Perfect encryption system presented by team of scientists from three countries
An international team of scientists from the University of St. Andrews (Scotland),…
MyKingz botnet uses Taylor Swift photo to infect target machines
Sophos researchers noticed that the MyKingz botnet, also known as Smominru, DarkCloud,…
Password meter services put Internet users at risk
Password meter services, implemented on many popular platforms, can be misleading, thereby…
Check Point named the most dangerous malware of November 2019
Check Point Research Team, Check Point® Software Technologies Ltd. (NASDAQ: CHKP), a…
France are looking for LockerGoga ransomware developers in Ukraine
French law enforcement agencies are looking in Ukraine for developers who used…
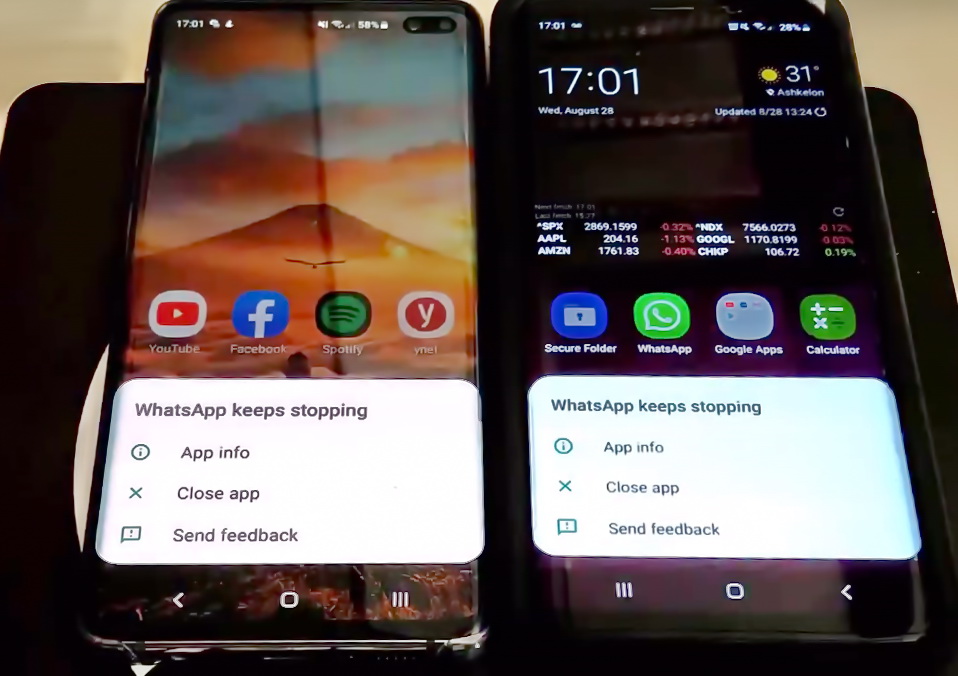
An attacker in a WhatsApp group chat could disable messengers of other participants
Do you like chatting in groups of interest? Are you smiling or…