AdaptiveMobile specialists have published a report on new bugs in the 5G protocol, thanks to which it is possible to disable network segments (DoS) and steal user data, including location information.
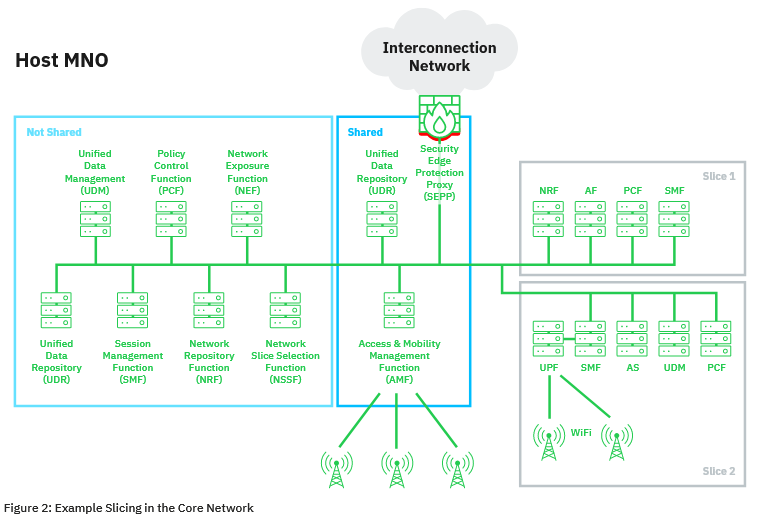
The issues identified are related to the 5G network partitioning mechanism that allows operators to split their infrastructure into smaller blocks dedicated to specific purposes (for example, automotive, healthcare, critical infrastructure and entertainment, and so on).
The discovered vulnerabilities can be exploited in hybrid mobile networks, where 5G is mixed with older technologies. Such options will be found in the real world in the next years, when 5G technology will gradually replace the rest.
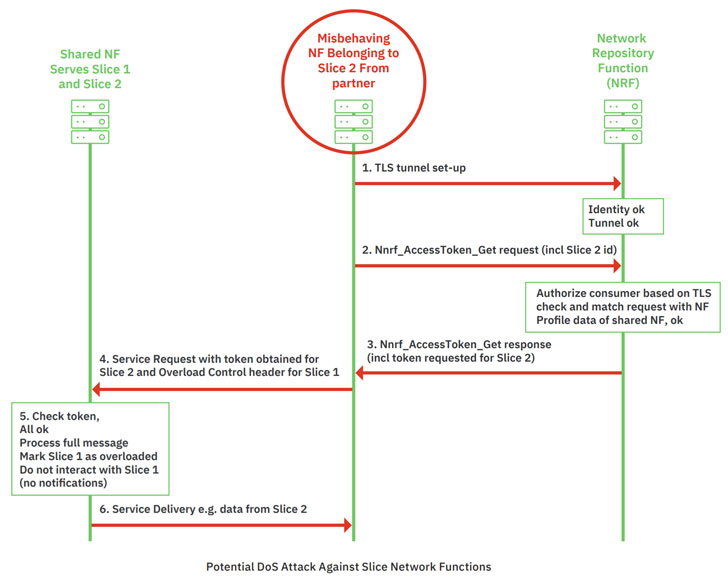
Attacks are possible due to the lack of mapping between application and transport layer identifiers, which allows potential attackers to impersonate legitimate network functions in hybrid 5G networks.
As a result, if an attacker manages to compromise the operator’s peripheral network equipment, he can abuse 5G functions to implement DoS attacks against other network segments or extract information from neighboring network segments, including subscriber data (for example, location data).
The researchers also warn that scenarios are possible when the operator’s partners, who are granted access to network segments, can abuse their privileges to attack other parts of the network.
AdaptiveMobile has already notified the 3GPP consortium (responsible for developing of the 5G standard), the GSMA and the mobile operators industry group about the problems. Experts say that protection against these attacks may require the development of some large features that may be added in Release 17.
Release 17 (or Rel-17) is the version of the 5G standard that is currently in development and should be released in mid-2022.
Let me also remind you that I wrote that Vulnerabilities in old GTP protocol could affect 4G and 5G networks.