Back in 2015, experts from Pen Test Partners talked about a way to hack Wi-Fi networks through the iKettle, created by Smarter, and then discovered that Smarter Coffee maker machine, created by the same manufacturer, also poses a threat to the safety of users. It even can be taught to ransom money.
Two years after publication of these studies, Smarter released iKettle version 3 and Coffee Maker version 2. The updated products used a new chipset that was not affected by the problems found by Pen Test Partners, although the company’s experts emphasized that Smarter had not accepted the previously found vulnerabilities CVE IDs and did not alert customers of problems.
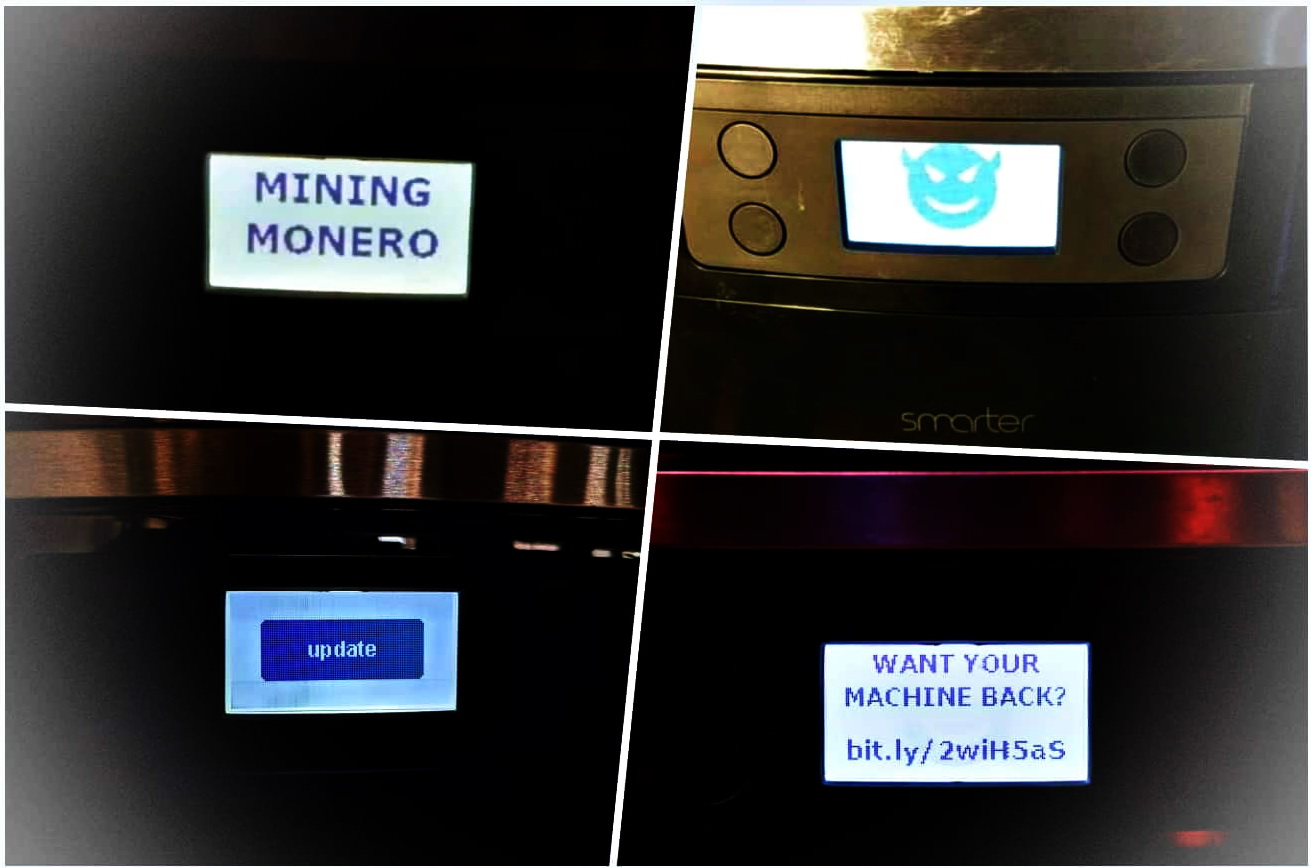
Now Avast specialist Martin Hron decided to study Smarter products. In a huge article that Chron devoted to hacking into a coffee maker machine, he tells how he managed to turn on the heating and water supply, activate the coffee grinder, and even display a message demanding ransom on the device’s display (all this was accompanied by a continuous squeak of a sound signal) without user’s awareness. Let me note that the expert did all this with one of the company’s old coffee machines, having specially reconstructed it for tests.
