TrojanProxy:Win32/Acapaladat.B
TrojanProxy:Win32/Acapaladat.B is a type of malware that hides in free, unauthorized VPN…
OneStart Browser
OneStart is a rogue program that is presented as a Chromium-based browser…
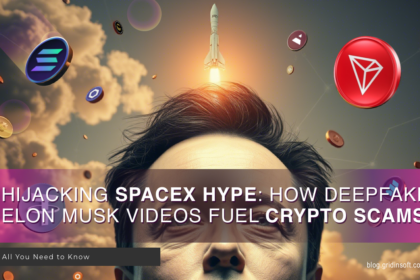
SpaceX Rocket Launch Scam
SpaceX Rocket Launch scam is a series of recurring malignant campaigns that…
VMWare ESXi Vulnerabilities Exploited, Patch Now
Broadcom has published a report on the discovery of three critical vulnerabilities…
Fox Ransomware
Fox Ransomware is believed to be a variant of the Dharma family,…
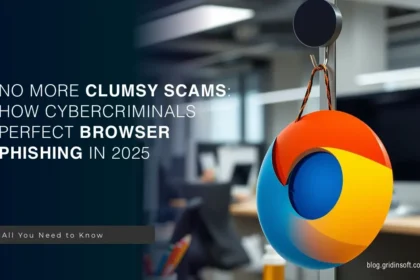
Phishing Links in Browser
Phishing links may lurk wherever you go on the Internet: in your…
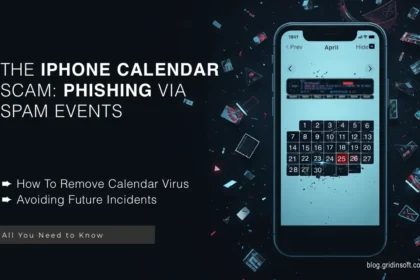
Calendar Virus on iPhone
Calendar virus on iPhone is a phenomenon where attackers misuse features of…
Roblox Robux Generator Scams
Scammers use Robux Generator as a lure to trick the target audience…
Frauds Promote Trading Scam With AI Bots in YouTube Ads
Attackers use AI-generated videos featuring credible crypto experts to create YouTube videos…
Lucky Ransomware (MedusaLocker)
Lucky ransomware is a variant of the MedusaLocker Ransomware family that has…
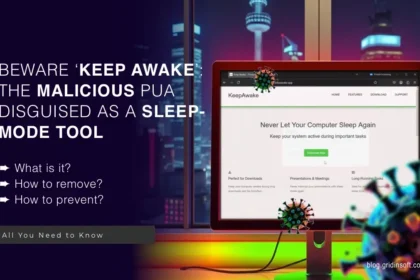
Removing Unwanted “Keep Awake” Application: A Comprehensive Guide
"Keep Awake" is an application that, on the surface, seems designed to…
CipherLocker Ransomware
CipherLocker is yet another malware variant that encrypts user data and demands…