Ukrainian cyber police in cooperation with Binance detained operators of 20 cryptocurrency exchangers
Since January 2020, the Ukrainian cyber police began cooperating with one of the world's largest cryptocurrency exchanges, Binance. The fact is that exchange experts often detect transactions that potentially are…
Microsoft developers will stop supporting classic Edge and IE 11
Microsoft said it would stop supporting classic Edge and IE 11. The company has published a schedule for the end of support for Internet Explorer 11 and Edge (a version…
Vulnerabilities in Amazon Alexa opened access to user data for outsiders
In June this year, researchers from Check Point discovered a number of dangerous vulnerabilities that opened for attacks the Amazon Alexa virtual assistant and its users. The problem was in…
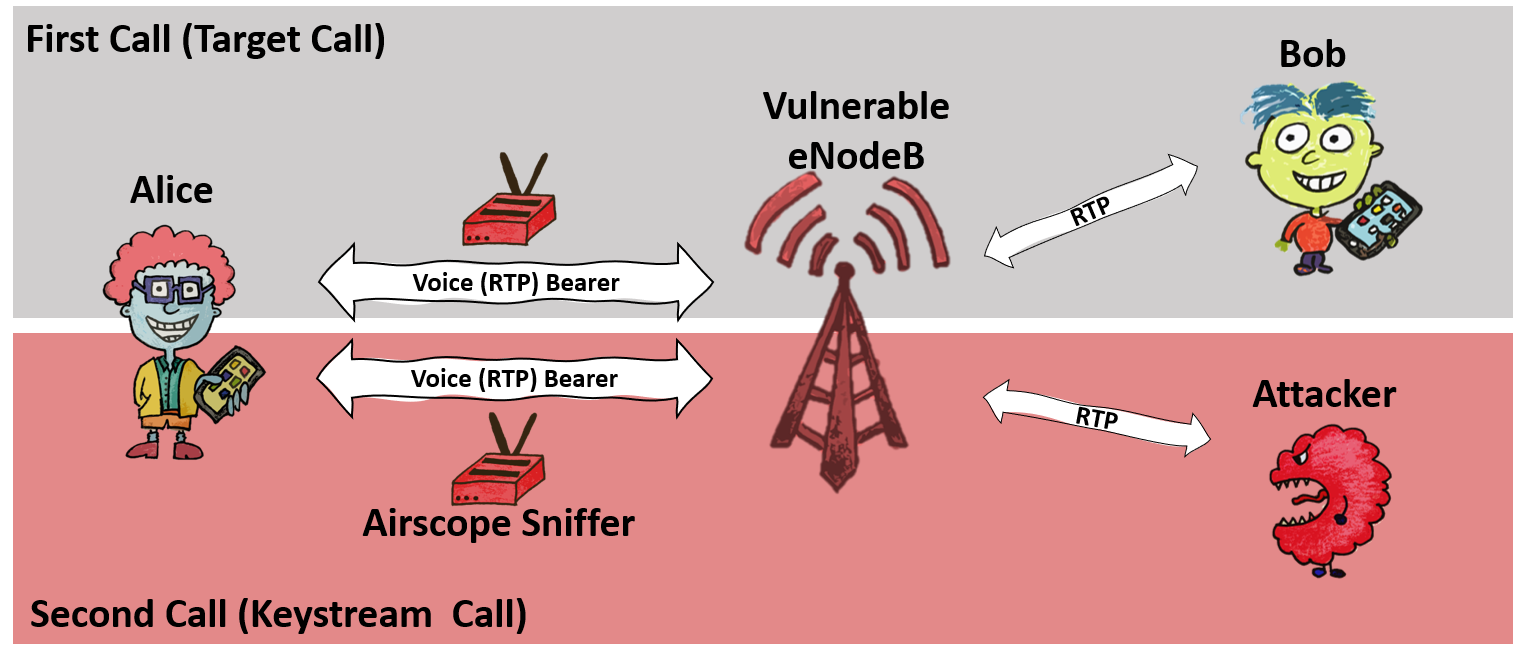
ReVoLTE attack allows overhearing other people’s conversations in LTE networks
Experts from the Ruhr University and New York University in Abu Dhabi have published information about the ReVoLTE attack, which allows decrypting and overhearing other people's conversations on LTE networks.…
Mozilla Downsizing Affects Security Professionals
Earlier this week, Mozilla fired 250 employees, and another 60 employees moved to other teams. The media reports that Mozilla's downsizing has seriously affected security professionals. Mozilla head and Mozilla…
Citrix expects attacks on fresh issues in XenMobile
Citrix engineers released a number of Citrix Endpoint Management patches this week. Citrix expects attacks on XenMobile Server corporate mobile device management systems. These issues give an attacker the ability…
HIBP (Have I Been Pwned?) leak aggregator opens the source code
Founder of Have I Been Pwned? (HIBP) Troy Hunt announced that after a series of unsuccessful attempts to sell the project, about which he talked this spring, he decided to…
Kr00k problem threatens devices with Qualcomm and MediaTek Wi-Fi chips
In early 2020, ESET experts spoke about the Kr00k vulnerability (CVE-2019-15126), which can be used to intercept and decrypt Wi-Fi (WPA2) traffic. Then it was reported that any devices using…
Intel investigates data leak: 20 GB of source codes and documents
Swiss programmer Till Kottmann has been studying various dumps in the public domain for a long time and it looks like he found something interesting, so now the IT giant…
US authorities offered $10000000 for information on planned cyberattacks for the elections
Less than 100 days are left before the start of the US presidential elections, and the US authorities have announced that they are ready to pay $10 000 000 for…
295 Chrome extensions injected ads in search results
AdGuard analysts have identified 295 malicious extensions in the Chrome Web Store that have been installed over 80,000,000 times. These Chrome browser extensions injected ads into Google and Bing search…
Google: 11 0-day vulnerabilities identified in the first half of 2020
Google Project Zero experts estimate that 11 0-day vulnerabilities, actively exploited by hackers, were identified in the first half of 2020. The current number of 0-day problems indicates that, most…