Corrupted Word Documents Phishing Attacks Avoid Security Checks
Hackers found a new way of bypassing the email security filters and anti-malware software – corrupted MS Word documents. As usual, they are attached to email messages with lucrative text,…
Skyjem.com
Skyjem.com is a questionable search engine that you may see appearing in the browser for no obvious reason. Its search results are questionable and heavily infused with advertisements and links…
Ledger Recovery Phrase Verification Scam
“Ledger Recovery Phrase Verification” is a scam email that targets non-vigilant users. Its goal is to trick users into writing down their recovery phrase on a fake Ledger website. "Ledger…
Trojan:PDF/Phish.A
Trojan:PDF/Phish.A is detection of a PDF file which potentially carries a malicious link or script designed to harm the system. This embedded malicious script may download additional malware onto the…
CISA Urges to Patch Critical Array Networks Vulnerabilities
The US cybersecurity agency CISA warned about the ongoing exploitation of a critical-severity flaw in Array Networks' secure access gateway products, including the Array AG and vxAG. Chinese hackers are…
Meta Deletes 2 Million Accounts Related to Scams
Meta has intensified its fight against pig butchering scams, removing over 2 million accounts linked to these operations on Facebook and Instagram. Meta has removed these accounts from its platform…
Trojan:PowerShell/Malscript!MSR
