Experts from Yuga Labs discovered vulnerabilities in mobile applications for Hyundai and Genesis vehicles.
In addition, the SiriusXM smart car platform, used in cars from other manufacturers (Acura, BMW, Honda, Infiniti, Jaguar, Land Rover, Lexus, Nissan, Subaru and Toyota), allowed to remotely unlock the car, start the engine and perform other actions.
Let me remind you that we also wrote that Ferrari Has So Far Denied If It Attacked by Ransomware, and also that Teen gets remote access to 25 Tesla cars.
Also the media reported that Bug in Honda cars allows remotely unlock and start a car.
Yuga Labs specialist Sam Curry has posted two long threads on Twitter (Hyundai, SiriusXM) about problems he and his colleagues have recently discovered in the software of many different vehicles.
The analysis began with applications for Hyundai and Genesis vehicles (MyHyundai and MyGenesis), which allow authenticated users to remotely start and stop the engine, and lock and unlock their vehicles.
By intercepting and studying the traffic generated by these applications, the researchers were able to extract API calls from it. They discovered that the validation of the car owner is based only on his email address, which is simply included in the body of the JSON POST requests. Then it turned out that MyHyundai, moreover, does not require confirmation of the email address during registration.
Based on the collected data, the experts created a new account using the target’s email address with an additional control character at the end. After that, they sent an HTTP request to the Hyundai endpoint. The request contained the experts’ email in the JSON token and the victim’s address in the JSON body, which allowed the validation to be bypassed.
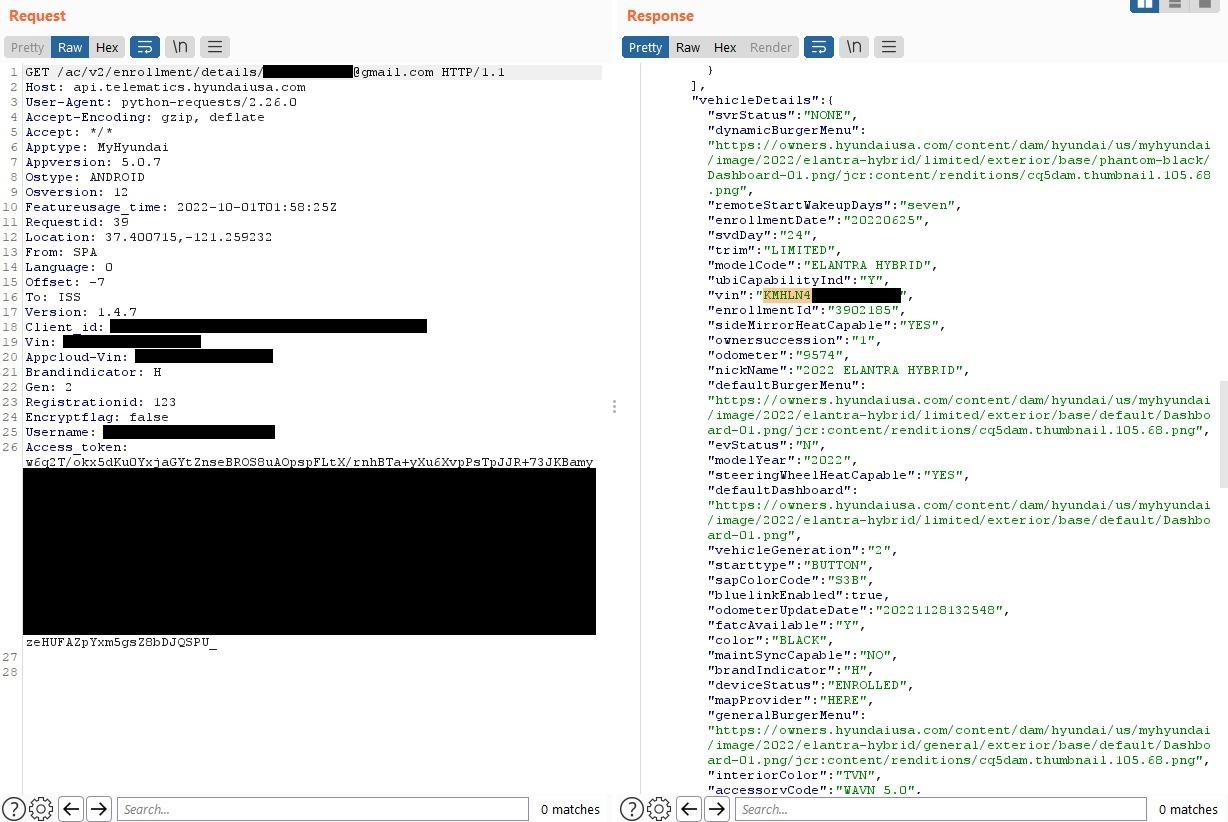
To test their attack, the researchers tried to unlock the Hyundai car they had in their possession. The attack worked and the car was successfully unlocked. After that, a Python script was created to automate all stages of the attack, for which you only need to specify the victim’s email address. You can see the script in action in the video below.

