Hackers are increasingly using open source tools for attacks
Speaking at the Virus Bulletin conference, Intezer Labs analysts said that hackers are increasingly using open source tools for attacks, and listed freely available tools that hackers majorly abuse. Such…
Attackers can use Windows Update client to execute malicious code
Hackers can exploit Windows Update client to execute malicious code on the system as part of the Living off the Land (LotL) method. The Windows Server Update Services (WSUS)/Windows Update…
Five Eyes Alliance, India and Japan Call for Backdoors in Software
Countries participating in the Five Eyes Alliance (which brings together intelligence agencies in Australia, Canada, New Zealand, the United States and the United Kingdom), as well as India and Japan,…
MalLocker ransomware easily tricks Russians, pretending to be a screen lock from the police
Microsoft experts talked about the new Android ransomware AndroidOS/MalLocker. (hereinafter simply MalLocker), which easily tricks Russians by pretending to be a screen lock from the police. Android ransomware abuses the…
Cellmate men’s chastity belts are vulnerable to attacks and dangerous for users
Pen Test Partners analysts have studied an extremely unusual device: the Cellmate male chastity belts, manufactured by the Chinese company Qiui. So Cellmate chastity belts turned out to be quite…
Researchers discovered four npm packages that were collecting user data
Sonatype identified four npm packages that collected and sent to their creator's data about user machines, such as IP addresses, computer username, home directory path, processor model, and country and…
US authorities arrested legendary John McAfee for tax avoidance
The US Department of Justice reported that the legendary John McAfee was arrested in Spain. The fact is that the former head of MacAfee is accused of tax avoidance, deliberate…
Google recruits a team of experts to find bugs in Android applications
ZDNet reports that a number of new positions have been added to Google's job list. The fact is that Google appears to be recruiting a team of Android security experts…
Chinese hack group SilentFade defrauded Facebook users for $4,000,000
At the Virus Bulletin 2020 conference, Facebook's security team revealed one of the most complex malware operations it has ever faced. Information security experts told about the Chinese hack group…
IPStorm botnet now attacks Android, macOS and Linux devices
For the first time, Anomali specialists noticed the IPStorm in June 2019, and then it attacked only Windows machines. Now it began to attack devices on Android, macOS and Linux.…
Microsoft estimated that ransomware attacks take less than 45 minutes
Microsoft analysts have prepared a traditional Digital Defense report, in which they talked about the main events and trends in the field of cybersecurity and threat analysis over the past…
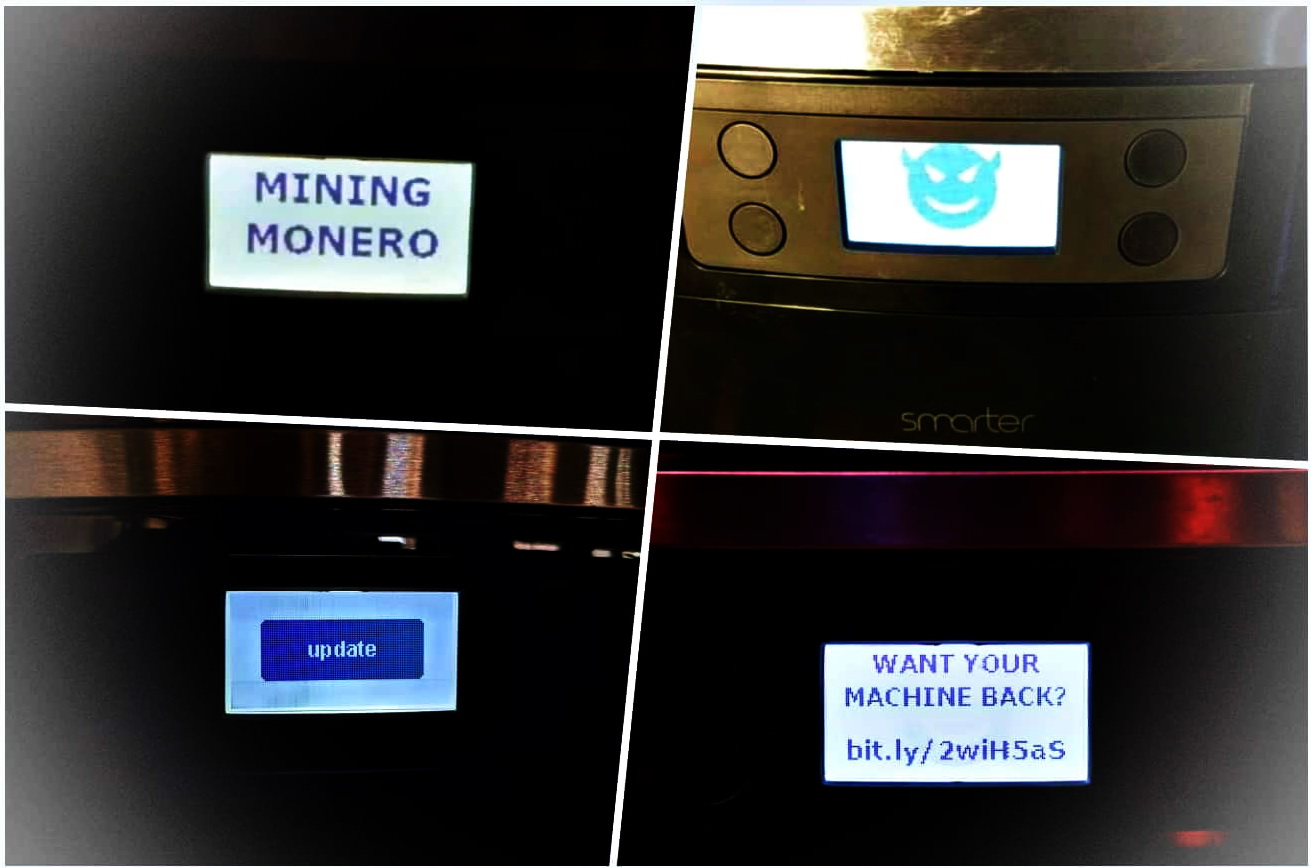
Avast expert taught Smarter Coffee machine to ransom money
Back in 2015, experts from Pen Test Partners talked about a way to hack Wi-Fi networks through the iKettle, created by Smarter, and then discovered that Smarter Coffee maker machine,…