“I was asked to prove the myth that the threat to IoT devices lies not only in the fact that they can be accessed through a vulnerable router and the Internet, but also in the fact that the device itself is vulnerable and can be compromised without penetrating the network and without hacking the router. It is possible. And I did this to demonstrate that this can happen with other devices from the Internet of Things”, — says the researcher.
So, almost immediately, the expert found out that after turning on the coffee machine works as a Wi-Fi access point, using an unsecured connection to communicate with a smartphone and a special application.
This application, in turn, is used to configure the device and allows connecting it to home Wi-Fi network. In the absence of encryption, the researcher had no problems studying how exactly the smartphone controls the coffee machine. Since there was no authentication either, a fake application could also be used for this purpose.
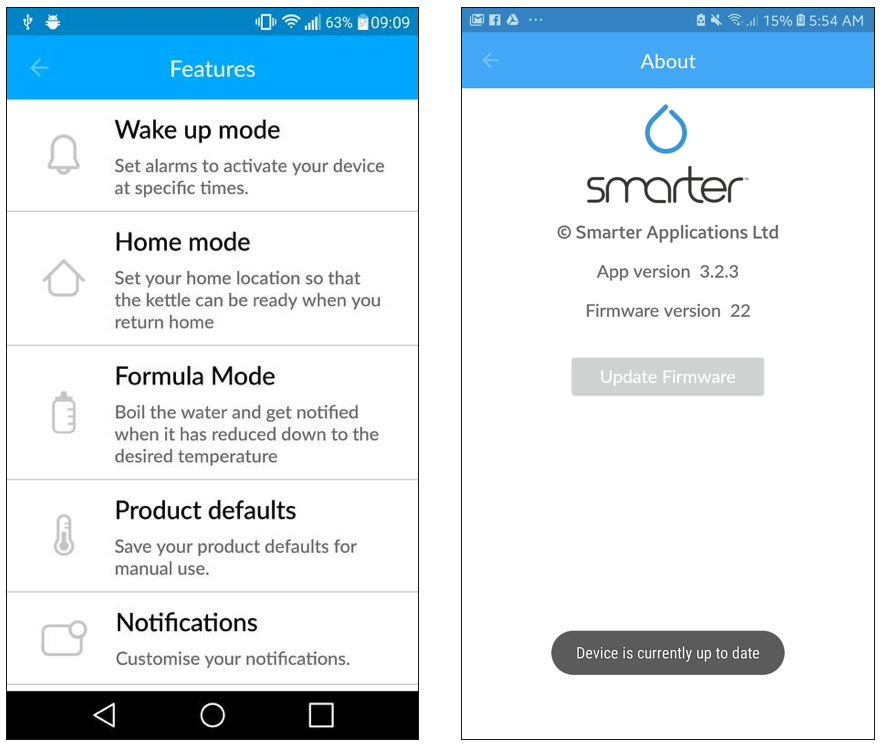
However, it was not possible to find anything dangerous in the application, and then Chron went on to research the mechanism that the coffee machine uses to receive firmware updates. It turned out that device also receives them through a smartphone, and also without encryption, authentication and code signing.