The Yuga Labs analysts then switched to studying the products of SiriusXM, which, among other things, is a provider of telematics services for more than 15 major automakers. The company claims to operate services for approximately 12 million connected cars.Как выяснили эксперты, мобильные приложения Acura, BMW, Honda, Hyundai, Infiniti, Jaguar, Land Rover, Lexus, Nissan, Subaru и Toyota используют SiriusXM для реализации функций удаленного управления автомобилем.
Examining network traffic from the Nissan app showed that it was possible to send fake HTTP requests to an endpoint knowing only the VIN number of a particular car. The response to such a request contains the victim’s name, phone number, address, and vehicle details. In addition to disclosing data, such requests could also contain commands to perform actions with the car. So, for cars manufactured after 2015, it was possible: remote start and stop, blocking, unlocking, headlight and horn control.
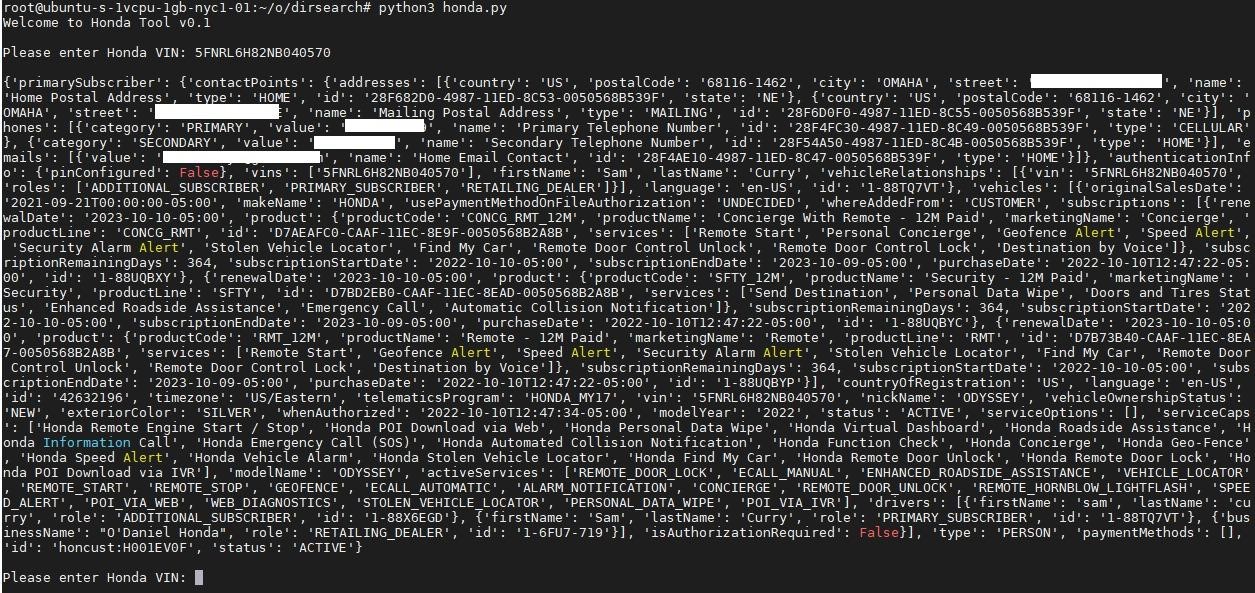
At the same time, experts emphasize that the VIN of almost any car can be found right in the parking lot (usually located at the bottom of the windshield) or on a specialized car sales website.
Hyundai representatives have already told the media that the vulnerabilities discovered by Yuga Labs were not used to attack car owners, and “customer accounts were not accessible to third parties.”
SiriusXM developers also stated that the bugs found by specialists did not affect any client and were eliminated 24 hours after receiving the report. In addition, the company reported that the vulnerabilities were closed as part of a bug bounty program that SiriusXM has had for a long time.




