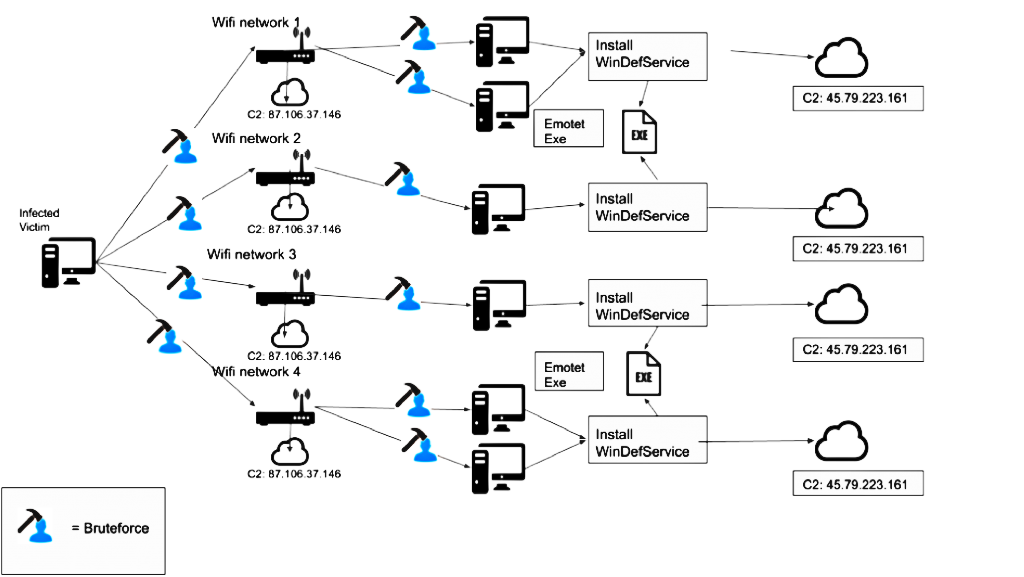
Binary Defense analysts noticed that the new version of the Emotet Trojan behaves like a Wi-Fi worm, as it tries to spread and infect new victims through Wi-Fi networks available nearby.
Researchers say that to detect the nearest Wi-Fi networks, the malware uses wlanAPI.dll on an already infected machine. Having discovered an available network, Emotet tries to brute force the credentials in order to access it. If an attempt is successful, the malware searches on the new network for any Windows machines that can also be infected.
“All accounts on such potentially accessible devices are scanned, and the malware tries to penetrate into the administrator and other user accounts with brute force. If the hack is successful, Emotet delivers a payload to the machine in the form of a service.exe file and creates a Windows Defender System Service for secure establishing in the system”, – report experts of Binary Defense.
To infect other devices via Wi-Fi, the Trojan, among other things, uses the worm.exe binary, the studied sample of which is dated April 2018. It contained the hard-coded IP address of the management server previously seen in connection with Emotet. Experts suggest that malware used Wi-Fi distribution and went unnoticed for almost two years.
Researchers believe that this may be partially explained by the fact that this binary is rarely used. Therefore, specialists for the first time discovered it on January 23, 2020, although Binary Defense closely watched the actions of Emotet from August 2019, when the malware restored activity after the break.
“It is likely that the worm component is not used at all if the malware knows that it is dealing with a virtual machine or working in a sandbox”, – say Binary Defense engineers.
Another executable file that uses trojan for distribution via Wi-Fi is service.exe. It also has a curious feature: although it uses port 443 Transport Layer Security (TLS) to communicate with the management server, in fact, the connection occurs through unencrypted HTTP.
Analysts at Binary Defense recommend the use of strong passwords to protect wireless networks so that an Emotet-like malware could not easily penetrate the network.
Emotet is one of the most active trojans currently distributed via email spam through malicious Word documents. Such letters can be masked as invoices, invoices, account security warnings, party invitations, and even information on the spread of the coronavirus.
Overall, hackers are closely monitoring global trends and constantly improving their bait letters.
Any.Run, an interactive service for automated malware analysis, has compiled a list of the 10 most common threats downloaded to this platform. The Trojan Emotet topped this 2019 threat rating.
Having penetrated the victim’s system, Emotet uses the infected machine for further spamming and also installs additional malware on the device. Often this is the Trickbot banker (which steals credentials, cookies, browser history, SSH keys, and so on), as well as Ryuk ransomware.




