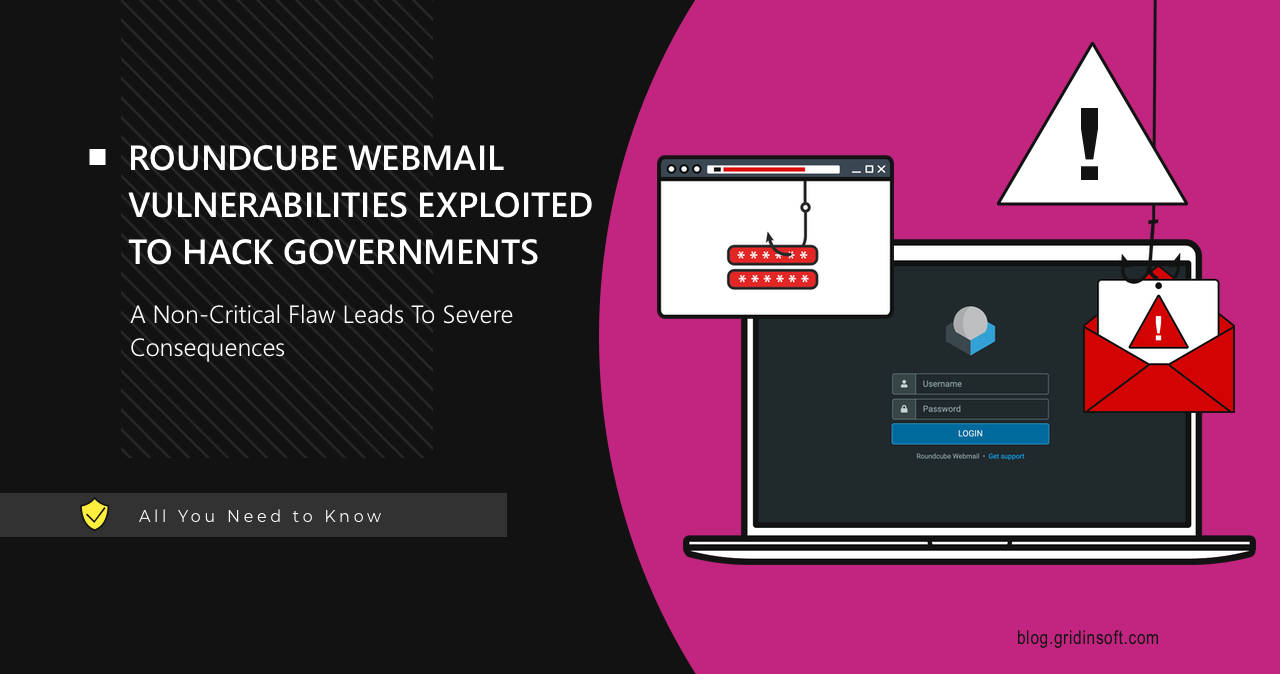
Vulnerability in Roundcube Webmail service appears to be exploited in real-world attacks. The flaw that falls under designation of stored XSS vulnerability allows hackers to target government agencies of ex-USSR countries that use this software solution. Researchers uncovered the nature of the attack, but it is difficult to guess who stands behind them.
Hackers Target ex-USSR Countries with Roundcube Webmail Vulnerability
Cybersecurity researchers reported that they detected an attempt to exploit a vulnerability in the Roundcube Webmail client in the wild. The vulnerability in question is CVE-2024-37383, with a relatively low CVSS rating of 6.1. It was used in a phishing attack against CIS government organizations in June 2024. Researchers discovered a malicious email in one of these organizations that contained a hidden attachment that was not displayed in the email client. The attack was aimed at stealing credentials and email communications through exploitation of an XSS vulnerability in Roundcube.
Roundcube Webmail is an open source email client written in PHP. It allows users to access their email accounts through the browser without the need to install additional apps. Actually, due to this fact, it is quite popular among commercial and governmental organizations and often attracts the interest of attackers.
Roundcube Webmail Vulnerability Exploitation
Vulnerability CVE-2024-37383 is a type of stored cross-site scripting (XSS) vulnerability and allows an attacker to execute JavaScript code on the victim’s end. The vulnerability affects versions of Roundcube Webmail 1.5.6 and below, as well as versions 1.6-1.6.6. In brief, the problem happens during processing the ‘href’ attribute of SVG elements.
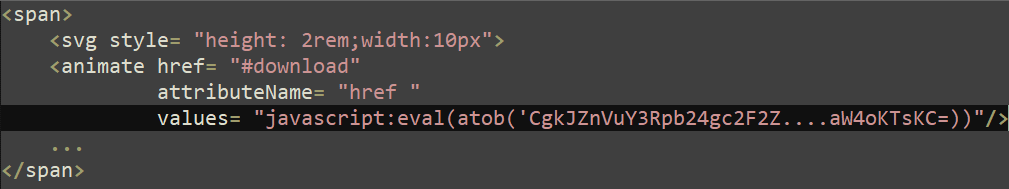
Before displaying the mail message, while processing SVG elements with the attribute animate, Roundcube excluded elements containing the name of the attribute “href”. But because of the extra space, the function responsible for checking the attribute did not exclude the elements. As a result, the extra space in the attribute name allowed these elements to remain on the page and inject arbitrary JavaScript code as a value for ‘href’ and activate it when the email was opened.
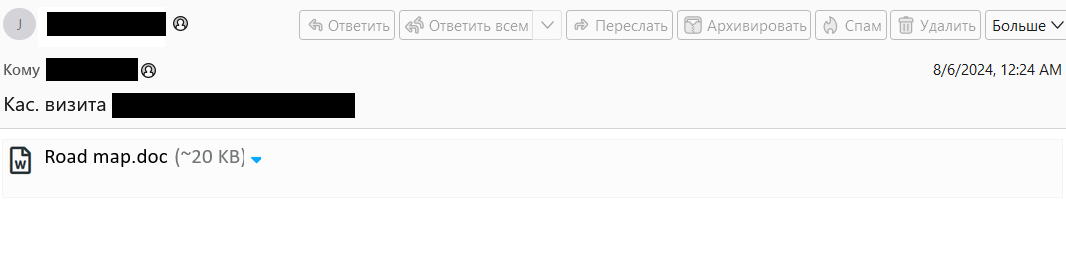
The sample attack included an email with a malicious script that used the eval(atob(…)) function to run encoded JavaScript code. The malicious email activated the download of an empty ‘road map.docx’ document, and in parallel, an attempt was made to exfiltrate messages from the mail server via the ManageSieve plugin. Additionally, the page displayed a fake login form that mimicked the Roundcube interface. This page requested a login and password, which were then eventually sent to the attacker to a remote server at libcdn[.]org hosted by Cloudflare. Despite a fairly extensive analysis, and previous incidents where groups such as APT28, Winter Vivern and TAG-70 have been implicated in attacks on Roundcube, experts were unable to find a link between this attack and any of the known APTs.
Mitigation and Fixes
Despite fixing the vulnerability in versions 1.5.7 and 1.6.7, which were released in May 2024, it appears that not all organizations updated their systems in a timely manner, leaving systems vulnerable to such attacks. In addition, even with updates to the above versions, the XSS vulnerability persisted. Fortunately, an updated version 1.6.9 is currently available, in which this flaw has been completely eliminated. So users and organizations are strongly recommended to upgrade to version 1.6.9.