Lennert Wouters, a researcher at the Catholic University of Leuven, who previously discovered a bug that allowed to hijack Tesla in a couple of minutes, said that he hacked the Starlink terminal using a $25 mod chip.
At the Black Hat 2022 conference, Wouters announced that he intends to make this tool available for copying.
Elon Musk has launched more than 3,000 Starlink satellites into orbit since 2018. This satellite network is designed to provide Internet connectivity in the most inaccessible places on Earth, where previously connection was unreliable, expensive or completely unavailable.
Thousands more satellites are planned to be put into orbit as it develops, and Starlink, like any other new technology, became an interest to hackers and researchers.
Now Lennert Wouters has spoken about one of the first hacks of the Starlink terminal, a satellite dish (dubbed the Dishy McFlatface) that is commonly placed on buildings. To gain access to the firmware of the dish, Wouters dismantled the terminal he bought and developed a special tool for hacking it himself.
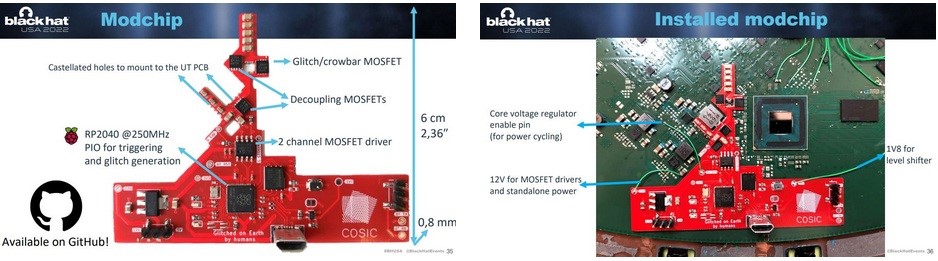
This role was taken over by a custom board (mod-chip) that was assembled from ready-made parts, the total cost of which was approximately $ 25. Once connected to a Starlink dish, the board is used for a fault injection attack, temporarily shutting down the system to bypass Starlink’s defense mechanisms. This “glitch” eventually allowed Wouters to reach the previously blocked portions of the Starlink system.
To create the mod chip, Wouters scanned a Starlink dish and created a board to match the existing Starlink board. Its mod chip needs to be soldered to an existing Starlink board and connected with a few wires.
The mod chip itself consists of a Raspberry Pi microcontroller, flash memory, electronic switches, and a voltage regulator. When creating the board for the user terminal, Starlink engineers printed the inscription “Made on Earth by humans” on it. Wouters’ mod chip says “Glitched on Earth by humans”.
Moreover, the researcher decided to open-source his tool by publishing his work on GitHub, including some of the details needed to launch the attack.
Wired explains that the Starlink system consists of three main parts. The first is the satellites themselves, which move in near-Earth orbit at an altitude of about 550 kilometers and transmit signals to the surface. The satellites communicate with two systems on Earth: gateways that send internet connections to the satellites, and Dishy McFlatface dishes that users can purchase. Wouters’ research centered around user terminals, which were originally round, but new models are rectangular.
Enthusiasts have been studying Starlink user terminals for a long time: they were repeatedly disassembled, discussed on Reddit, but Wouters was the first to pay attention to the security of the terminal and its chips. He says that he went through several stages and tried many different approaches before he created his open source mod chip.
Waters has been testing the Starlink system since May 2021, achieving 268 Mbps download speeds and 49 Mbps download speeds from the roof of his university building. After that, he decided to disassemble the device. Using a combination of “an industrial hair dryer, tools, isopropyl alcohol and a lot of patience,” he was able to remove the lid from the plate and gain access to its internal components. In the end, this helped to understand how the device boots and downloads firmware.
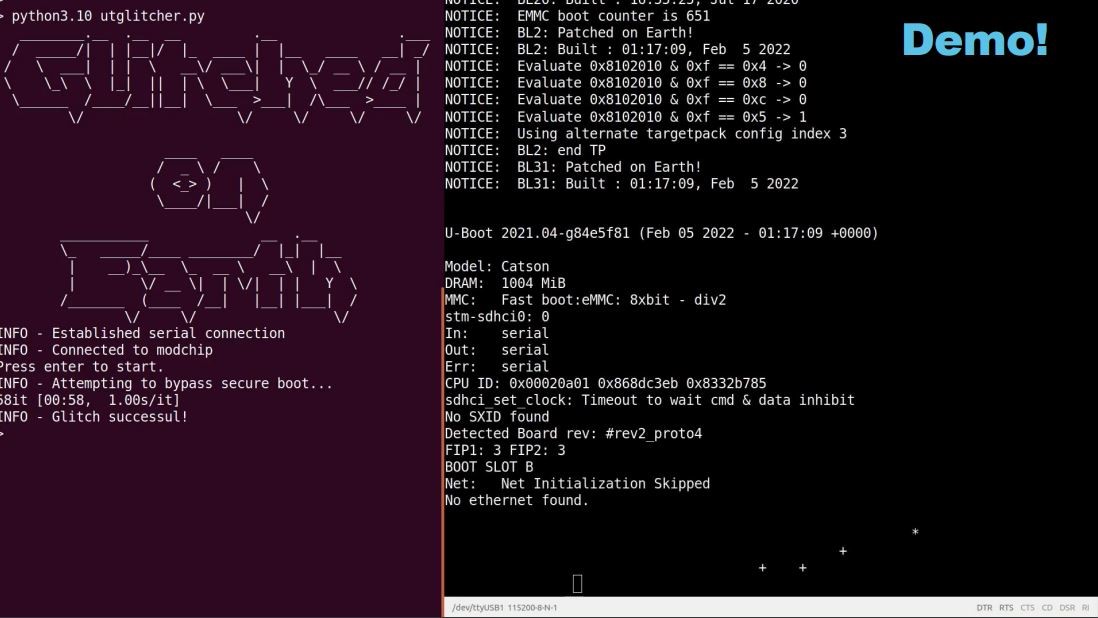
In general, Waters’ attack works by bypassing the security and signature checks needed to make sure the system starts up correctly and the code hasn’t been tampered with.
So, when a Starlink dish turns on, the loader goes through a number of different stages. Wouters’ attack causes a crash in the first bootloader, a ROM bootloader that is flashed into the SoC and cannot be updated. After that, it becomes possible to deploy custom firmware and gain control over the terminal.
The researcher notified Starlink about the vulnerabilities he found last year, and the company paid him a reward under the bug bounty program. Starlink developers even offered Waters an access to the device’s software, but he refused, as he was already deep in work and wanted to finish developing the mod chip.
That being said, Wouters notes that while SpaceX released an update to make the attack more difficult (it changed its mod chip in response), the underlying problem cannot be fixed until the company creates a new version of the main chip. For this reason, all existing user terminals are still vulnerable, although it has become more difficult to carry out an attack.
Although the mod-chip specs are available on GitHub, Wouters says he doesn’t plan to sell off-the-shelf boards, nor will he distribute custom firmware for the user terminal or give exact details of the glitch he was exploiting.
It’s worth noting that after Waters’ Black Hat speech, Starlink engineers released a six-page PDF document explaining exactly how they secure their systems.
Starlink experts emphasize that such an attack requires physical access to the terminal, and as a result of a boot failure, only one specific device can be compromised, but not the entire Starlink network.

