The Security Blog From Gridinsoft
New stealthy “Beep” malware focuses heavily on evading detection
Cybercriminals periodically develop something new. Sometimes it is an updated version of already known malware, and sometimes it is something…
LastPass Breach Investigation Goes On, Things are Even Worse
LastPass, owned by GoTo (formerly LogMeIn) and with over 30 million users, revealed new details about the cyber incidents that…
YouTube Video Causes Pixel Smartphones to Reboot
Users have found that Pixel smartphones powered by Google Tensor processors are rebooting when user is trying to watch a…
The Researcher Hacked His Own Bank Account by Imitating a Voice with AI
The journalist Vice Motherboard Joseph Cox hacked the bank account by imitating a voice with the help of AI, which…
Nearly 50% of Cybersecurity Leaders Will Change Jobs by 2025
According to a new report from Gartner, by 2025, nearly 50% of cybersecurity leaders will change jobs, and 25% will…
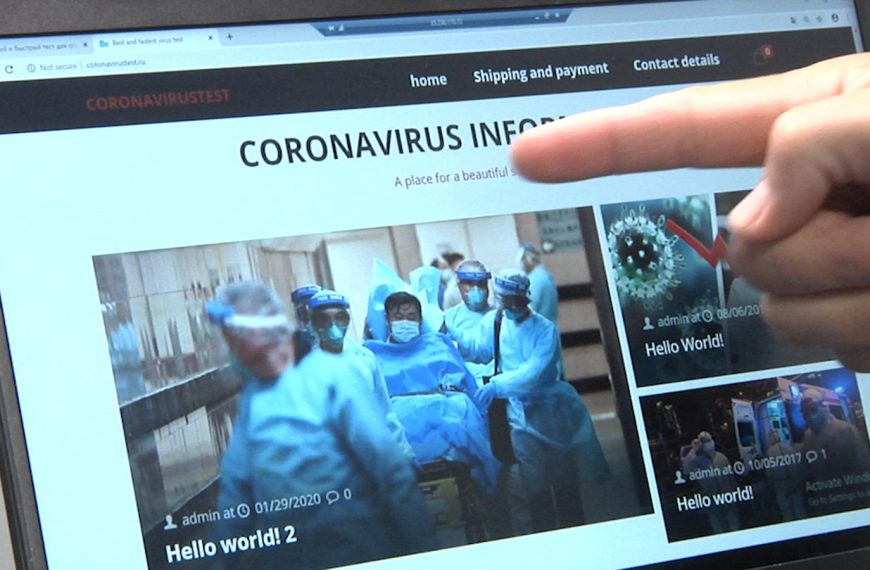
Hackers spoof DNS settings to distribute fake coronavirus applications
Journalists from Bleeping Computer investigated that hackers are replacing DNS…
Published exploit for Kr00k Wi-Fi vulnerability
In February 2020, information security specialists spoke at the RSA…
Cybercriminals fake letters from WHO to distribute HawkEye and trick money into fight with COVID-19
Specialists from IBM X-Force discovered a new malicious campaign, in…
Firefox Refuses to Support FTP Protocol
ZDNet reports that Mozilla developers consider FTP to be an…
Ransomware attacks most often occur at night and on weekends
According to a report published by the American company FireEye,…
Snoop attack steals data from Intel processors
Amazon Web Services (AWS) software engineer Pawel Wieczorkiewicz discovered another…
Microsoft stopped RDCMan development due to a bug
Microsoft has stopped development of the Remote Desktop Connection Manager…
Two new malware can steal cookies from Android apps
IS experts discovered two new malware for Android (recognized as…
Modern RAM is still vulnerable to Rowhammer attacks
Recently, I wrote all about the vulnerabilities of Intel and…
Intel processors need hardware fixes due to new LVI attack
Security experts discovered a new attack on Intel processors called…
Information security experts said that AMD processors are vulnerable to two attacks
A joint group of specialists from the National Center for…
More than 40% of Android users are at risk of cyberattacks
According to a study by Which company, more than 40%…