Trojan:PowerShell/Malscript!MSR refers to a detection linked to malicious script activity. This type of malware typically exploits the system console interface to download and run full-fledged malicious programs. Let me quickly…
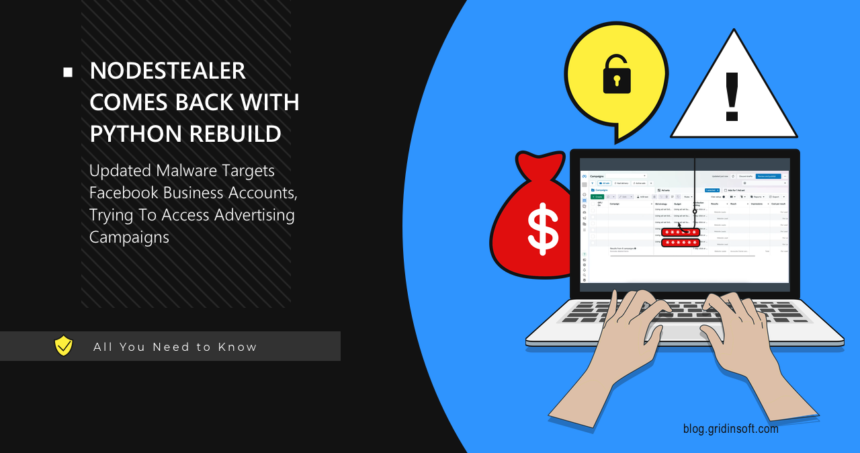
NodeStealer Returns With Python Codebase, More Functions
Researchers have identified an updated version of NodeStealer, now rewritten in Python. This version is capable of extracting additional information from Facebook Ads Manager accounts and credit card details stored…
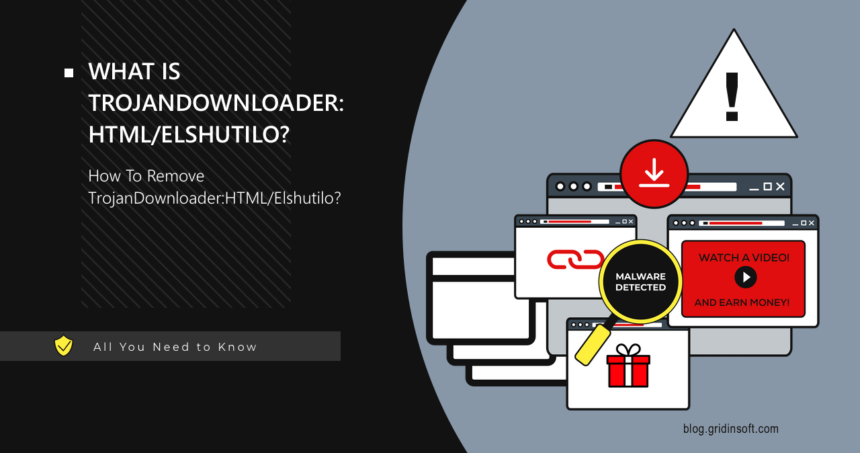
TrojanDownloader:HTML/Elshutilo
TrojanDownloader:HTML/Elshutilo is script-based malware designed to download additional payloads onto the target system. Since detection is based on threat behavior rather than a signature, it can sometimes result in false…
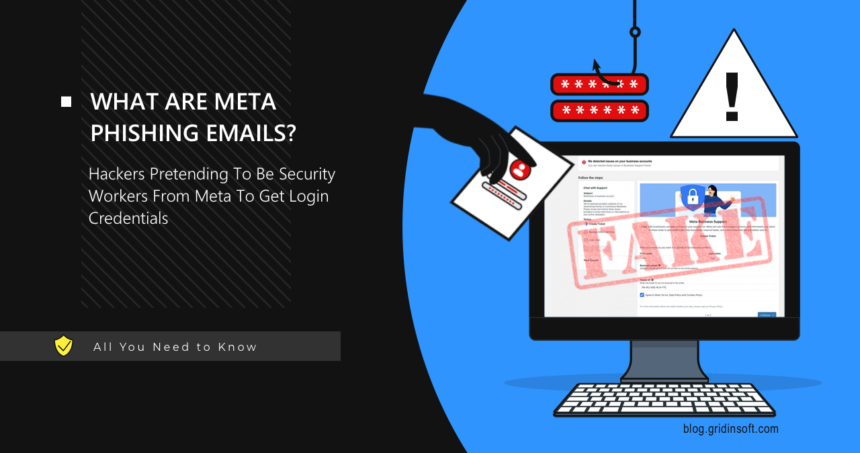
Meta Security Email Phishing Scams Explained
Attackers are targeting users of Meta services with phishing attacks. Classic fraud schemes are gaining momentum once again, with users risking their accounts and all the data present within them.…
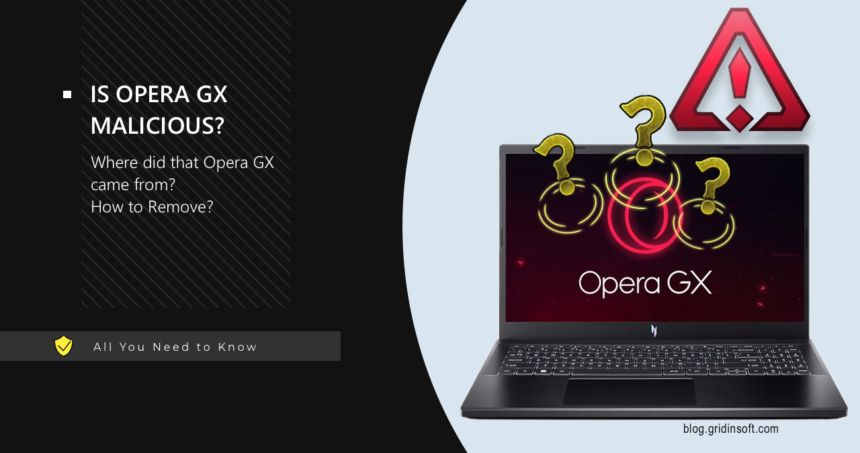
Opera GX
Opera GX is a special version of the Opera browser with extra features tailored for gamers. However, malicious, weaponized versions of the browser are circulating online, transforming this legitimate browser…
GitLab Fixes Critical Kubernetes Agent Takeover Vulnerability
GitLab has released another update that fixes varying degrees of vulnerabilities. Users are advised to apply the updates as soon as possible, as one of the flaws is rated as…