Since the latest firmware version was stored inside the Android application, the expert was able to transfer it to a computer and reverse it using IDA. Almost immediately, he found readable lines and concluded that there was no encryption here either.
Exited with the idea of creating malicious firmware for Smarter, Hron was forced to disassemble the device and find out what hardware it uses.
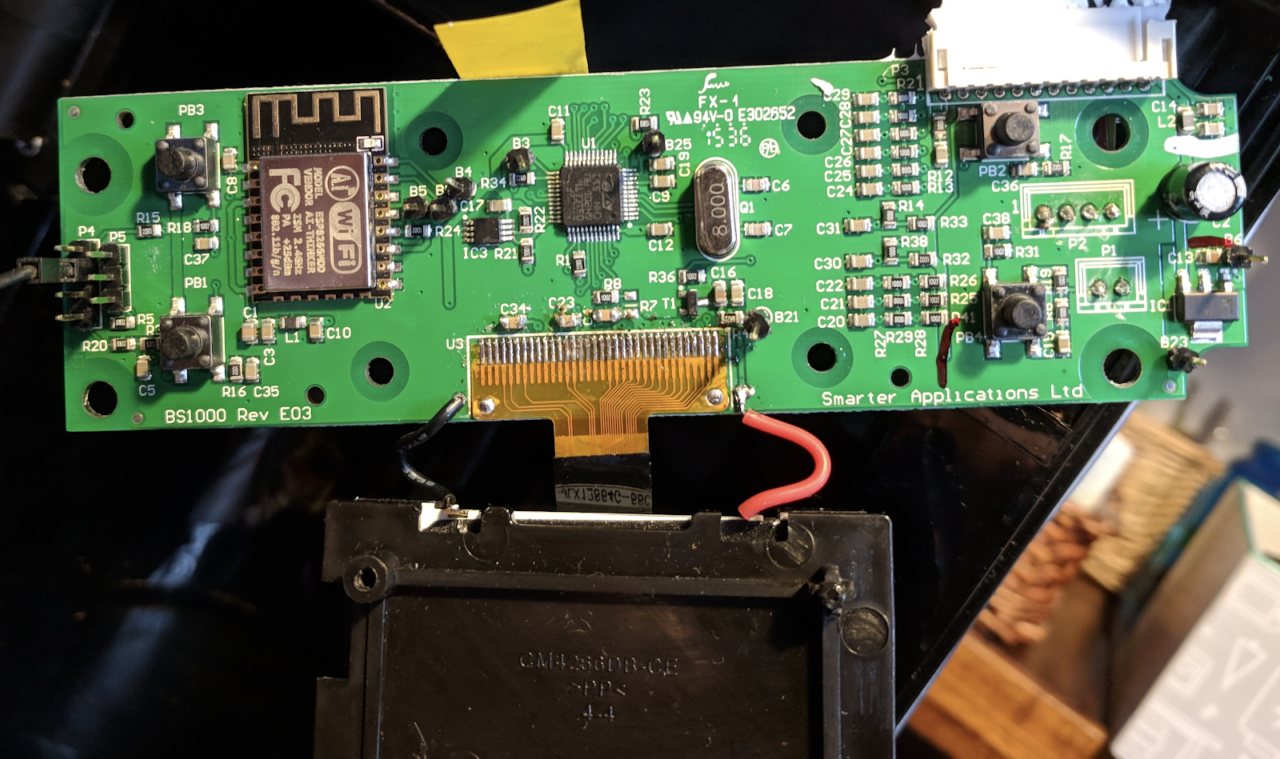
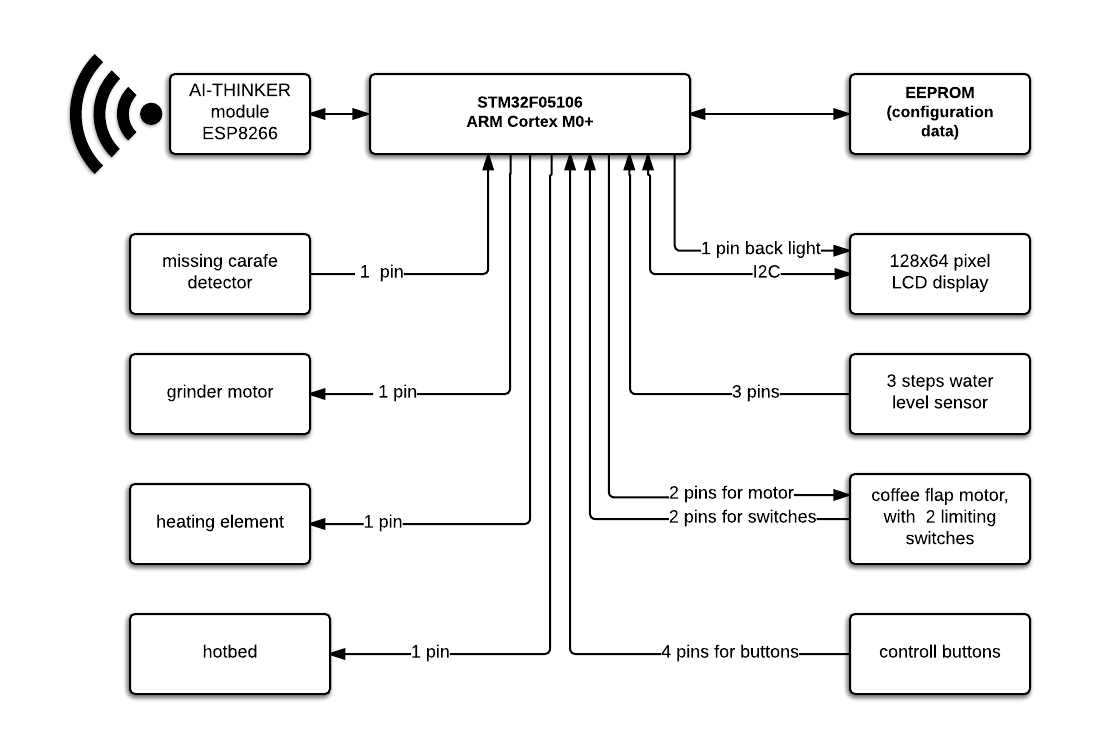
Having dealt with the hardware, Hron moved on to studying the firmware itself and was able to highlight the most important functions for hacking, for example, checking whether the coffee pot is on a heating element, or finding a way to make the device emit a sound signal. Most importantly, the researcher figured out how to force the device to install a malicious update.
In the end, Hron got enough information to write a Python script that mimics the update process. After actually testing a slightly modified version of the firmware, he found that it worked fine.
Initially, the expert wanted to force the device to mine the Monero cryptocurrency, but this would be extremely inefficient and almost make no sense, given the processor and Smarter architecture. Therefore, in the end, he decided to stop at a ransomware modification of the firmware, which would require a ransom, so that the device stopped behaving as shown in the video above.
“A ransomware attack is the least an attacker can do. So, if a hacker puts in more effort, he can force the coffee maker (and probably other devices from Smarter) to attack the router, computers or other devices connected to the same network”, – said Martin Hron.
Fortunately, due to a number of limitations, such an attack is unlikely to pose an immediate threat to real users, but rather an interesting experiment.
Chron notes that bypassing these restrictions will allow hacking the Wi-Fi router, which can be used as a springboard for an attack on the coffee machine. Such an attack can already be performed remotely, but if an attacker compromised a router, then a faulty coffee machine is unlikely to be exactly what the owner of a compromised network should worry about.
Overall, Avast employees usually do not seem to be approaching the “rising of the machines” – we recently wrote that Avast experts accidentally got source code for GhostDNS exploit.