms that usually the FBI cannot access the encrypted messages themselves, but they can request other types of information that can also be useful in investigations.
| Application | Legal Permissions and Other Details |
| Apple iMessage | Reading message content is limited. Summons: Help you find out basic information about a subscriber. 18 USC §2703 (d): Helps to identify requests in iMessage 25 days from the specified date. Pen Register: Impossible. Search warrant: helps you get backups from the target device; if the target uses iCloud backups, encryption keys must be provided, and iMessages can also be retrieved from iCloud if the target has activated Messages in iCloud. |
| Line | Reading of message content is limited. Registration data of the suspect and/or victim (profile picture, name, email address, phone number, LINE ID, registration date, etc.). Usage Information. Content of text chats for a maximum of 7 days for specified users (only if end-to-end encryption is not active and not used, and only if a valid warrant is received; however, videos, images, files, location data, voice calls, and other such data will not be disclosed). |
| Signal | The content of messages cannot be read. Date and time of user registration. Last date when the user was connected to the service. |
| Telegram | The content of messages cannot be read. User contact information is not provided to law enforcement to comply with a court order. & nbsp; Telegram may disclose the IP address and number for confirmed terrorist investigations, according to Telegram’s privacy statement phone to the relevant authorities. |
| Threema | The content of messages cannot be read. A hash of the phone number and email address, if provided by the user. Push Token, if using a push service. Public key. Date (no time) when Threema ID was created. Date (no time) of last login. |
| Viber | The content of messages cannot be read. Provided credentials (i.e. phone number), registration data, and IP address at the time of creation. Message history: time, date, source number, and destination number. |
| Content of messages cannot be read. Subpoenas and requests to save accounts are accepted, but data for accounts created in China is not provided. For accounts outside of China, provided basic information (name, phone number, email address, IP address) that is retained as long as the account is active. |
|
| Reading message content is limited. Subpoena: Help you get basic subscriber data. Court order: same as subpoena and information about blocked users. Search Warrant: This lets you get contacts from the target’s address book and find out which WhatsApp users have the target in their address book. Pen register: Transmits source and destination metadata for every post every 15 minutes. If the target is using an iPhone and iCloud backup is enabled, the data from iCloud may contain WhatsApp data, including the content of messages. |
|
| Wickr | The content of messages cannot be read. The date and time the account was created. The type of devices on which the application is installed. Date of last use. Number of messages. The number of external IDs (email addresses and phone numbers) connected to the account, but not the IDs themselves by open test. Avatar. Limited information about recent changes to account settings, including adding or stopping devices (does not include message content or routing and delivery information). Wickr version number. |
Let me remind you that I also reported that FBI removed web shells from vulnerable Microsoft Exchange servers without informing owners.




